ADVANCED THREAT DEFENSE
Multi-layered Approach to Email Threat Protection90% of business compromises start with an email, defend your users today. Protect Your Entire Company From Phishing, Malware, Spam and Spoofing Utilizing Real-Time Anti-Phishing Feeds.
Protect Your Employees from Malicious Email 24×7
On Any Device
ADVANCED THREAT DEFENSE STOPS EXTERNAL EMAIL THREATS
Spam Filtering
Keep malware, spyware, spam & viruses out.
Phishing Protection
Advanced Threat Defense for email links.
Business Email Compromise
Stop whale phishing and domain name spoofing.
Unsuspecting Employee Emails Are Under Constant Attack
Which unsuspecting employee will unknowingly bring your organization down to its knees?
The Numbers Say It All
Email is the number one vector for sophisticated threats that are targeting your organization. These days its people rather than infrastructure that are the targets.
Attacks including malware, ransomware and phishing are becoming more common and more sophisticated every day.
Its not a matter of IF, but only a matter of when.
You don’t have to play the Number’s Game
Why be the next number on the hacker’s hit-list ?
Protect your entire company from Phishing, Malware, Spam and Spoofing, utilizing real-time anti phishing software feeds.
Our classification engine detects and defends against these threats in real-time with the highest possible level of accuracy.
Advanced Threat Defense includes the features your need in one integrated solution to secure your users.
Protect your organization from Spam, Malware, Ransomware, Phishing and Malicious Attachments – without any per-user fees.
Sleep easy, knowing the next innocent mistake of that super-star employee wont turn into corporate disaster.
Business Email Compromise (BEC)
Cyber Enabled Financial Fraud is on the rise globally and there are new loopholes in business infrastructure being discovered and exploited in organizations without any enterprise email security.
At its very core, Business Email Compromise (BEC) is a modern-day variation of the oldest trick in the con artist’s handbook – the art of deception.
The motivation for BEC is typically financial, with the end goal of tricking an employee with finance access into making wire transfers to bank accounts thought to belong to trusted partners of the business, except the money ends up in accounts controlled by criminals.
These attacks are extremely sophisticated and these are the techniques that they use. Advanced Threat Defense protects you against these phishing attacks.

Remember – its now people rather than infrastructure that are the targets.
DuoCircle Advanced Threat Defense Suite
When you sign up for Advanced Threat Defense you get ALL the email protection solutions below.
Spam Filtering
Link Click Protection
Message Replay
Email Backup MX
DKIM signed SMTP
Data Loss Protection
Spear Phishing & Spoofed Domain Names
Spear-Phishing
Bogus e-mails believed to be from a trusted sender prompt victims to reveal confidential information to the BEC perpetrators.
This may include the names of internal people, their extension numbers or other information that would make the spear phishing emails seem even more legitimate.
These could be questions about the accounting practices, what software is being used for accounting or even if a CEO is attending a conference.
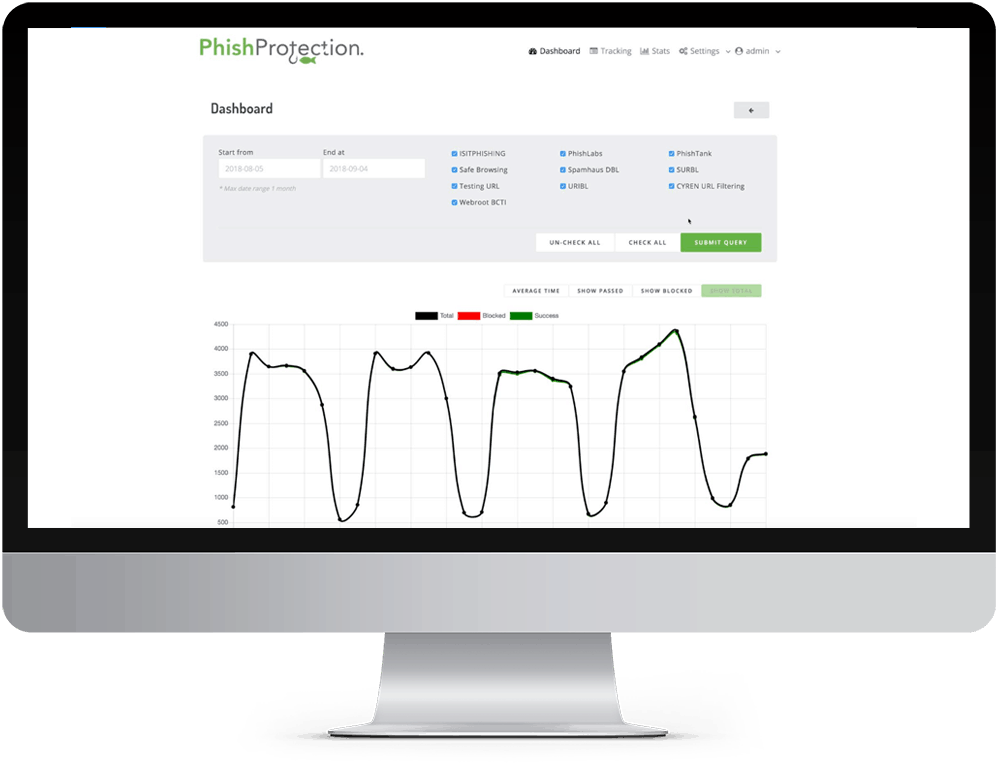
Spoofed Domain Names
Slight variations on legitimate addresses trying to fool victims into thinking fake accounts are legitimate.
The victim thinks he is corresponding with their CEO, but that is not the case. And, when wire transfer instructions are provided, the victim typically complies with the transfer request thereby falling for phishing through spoofed domain names.
Malware
Used to infiltrate company networks and gain access to legitimate e-mail threads about billing and invoices.
Malware also allows criminals undetected access to the victim’s data, including passwords and financial account information all through email security vulnerabilities.
Again, these could be questions about the accounting practices, what software is being used for accounting or even if a CEO is attending a conference.
All Advanced Threat Defense Plans Include
Unlimited Inbound Message Volume
Spam Filtering
Domain Name Spoofing Protection
Malicious Attachment Blocking
Activity Logs
Real time access to the mail queue and click reporting.
Smart Quarantine
30 Day Backup queue with MX backup service included.
24/7 email, chat and phone support.

Join the thousands of organizations that use DuoCircle
Find out how affordable it is for your organization today and be pleasantly surprised.