What is DKIM? DomainKeys Identified Mail Explained
DKIM is an email authentication standard that leverages the power of signature and encryption to safeguard email communication.
Cybercrime has become rampant in today’s times. A lot of cyber attacks originate from an innocuous-looking email that contains malicious links and attachments. Cyber adversaries impersonate prominent organizations to forge emails and pass them on to unsuspecting victims. Such minor and simple-sounding threats from malicious actors cause millions of dollars every year to large businesses and SMBs alike. The DKIM email authentication standard is one method organizations use to defend against such malicious interference.
Table of Contents

What Is Email Authentication?
In simple words, email authentication is a technical solution to substantiate that the emails launched from a specific server are not forged. It eliminates the possibility of a malicious actor impersonating an organization to send spam or phishing emails. The commonly used email authentication standards are SPF, DKIM, and DMARC.
What Is DKIM?
DKIM is the abbreviation for ‘Domain Keys Identified Mail.’ It is used for authenticating emails sent from specific servers. Similar to SPF, DKIM is used for DMARC alignment. Compared to SPF, the DKIM record in the DNS is slightly more complicated. However, the advantage is that DKIM can survive email forwarding, thereby making it a superior standard compared to SPF.
How Does DKIM Work?
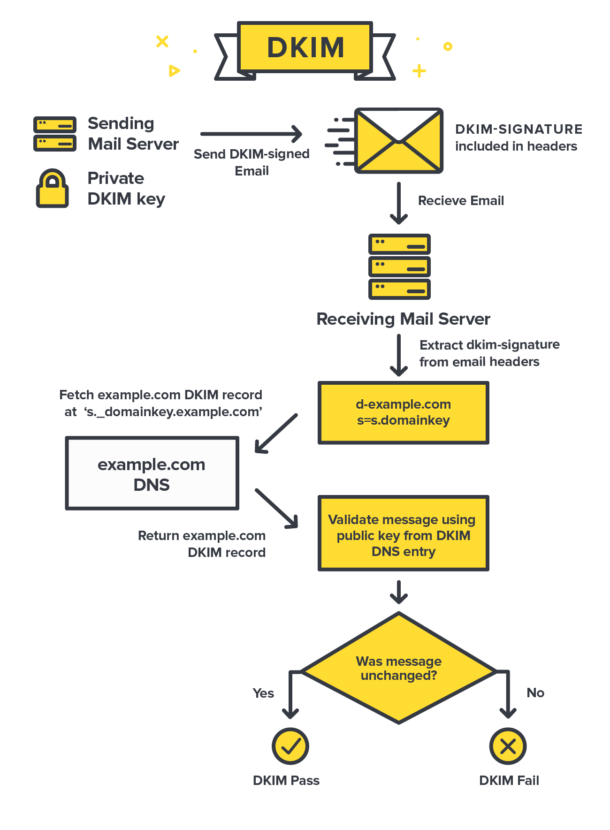
DKIM is a signature-based email authentication standard that gives emails a signature header and secures it with encryption. Thus, emails get a tamper-proof seal in the form of a DKIM signature. It confirms that the email has originated from the domain it claims. Secondly, it also certifies that there is no tampering with the email contents.
The procedure requires the configuration of email servers to attach unique signatures to each email sent through it. As DKIM remains effective even while forwarding emails, these signatures travel along with the emails. They are verified all along the way by email servers that receive and relay these messages towards the final destination.
Image source: postmarkapp.com
DKIM Signature Theory
DKIM signature contains every bit of information necessary for the verification of an email by the email server. It is encrypted by a pair of authentication keys known as the ‘private key’ and the ‘public key.’ The originating server has the private key, subject to verification by the receiving server with the corresponding public key.
It is the same fundamental theory used in public-key cryptography. A user can have a private key and a public key. The private key will only be known to themselves, whereas the public key will be shared with other users. When a sender sends an email, they sign it with their private key. Thus, the recipient can ensure it is genuine. The recipient can open it by applying the sender’s public key, which is published among all authorized users to open emails from the particular sender.
Adding DKIM Record Manually To Your Domain
Adding a DKIM record manually to a domain is easy once you know the theory and constitution of a DKIM record. A DKIM record carries information concerning the selector, the domain, the public key, and several other details. Setting up a DKIM record essentially involves defining these values. It is done in a specific format, typically consisting of a letter representing a parameter, followed by an ‘equals to’ sign and the parameter’s value. A typical DKIM record looks like this:
dk1025-2013._domainkey.manhattan1.net. 600 IN TXT "v=DKIM1\; p=IfAGSGI3QBQA4NDBQBQ1aglyMWLLy/egLoQ85lKCDFceVUncGrmM9bikog5N4cUwhQMZ0ve/EGiUPqciyH1FTAUMO86HvM5L4RskAMGM0CqSbDEAUAGACiKgCTNLSQNVNvYnDa2qETilqgtH8HAlamKDwdgG1cZ6RyfHQvPUwcel8Ao/ymfPbt8NtMxe4pAikAjqfYNTKV;"
In the above DKIM record sample,
dk1025-2013 is the information concerning the selector used, which will help locate the public key in the DNS. It is denoted using the tag s=.
manhattan1.net is the domain name of the sender, represented as d=.
p= is the public key used in conjunction with the digital signature and can be seen as a string of alphanumeric and special characters.
The tags mentioned above are mandatory. However, there are also certain optional tags used, like the ones described below.
v= It indicates the version of the DKIM record. It is usually given at the beginning of a record.
k= defines the type of key used. Usually, it is ‘rsa’ by default. Both signers and verifiers have to support it.
n= It is a provision to insert any note to be read by the administrators.
There are many more mandatory and optional tags than the ones listed above. While creating the DKIM record, one can choose the relevant tags as required and assign appropriate values.
How To Quickly Test DKIM Signature
Once you have incorporated DKIM into your domain, you can easily verify if the DKIM signature works by sending a test mail to any of your mail accounts. Here is the stepwise process for verifying if the email is DKIM-signed on Gmail.
- Once the DKIM signature is set up, send a test email to your Gmail account.
- Once the email is received in the inbox, open it.
- Click on the dropdown menu near the ‘reply’ icon (top right corner).
- Click ‘Show original.’
- You can now see more information on the email, including ‘signed-by,’ followed by your domain name. It shows that the DKIM signature is active. Otherwise, the DKIM is not correctly set.
What Is A DKIM Selector And Its Significance
The DKIM selector identifies the information of a public key related to a particular DKIM signature. Once a selector is set with the DKIM, all emails will be signed using it as the default selector. Multiple selectors can also be used for varying signatory controls on different users. It means that the same criteria do not necessarily govern all users.
A selector is an integral part of the DNS record and handles multiple DKIM keys in a particular domain. It holds great significance as it is the element that links the public and private keys while using a DKIM signature. In any DKIM signature, the private key specified for the particular signature is connected to a specific selector. And the associated public key specified in the DNS will also be locked to the same selector. Thus it is the selector that makes the functioning of the public-private key pair possible. Different selectors can be assigned to various vendors.
How Is DKIM Different From SPF And DMARC?
All three standards mentioned here enable different aspects of email authentication. The brief descriptions below show how they differ from each other.
- SPF – It allows email senders to define which IP addresses can send emails representing a particular domain.
- DKIM – It provides an encryption key and a unique digital signature to verify that the email message has not been altered.
- DMARC – It serves as a unification standard for SPF and DKIM. DMARC record integrates them into a common framework and allows the domain owners to state how they would like their domain to handle the email if it fails an authorization test.
Is DKIM Alone Enough For Authenticating Emails?
On its own, DKIM is not the most reliable authentication method for identifying the email sender’s identity. It cannot prevent spoofing of the domain that is visible in the email header. However, with the help of DMARC, one can guarantee that the domain seen by the end-user is the same as validated by DKIM and SPF.
Every business, whether small or big, depends on emails as the primary mode of communication. Malicious actors take advantage of this fact and continuously try to compromise the organization’s network by launching targeted cyber attacks such as spear phishing, which, if successful, can cause immense damage to the organization in terms of both money and reputation. Email authenticating standards like DKIM can serve as efficient safeguards in such situations and help the recipients verify that the emails’ contents have not been tampered with during its journey.