PHISHING PROTECTION
Malicious URL protection for every click, on every device.Defense from spear-phishing, ransomware, impersonation and other targeted attacks.
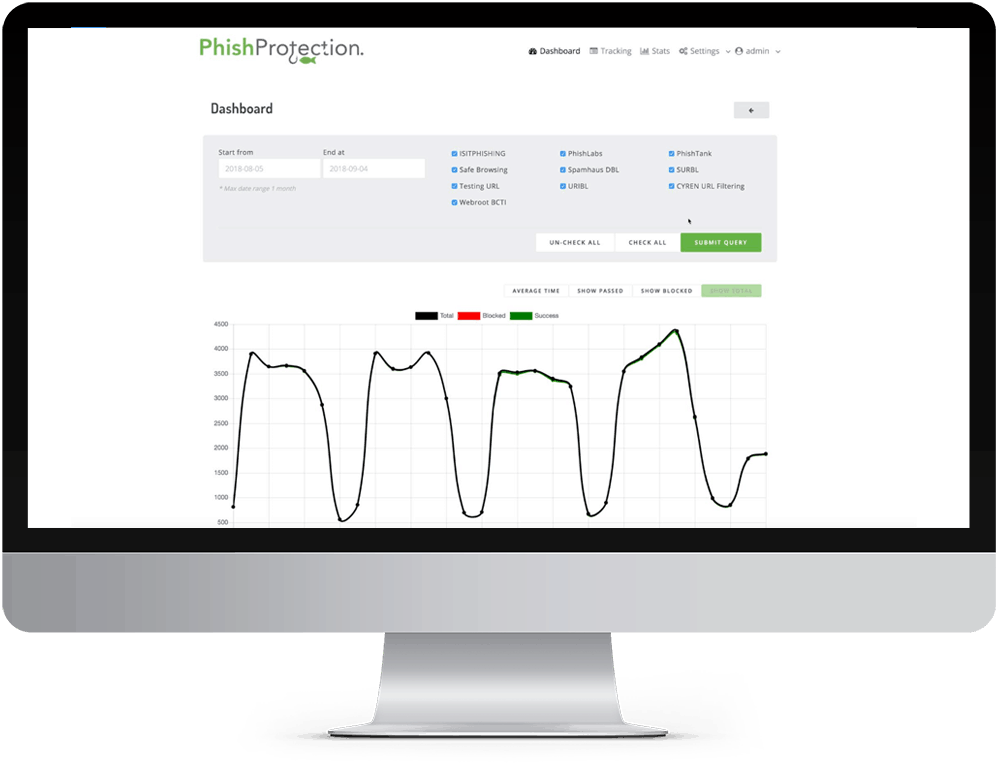
Get True Real-Time Phishing Protection
ON EVERY LINK CLICKED IN EMAILS
Email is the number one vector for sophisticated threats that are targeting your organization.
Remember – its now people rather than infrastructure that are the targets.
Ransomware And Phishing Protection
Ransomware is now a billion dollar a year crime. The FBI predicts that it is getting worse as more and more transactions shift online.
Blocks Malicious Websites
Protect your users against phishing mistakes by prompting them with a waing if they are going to an unsafe website.
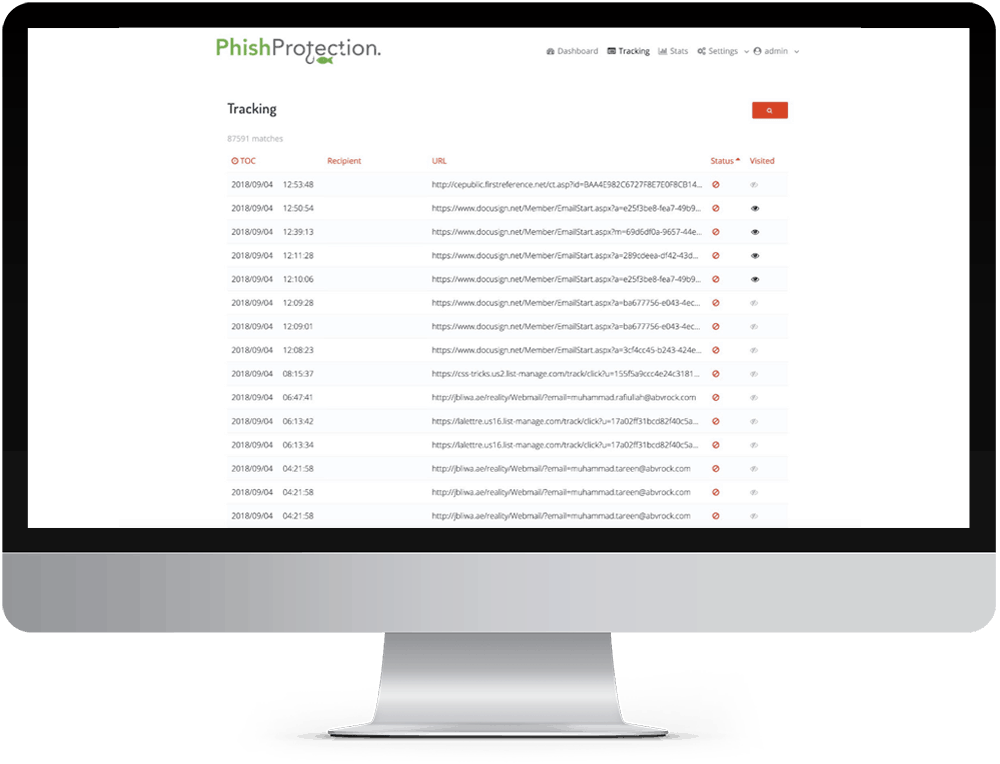
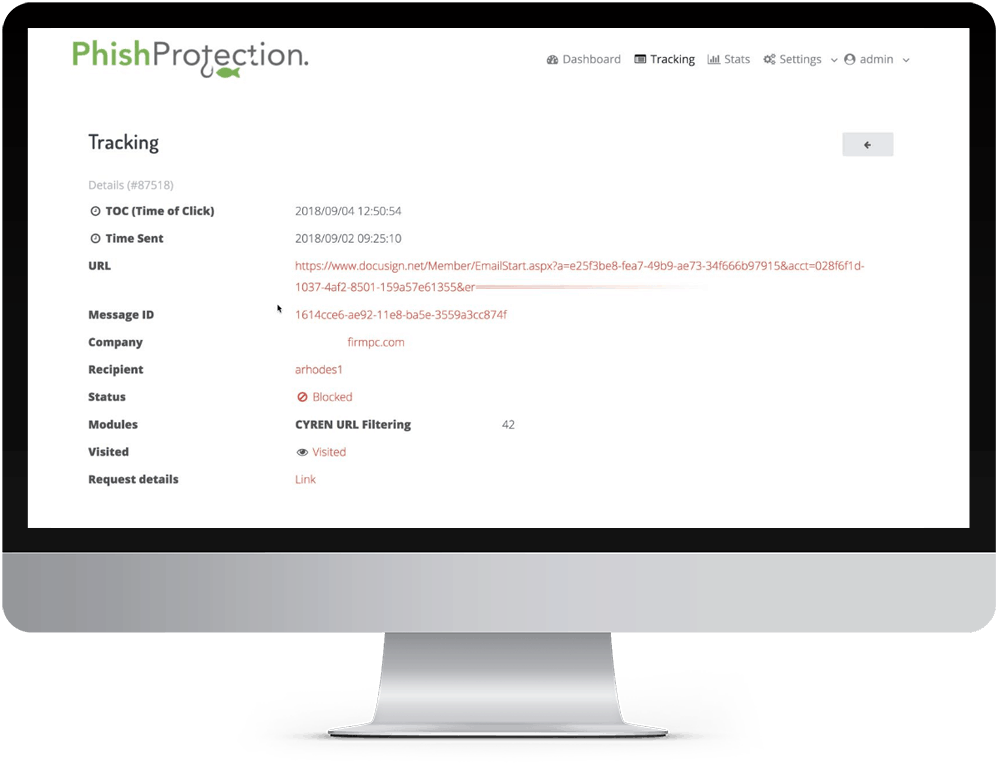
Real Time Link Checking
We check 6 URL reputation databases on each click for real time link checks and validation. Your clicks are in safe hands.
Our Link Click Protection includes subscriptions to the most advanced outbreak protection feeds for real-time protection.
It is part of the multi-layered approach to email protection called Advanced Threat Defense which is also offered by us at PhishProtection.com
Phishing Protection will work seamlessly with any Hosted Email, Office 365 and Exchange.
Attackers Thrive on Loopholes.
We Plug Them.
Phishing attacks can steal passwords or empty a bank account.
Ransomware can encrypt an entire network and shut down a company in seconds by locking the users’ infected devices. It is currently an extremely effective way to infect a computer or an entire network.
Google does try and do an adequate job if you use the Google Chrome web browser to protect against these bad links.
The response time is typically within a few hours, but there are more effective URL safety lists that can be combined with better link click protection.

Your Next Click Could Be The Fatal One
Your users are facing at least one risky email per day. Email is the number one vector for advanced threats that are targeting your organization.
These days its people rather than infrastructure that are the targets. Traditional spam filtering struggles to keep up with these new attacks, leaving your company at risk.
One of the more sophisticated techniques of Ransomware, Cryptolocker and Phishing scheme authors is to send an email from a domain or a URL with a good reputation.
When the emails are delivered to your mail server the site is clean, but within a few hours the hackers switch out the safe content on the site for their harmful payload.
This way they bypass the first line of defense – your spam and virus filters and then try to infect your computer with malware.
Spear Phishing & Spoofed Domain Names
Spear-Phishing
Bogus e-mails believed to be from a trusted sender prompt victims to reveal confidential information to the BEC perpetrators.
This may include the names of inteal people, their extension numbers or other information that would make the spear phishing emails seem even more legitimate.
These could be questions about the accounting practices, what software is being used for accounting or even if a CEO is attending a conference.
Spoofed Domain Names
Slight variations on legitimate addresses trying to fool victims into thinking fake accounts are legitimate.
The victim thinks he is corresponding with their CEO, but that is not the case. And, when wire transfer instructions are provided, the victim typically complies with the transfer request thereby falling for phishing through spoofed domain names.
Malware
Used to infiltrate company networks and gain access to legitimate e-mail threads about billing and invoices.
Malware also allows criminals undetected access to the victim’s data, including passwords and financial account information all through email security vulnerabilities.
Again, these could be questions about the accounting practices, what software is being used for accounting or even if a CEO is attending a conference.
Phishing Protection is Bundled with
Advanced Threat Defense
A MULTI-LAYERED APPROACH
Unlimited Inbound Message Volume
Spam Filtering
Domain Name Spoofing Protection
Malicious Attachment Blocking
Activity Logs
Real time access to the mail queue and click reporting.
Smart Quarantine
30 Day Backup queue with MX backup service included.
24/7 email, chat and phone support.
Join the thousands of organizations that use DuoCircle
Find out how affordable it is for your organization today and be pleasantly surprised.

