5 Trend Micro Alternatives That Provide Reliable Cloud Security Solutions
Many Trend Micro alternatives can keep corporate data and credentials secure from malware and phishing attempts.
With cybercrime on the rise and its increasingly sophisticated methods of attacks, the need for cybersecurity solutions has been consistently on the increase since 2014. According to Statista, the total spending projected for cloud security solutions worldwide in 2021 is $3.5 billion. The present pandemic has accelerated the need for enterprises to adopt cloud-based infrastructure. With data being migrated to the cloud, the need for reliable email security solutions has become paramount. According to research conducted by IDC, a global intelligence organization, 79% of organizations experienced at least one cloud data breach between January 2019 and June 2020, and 43% said they faced at least ten. The same study also indicated that the top three cloud security threats were due to the following reasons:
- Security misconfiguration of production environments (67%)
- Lack of visibility into access in production environments (64%)
- Improper Identity and Access Management (IAM) and permission configurations (61%)
In such a scenario, various Trend Micro alternatives can provide complete cloud-based security solutions to keep critical organizational data safe and secure from malicious forces trying to barge into your network periphery.
Table of Contents

6 Trend Micro Alternatives That Provide Cloud Security Solutions To Keep Corporate Data Secure
Here are five options among Trend Micro alternatives that can provide exceptional cloud security services for organizations.
DuoCircle
DuoCircle is one among the top email security service providers. DuoCircle’s email security solutions provide protection from phishing emails and phishing scams, phishing threat identification, ransomware & malware attacks, but also against spoofing and impersonation detection. DuoCircle specializes in Outbound SMTP for ensuring inbox delivery, DKIM Signed mail, advanced threat defense for email links, email forwarding, email backup, etc.
Zscaler
Convinced that the legacy castle-and-moat security approach is outdated and leaves an enterprise vulnerable to cyber-attacks, Zscaler offers a host of cloud security solutions via its Zscaler Zero Trust Exchange. Its fast, secure, work-from-anywhere mode provides the user with an attractive set of features for modern-day requirements. The Zero-Trust concept is based on the principle of not trusting any entity inside or outside an organizational network without thoroughly verifying its identity. It is similar to the guilty-until-proven-innocent approach. The two leading offers based strictly on this principle are:
Zscaler Internet Access
It’s a secure internet and web gateway that provides lightning-fast performance with its 150 data centers. It offers multiple security services, namely, Cloud Firewall/IPS, Sandboxing, URL Filtering, DLP (Data Loss Prevention), CASB (Cloud Access Security Broker), Browser Isolation, and CSPM (Cloud Security Posture Management).
Zscaler Private Access
With zero-trust access, users can access private applications running within Zscaler data centers or the public cloud, ensuring complete invisibility to unauthorized users.
Menlo Security
Menlo Security’s specialty is its Browser Isolation space. It promises its users 100% malware elimination. Zscaler recently extended its Secure Web Gateway to smartphones and tablets. Some of the leading solutions of Menlo are
Secure Web Gateway
In keeping with the principle of ‘zero-trust,’ Menlo Security’s trademarked ‘Isolation Core’ delivers internet security with no compromise. It aims to eliminate 100% web and email malware. The primary approach for accomplishing it is by providing ‘Server-Side Browser Isolation’ to quarantine the threats away from the users’ devices and corporate networks onto its remote cloud server. The result is clean content to the users’ devices.
Phishing and Ransomware Protection
Menlo Security’s Email Isolation uses detection-based technology to protect against advanced email attacks by using additional security along with the existing secure email gateway. All email attachments are viewed remotely, eliminating the possibility of ransomware reaching the users’ devices.
Netskope
Netskope is another leading cloud security solution provider that claims to be data-centric, cloud-smart, and fast. Also, following zero-trust policy, it implements a robust, secure web gateway. The following are two popular Netskope cloud solutions.
Netskope Security Cloud Platform
It provides real-time data and threat protection when accessing cloud services using a patented technology called Netskope Cloud XDTM. It also aims to secure managed cloud services such as G Suite, Office 365, AWS, and Box. The solution enables applying specific policies like removing public shares that help secure sensitive data in the cloud. It also provides granular control of unmanaged apps that continue to run safely, thus preventing stoppage time.
NewEdge
Netskope’s NewEdge is the world’s largest and highest-performing private cloud security network with no reliance on the public cloud infrastructure. The user can access it from data centers in over forty regions across the world. This state-of-the-art network infrastructure ensures security and data protection while delivering high performance and superior user experience.
Akamai
Akamai has established a robust Content Delivery Network (CDN) that is cost-efficient and performance-oriented. Akamai’s media delivery solutions are fast, scalable, and seamless. Through its Intelligent PlatformTM, Adaptive Media Delivery, users can enjoy high-quality, secure viewing on any device at varying connection speeds. The following are some core solutions offered by Akamai.
Cloud and Enterprise Security
It protects apps and APIs by providing DDoS protection, Web Application Firewall, and API protection in private data centers or the public cloud. It aims at preventing credential abuse by implementing Bot Management, Credential Stuffing, and Identity Management. Akamai Cloud Security also follows the zero-trust policy with a strict identity verification process.
Accelerating Web and Mobile Performance
It is a critical factor in engaging users. Akamai strives to innovate faster to build and deliver the best digital experiences by optimizing images and video, employing effective script, and identity management.
Authentic8
Authentic8 specializes in keeping users and enterprises safe on the web by creating an isolation layer between the user and the web. It accomplishes the mission using its secure virtual web browser, Silo. Authentic8’s solutions also cover administering access, SaaS app access, remote working, financial fraud detection, criminal investigations, and threat intelligence. Here is how it works.
Silo protects and streamlines OSINT (Open-Source Intelligence) research by providing an isolated browsing platform for accessing social media sites, forums, and other web-based resources keeping researchers completely anonymous. It also offers a professional-grade OSINT production platform to allow researchers to blend in with other local resources. The browser makes online investigations in the modern digital age anonymous, secure, and compliant with the chain-of-custody policy.
Administrators can preconfigure user access to websites, applications, etc., by embedding policy, security, and identity into the Silo browser. It enables users to access resources from trusted and untrusted devices and, at the same time, secures access to business-critical web applications. Granular policies help fine-tune user entitlements to web and application resources.
AccuKnox
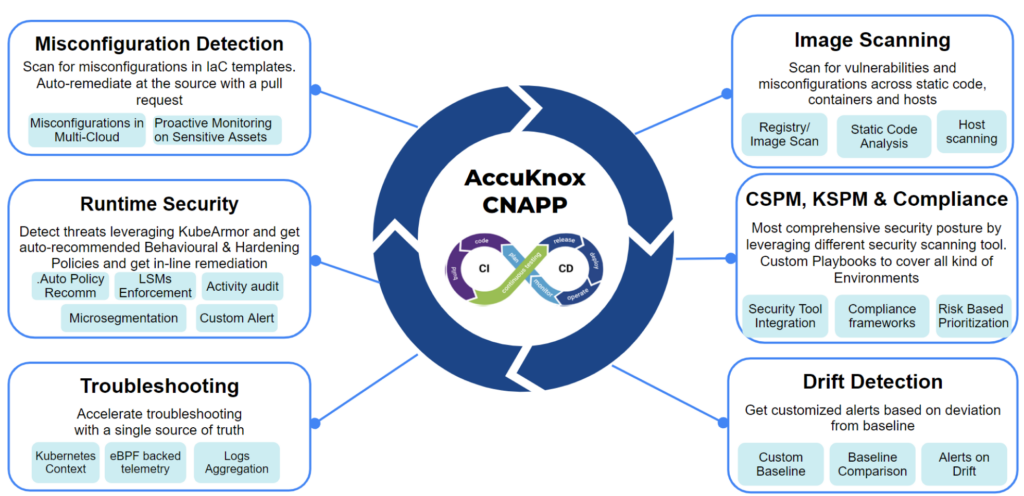
AccuKnox provides a comprehensive Zero Trust Cloud Security Tool that secures “Build to Runtime” in minutes. AccuKnox Zero Trust CNAPP (Cloud Native Application Protection Platform) protects Public clouds, Private clouds, Kubernetes, VMs, Bare metals, IoT Edge, and 5G security.
AccuKnox agentless multi cloud security provides “Inline Prevention as Opposed to Post-Attack Mitigation” to prevent advanced Zero-Day attacks before they happen!
- Comprehensive Zero Trust CNAPP
- Inline remediation as opposed to post-attack mitigation
- Agentless CSPM + eBPF, LSM powered CWPP
- Secures modernized (K8s) and traditional (VM) assets
- Supports Public, Multi-Cloud, and Private Clouds (on prem)
- Futureproof with support for IoT/Edge, 5G workloads
Final Words
The global pandemic has forced countless small and medium businesses to migrate to the cloud so that their workforce could operate remotely to prevent a complete shutdown. The lack of adequate cloud security for these organizations has resulted in unprecedented data breaches by malicious actors.
Having the cloud platform open to such security threats allows malicious actors to steal confidential corporate files and sensitive data like credit card information and login credentials. Having ample security and cloud platform features combined with appropriate configuration settings and constant monitoring is the best way out in such a scenario. And cloud security products from Trend Micro alternatives are some of the best solutions for the times.