Apple Patches ImageIO, Hackers Exploit Apache, Noodlophile Targets Firms – Cybersecurity News [August 18, 2025]
Cybersecurity threats continue to escalate this week. Apple issued its seventh zero-day fix of 2025 after reports of active exploitation. Hackers are abusing a two-year-old Apache flaw to install hidden back doors that patch themselves to evade detection. A phishing campaign is spreading malware against enterprises worldwide. Authorities renewed sanctions on crypto exchanges that moved over $100 million for ransomware groups and froze another $300 million tied to fraud. At the same time, another malware is exploiting Windows flaws to infiltrate multiple industries.
Apple Fixes Zero Day in ImageIO Under Active Exploitation
Apple just pushed out some critical security updates for iOS, iPadOS, and macOS, and you’ll want to get these installed right away. They’ve patched a zero-day flaw in the ImageIO framework, tracked as CVE-2025-43300, that could cause trouble when your device processes a malicious image. Apple mentioned it’s aware of reports that this vulnerability has been used in targeted attacks, although they haven’t shared specifics on who was behind them or who was targeted. The fix involves better memory handling and is available for iPhones XS and later, various iPads, and recent macOS versions.
This marks the seventh zero-day vulnerability Apple has had to fix in 2025, showing just how persistent attackers are. It follows another recent patch for a Safari bug that was also being actively exploited, which was reported by Google as having been exploited as a zero day vulnerability in the Chrome web browser. It’s a good practice to keep your devices updated to stay protected from these kinds of targeted attacks.
Hackers Use Old Software Bug to Break into Apache and Then Secretly Fix It
Hackers are taking advantage of a significant weakness in Apache ActiveMQ to get into cloud-based Linux systems, where they’re installing a new tool called DripDropper. What’s unusual is that after they break in, they patch the vulnerability they used. This move locks out other attackers and makes it a lot harder to spot their presence. Once they have control, they tweak SSH settings for root access and use tools like Sliver and Cloudflare Tunnels to stay hidden.
The DripDropper tool itself is password-protected and cleverly conceals its activity by connecting to Dropbox accounts controlled by the hackers. It then downloads additional files to make sure their access sticks around, messing with cron jobs and SSH backups. After setting up their backdoor, the hackers even installed official security patches to cover their tracks completely. While it’s not a common tactic, it’s so dangerous and highlights why it’s so important to patch systems quickly and keep a close eye on cloud environments for anything out of the ordinary.
Noodlophile Malware Uses Fake Copyright Emails to Target Global Firms
A malware campaign known as Noodlophile is back with some clever new tricks, targeting businesses across North America, the whole of Europe, and some of the Asia Pacific region. Attackers are sending out compelling spear phishing emails that look like copyright infringement notices. To make them seem legitimate, the emails are personalized with details like the company’s Facebook Page ID. These messages, which often come from Gmail accounts, contain Dropbox links that cleverly install the Noodlophile malware by hiding it within a legitimate PDF reader program.
This new version of Noodlophile is even sneakier, allegedly using social media descriptions to hide the location of its malicious payload. Once it’s running on a system, the malware gets to work stealing browser data and other system information. The attackers are still developing it, with plans to add keylogging and file encryption features. For now, businesses with a strong social media presence, especially on Facebook, are the primary targets and are advised to be vigilant.
PipeMagic Malware Exploits Windows Flaw in RansomExx Attacks
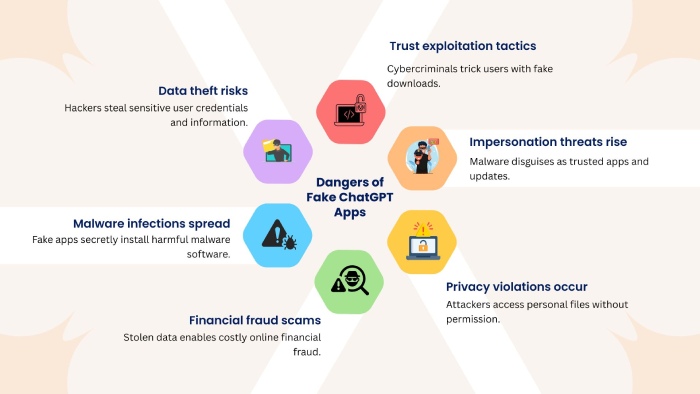
Cybersecurity researchers are flagging new attacks from the PipeMagic malware, which has ties to the RansomExx ransomware group. These attackers are taking advantage of a recently patched Windows vulnerability (CVE-2025-29824) to gain higher-level access. PipeMagic isn’t new; it first appeared in 2022 and has been spread through fake ChatGPT apps before. In the latest incidents, they’re disguising the malware as Microsoft Help files or Chrome updates to trick users, while also using other methods to steal credentials and move around unnoticed.
PipeMagic is particularly sneaky because it’s a modular backdoor that loads its harmful tools directly into memory, which helps it avoid detection. It uses encrypted channels to communicate secretly, allowing attackers to read files, run malicious code, and spread across a network without leaving a trace. It maintains a modular, hidden, and highly extensible architecture, making detection and inspections a substantial hurdle. The 2025 versions have gotten even better at staying hidden and have more capabilities. With victims in IT, finance, and real estate across the globe, it’s clear that PipeMagic is an active and evolving threat.
Sanctions Tightened on Crypto Exchange Linked to Ransomware Laundering
The U.S. Treasury is cracking down again on the cryptocurrency exchange Garantex, hitting it with renewed sanctions for handling over $100 million in illegal transactions for ransomware gangs and darknet markets. They didn’t stop there, though. Sanctions were also extended to its successor, Grinex, allegedly along with three executives and six related companies in Eastern Europe and Central Asia that helped keep the operation running. Even after a significant takedown effort back in March 2025, Garantex just moved its systems and funds over to Grinex, which is still processing billions in crypto transactions.
Authorities have linked Garantex to laundering money for notorious ransomware groups like Conti, LockBit, and Ryuk, and it also worked with other money launderers and cybercriminals. Allegedly, its top executives were apparently in on it, helping to set up the infrastructure and make everything look like a legitimate business. In a related move, the Department of Justice seized $2.8 million in crypto and other assets tied to this mess. On top of that, they froze another $300 million in crypto connected to fraud and romance scams, showing they’re serious about stopping criminals from exploiting virtual currency platforms.