How to avoid email authentication failures when sending messages to Microsoft 365 users?
If you are struggling with disappearing emails or deliverability drops when targeting Microsoft 365 users, then it’s an indication of an underlying issue— misconfigured or missing email authentication protocols.
Email authentication protocols are sensitive; they must be configured in a certain way, otherwise, they can do more harm than good. Often, misconfigured SPF, DKIM, and DMARC records trigger instances of false positives, which means that even genuine emails sent from your domain are either marked as spam or bounce back.
This blog discusses key considerations for avoiding email authentication failures when sending messages to Microsoft 365 users.
Correctly set up and configure SPF, DKIM, and DMARC records for your domain
Use the configuration information that your domain registrar or DNS hosting service shared with you. Often, domain owners refrain from publishing SPF records because they don’t know all the IP addresses and mail servers that send emails on their behalf.
The first step is to enlist all email sources, including those of third-party senders that send emails from your domain (such as Microsoft Azure, GoDaddy, Rackspace, and Amazon Web Services). Then create an SPF record and use the SoftFail enforcement.
If your domain has a valid SPF record, Microsoft 365 treats inbound email from your corporate infrastructure as authenticated. However, emails from unidentified sources will be marked as spam—this is essentially what the principle of the SPF protocol is.
Once you have identified and added all the sending sources, you can proceed to change the enforcement to ‘Hard Fail.’ However, don’t rush to make this transition; we suggest you proceed with it only when you are fully confident that there are almost no instances of false positives.
The next important step is to activate DKIM for your domain, which utilizes cryptographically secure keys to verify that the email content has not been altered during transit.
Lastly, set up DMARC so it can check whether the domain in your “From” address matches your actual sending domain (the one in your MAIL FROM).
It also allows you to specify how mailbox providers should handle emails that fail this check, whether to reject them or send them to the spam folder.
If you use tools or bulk senders (such as a CRM or newsletter software) to send emails on your behalf, ensure the “From” domain still matches the one that passes SPF or DMARC.
Otherwise, Microsoft might consider your emails suspicious, even if you’re the actual sender.
Aggregate and forensic reports help fix the misconfigurations
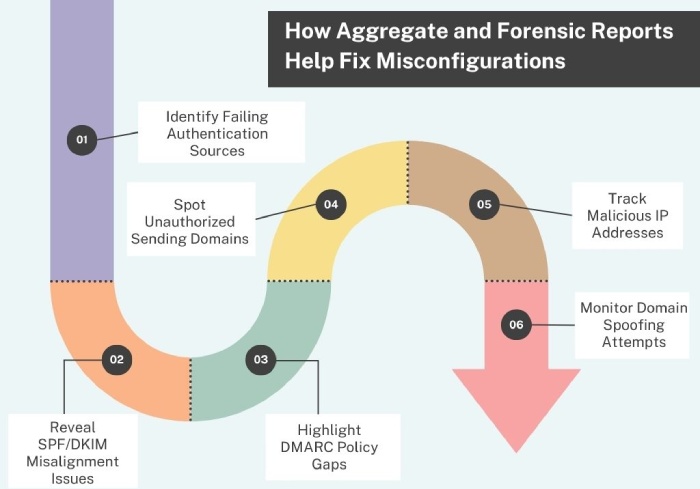
Aggregate and forensic reports indicate which emails are failing DMARC and why, such as when SPF or DKIM is not passing, or when someone is using your domain without permission. These reports help you identify issues, such as missing DNS records or incorrect sender sources. Once you identify the problem, you can correct the misconfigurations and ensure that your emails pass authentication the next time they are sent.
If you’re still running into issues with SPF, DKIM, or DMARC, the experts at DuoCircle are here to help.