Hackers Exploit Shellter, Anatsa Trojan Spreads, Pull Request Breach – Cybersecurity News [July 07, 2025]
This week’s cyber world feels like a game of digital whack-a-mole, where every time defenders squash one threat, another pops up somewhere else. There are hackers sneaking malware into trusted tools, trojans hiding in mobile apps, and cybercriminals hijacking search results and online ads. From leaked security software fueling new attacks to crafty scams riding the wave of AI buzz, cybercriminals are proving they’ll exploit anything. Here’s how they’ve been keeping security teams on their toes!
Hackers Abuse Leaked Shellter License to Deploy Malware
Hackers have started using a leaked license of Shellter, a tool meant for cybersecurity testing, to hide malware that steals personal information following the publication of the article “Taking SHELLTER: a commercial evasion framework abused in-the-wild” by Elastic Security Labs.
Shellter’s creators said a client leaked their paid version, allowing attackers to turn it into a weapon for spreading threats like Lumma Stealer, Rhadamanthys Stealer, and SectopRAT. Though the tool helps security experts bypass antivirus checks for testing, threat actors are now using it to slip past security software and hide malicious code in normal-looking apps.
Security firm Elastic found several money-driven hacking campaigns starting in late April 2025 using Shellter Elite version 11.0. On the other hand, hackers reportedly shared the stolen tool on underground forums, used YouTube videos about gaming cheats, and even used fake sponsorship offers to lure victims. Some attacks dropped malware through file-sharing services like MediaFire.
Shellter has released an update to fix the problem, but tension remains, with Shellter’s team holding Elastic accountable for going public too quickly instead of notifying them first. Right now, it’s best to keep software updated and avoid downloading programs or files from unfamiliar sources.
Anatsa Android Banking Trojan Infects 90,000 Users Through Fake PDF App
Security experts have uncovered an Android malware campaign where a banking trojan called Anatsa was spread through apps on Google Play, mainly targeting users in the region of North America.
The attackers disguised the malware as a “PDF Update” inside a document viewer app, which seemed harmless at first. After gaining thousands of downloads, they pushed an update that secretly installed Anatsa as a separate app. Once active, Anatsa shows fake messages saying banking apps are under maintenance, tricking people into sharing login details. The Trojan can log keystrokes, steal credentials, and even take over devices to make fraudulent transactions.
Researchers say this is the third time Anatsa has hit mobile banking users in the U.S. and Canada. Previously, it used similar tactics in European countries, posing as PDF readers and phone cleaners before turning malicious. The malicious app behind the latest attack, called “Document Viewer – File Reader,” was downloaded about 90,000 times before Google removed it.
Google has taken down these apps, but users are encouraged to install only authorised apps from trusted sources and watch for sudden updates or suspicious permission requests to stay safe.
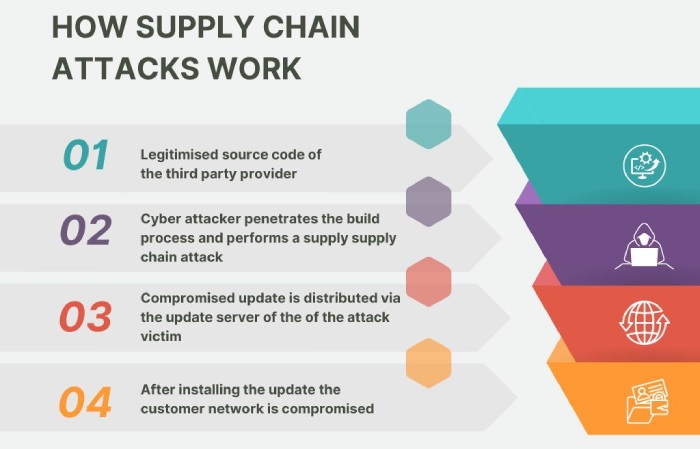
Malicious Pull Request Exposes Over 6,000 Developers’ Sensitive Data
A supply chain attack has hit Ethcode, a Microsoft Visual Studio Code extension used for working with Ethereum smart contracts, which had over 6,000 installs.
On 17 June 2025, an unknown user named Airez299 submitted a pull request on GitHub, claiming to modernize the Ethcode project. Hidden in what seemed like helpful updates, the attacker added two malicious lines of code among thousands of changes. This code introduced a new npm dependency called “keythereum-utils,” which, once imported into Ethcode’s code, secretly downloaded further harmful software.
The malicious library was downloaded 495 times before being removed from the npm registry, and multiple fake npm accounts were used to spread different versions. Experts believe the malware was built either to steal crypto assets or corrupt smart contracts. Following the discovery, Microsoft removed Ethcode from the marketplace and has since reinstated it after cleaning out the malicious code.
Currently, the threat has been neutralized, but developers should stay cautious, review code contributions carefully, and avoid unverified packages.
RondoDox Botnet Leverages Security Vulnerabilities for DDoS Attacks
Cybersecurity experts are warning about RondoDox, a new botnet exploiting security flaws in TBK DVRs and Four-Faith routers to hijack devices and use them for cyberattacks.
Hackers are abusing two known bugs (CVE-2024-3721 in TBK DVRs and CVE-2024-12856 in Four-Faith routers) to gain remote control, especially targeting devices in places like stores and offices that often run outdated software and sit exposed on the internet. Instead of simply flooding networks with traffic, RondoDox turns infected gadgets into hidden proxies to mask command signals, commit fraud, or boost DDoS-for-hire operations.
First spotted in late 2024, the malware spreads to various Linux systems through a shell script that turns off standard shutdown signals, searches for writable folders, and wipes activity logs to hide its tracks. It even renames system files to block recovery and kills tools like Wireshark or other malware to avoid interference. Finally, it contacts external servers and imitates traffic from games, chat apps, or VPNs to stay under the radar.
Researchers say attacks are ongoing, and users should update device firmware, secure network ports, and monitor for unusual traffic.
SEO Poisoning Campaign Delivers Malware Posing as AI Tools
Cybersecurity experts have uncovered hackers using SEO tricks to spread a malware loader called Oyster (also known as Broomstick).
They do this by creating fake websites that pretend to offer trusted tools like PuTTY and WinSCP, luring professionals to search online. When people download these fake apps, the malware installs a backdoor and sets up a scheduled task that runs every three minutes to keep itself active by launching a harmful DLL file. The threat actors have used domains like updaterputty[.]com and putty[.]run, and they’re likely targeting other tech tools, too. Alongside Oyster, they are also pushing other malware like Vidar, Lumma, and Legion Loader by gaming search results for terms tied to AI and popular apps.
These malicious ads also appear on Facebook, aiming to steal crypto wallets or credit card details through fake apps and shopping pages. Moreover, the attackers have been manipulating Google search results to show fake support numbers on legitimate websites.
The attacks are still ongoing, so stick to official sites for downloads, check URLs carefully, and avoid clicking any suspicious links that seem phishy!