Charon Ransomware Threatens, Data Breach Notifications, TETRA Security Flaws – Cybersecurity News [August 11, 2025]
Cybersecurity incidents this week include Google completing notifications for a Salesforce breach linked to ShinyHunters, and the discovery of Charon ransomware targeting the Middle East public and aviation sectors with APT-style tactics. Researchers exposed new 2TETRA:2BURST flaws in critical TETRA radio systems, while a WinRAR zero-day was exploited by Paper Werewolf and RomCom groups. The GreedyBear campaign stole over $1 million via malicious browser extensions, alongside an Ethereum trading bot scam using AI-generated YouTube videos to drain wallets of nearly $900,000. Let’s dissect each news in brief!
Charon Ransomware Targets Middle East Public Sector and Aviation
Cybersecurity researchers have found a new ransomware called Charon that’s going after public sector and aviation organizations in the Middle East. Trend Micro reports that the attackers are using some advanced tactics, like DLL side-loading and process injection, to sneak past security software. They get in by using a legitimate Edge.exe file to load a malicious DLL, which then unleashes the ransomware. Charon is built to shut down security services, wipe out backups, and encrypt files quickly using multithreading.
Interestingly, the attackers also tried to use a “bring-your-own-vulnerable-driver” technique to disable endpoint detection, though it seems that part wasn’t fully working yet. The ransom notes were customized for each victim, which shows these weren’t random attacks. While it’s not confirmed, the campaign has similarities to the Eastern-linked Earth Baxia group, suggesting it could be them or a new group copying their style. This all points to a bigger trend where ransomware attacks are becoming as sophisticated as nation-state operations, combining stealthy methods with disruptive encryption to cause maximum damage.
Google Confirms Data Breach Notifications Sent to Impacted Users
Google has now finished letting organizations know they were affected by the recent data breach carried out by the ShinyHunters group, also known as UNC6040. The incident, which came to light on August 5th, involved a violation of a Salesforce database that stored contact information and notes for small and medium-sized businesses. According to Google, the information that was accessed mainly was basic business data, like company names and contact details, much of which is already public.
This confirmation comes after some security researchers raised concerns about how long it took to notify the victims, pointing out that the attackers had the data for nearly two months before it was disclosed. While Google hasn’t shared the specific email it sent out, it has stated that everyone impacted has been contacted. The full extent of the breach is still under investigation, and the company has yet to release all the details.
New Flaws Expose Critical Security Gaps in TETRA Communications
Security researchers at Midnight Blue have uncovered some serious new flaws in the TETRA radio protocol, which is a system used by police, military forces, and critical infrastructure operators around the world. These vulnerabilities, called “2TETRA:2BURST,” target the protocol’s end-to-end encryption. They make it possible for attackers to replay messages, break in with brute force, inject their own malicious traffic, and even decrypt communications that are supposed to be secure. The issues are pretty deep, involving a weakened encryption algorithm and no protection against replaying voice or data messages.
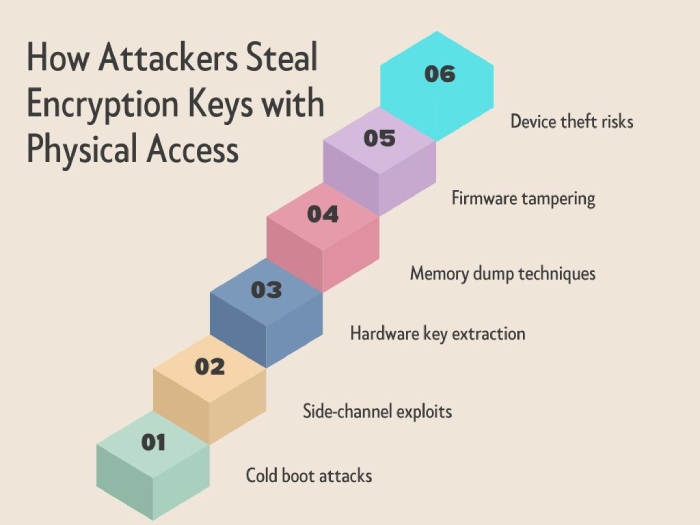
The researchers warned that networks carrying data are especially at risk. Even though the European standards body, ETSI, notes that the encryption isn’t part of its official standard, fixes for these problems are limited. To make matters worse, related flaws were also found in Sepura SC20 TETRA radios that could let an attacker with physical access steal encryption keys. For now, there’s no evidence that hackers are actively using these flaws. However, experts are urging operators to switch to more secure encryption, disable the outdated TEA1 algorithm, and add protective layers like a VPN until things are patched up.
WinRAR Zero-Day Exploited by Paper Werewolf and RomCom Groups
The team behind WinRAR had fixed a significant security flaw that was already being used in live attacks. This vulnerability, found in versions before 7.13, let attackers run malicious code by tricking users with a specially crafted archive file. Security firm ESET discovered the bug, while another firm, BI.ZONE reported that a Northeastern-linked group called Paper Werewolf likely bought the exploit on the dark web. They used it in phishing campaigns to plant malware on victims’ systems, all while showing them harmless-looking decoy documents to avoid suspicion.
At the same time, the RomCom hacking group was also using the flaw as a zero-day attack against financial, manufacturing, and defense companies in Europe and North America. Their method involved using malicious archives to install several backdoors, including SnipBot and RustyClaw. Although ESET found no proof of a successful breach, it shows how skilled the group is becoming. Coincidentally, 7-Zip also released a patch for a similar issue that could allow hackers to write files and run code, particularly on Unix systems.
GreedyBear Steals Over $1 Million Through Malicious Browser Extensions
A huge new scam called GreedyBear has been found using over 150 fake Firefox extensions that pretend to be popular crypto wallets like MetaMask and TronLink. The attackers used a sneaky trick; they’d first publish a clean extension to get it approved and then push a malicious update later. This new code was designed to steal wallet credentials and IP addresses, sending everything back to a central server. This campaign is a bigger version of the earlier Foxy Wallet scam and also spreads malware through pirated software sites. It looks like they’re now targeting Chrome users and might be using AI to create fake extensions even faster. Users trying to quickly convert funds, such as usdt to usd, should be especially cautious and verify that their wallet extensions are legitimate before initiating any transactions.
At the same time, another scam has popped up involving what looks like an Ethereum trading bot. It’s promoted with AI-generated YouTube videos on old accounts to seem legitimate, tricking people into setting up a malicious smart contract. As soon as you put money into it, the contract sends your crypto straight to the scammers’ wallets. They’ve already made off with nearly $900,000 this year alone. It just shows how even smaller groups can use AI and fake online buzz to build trust before pulling off major thefts.