A guide to DKIM syntax– create your DKIM record for free
A DKIM record is a DNS record in the TXT format that includes a public key that is used by recipients’ mail servers to verify the legitimacy of emails they receive from your domain. A standard DKIM record has a name, version, key type, and public key. Some domain owners think that creating a DKIM record requires hardcore technical expertise, but that’s not true, especially when it comes to generating a basic DKIM record. You just need to be an average tech user, and you will be able to create a DKIM record on your own.
The purpose of DKIM
DKIM is a technology that verifies whether an email was sent from a mail server officially authorized by the domain owner. It is based on the concept of public key cryptography, which is the same standard as used in SSL certificates.
When you deploy DKIM for your domain, the sender’s mail server digitally signs a part of the outgoing email. Then, upon reception, the receiving mail server retrieves the public key from your DKIM record to verify the signature. A successful verification indicates that the email content was not modified in transit– which means the recipient has received the email exactly how it was sent by you. This technology prevents recipients from deceiving messages.
The concept of cryptographic keys
In DKIM, there are two cryptographic keys involved per DKIM record. One is a private key that nobody knows or has access to except the owner. The second is the public key that is openly available. Both keys are related to each other, which means that the text encrypted with the private key will be decrypted with its corresponding public key only and vice versa.
In simpler words, if a receiving server is able to decrypt a message with the public key mentioned in the sending domain’s DKIM record, then there is a surety that it was signed with the private key that only the owner of the sender’s domain knows.
In simpler words, if a receiving server can decrypt a message using the public key specified in the sending domain’s DKIM record, it confirms the message was signed with the private key known only to the domain owner. Properly adding DKIM record ensures this authentication process works reliably and boosts email deliverability.
If you enable DKIM, then the digital signature will be added to the header of all emails sent from your domain. The recipient’s server can read in the header which part of the email it needs to verify and the location of the public key that it will require for verification.
DKIM encounters issues with forwarded emails and mailing lists
DKIM faces problems with email forwarding and mailing lists because the email content and headers get modified. So, when an email is forwarded, the DKIM signature no longer matches the original email, triggering DKIM to fail.
The same is true for mailing lists. Mailing lists often modify the original email by adding headers, footers, or making other alterations. These changes can invalidate the DKIM signature. Additionally, mailing lists may modify the subject line, add list-specific headers, or even strip certain headers, which can affect DKIM validation.
How to mitigate this problem?
There are 4 main strategies that you can deploy to minimize or evade the shortfalls of DKIM with forwarded emails and mailing lists.
Enable ARC
ARC is a relatively new email security technology that preserves email authentication results across intermediate servers that emails pass through when forwarded or sent using mailing lists. It allows intermediaries to record the authentication status of the message exactly as they received it, enabling downstream systems to trust the results even if the message is modified.
Use the “l=” tag
The job of the “l=tag” is to specify the length of the message body that is included in the signature. This can be useful if only the initial part of the message body is signed, allowing certain types of modifications to not break the signature. Please note that this tag has some limitations.
Minimize changes
Encourage mailing lists and email forwarding services to minimize changes in the original email content sent by you. There are some software that allow you to make configurations so that they make minimal modifications to the messages they process.
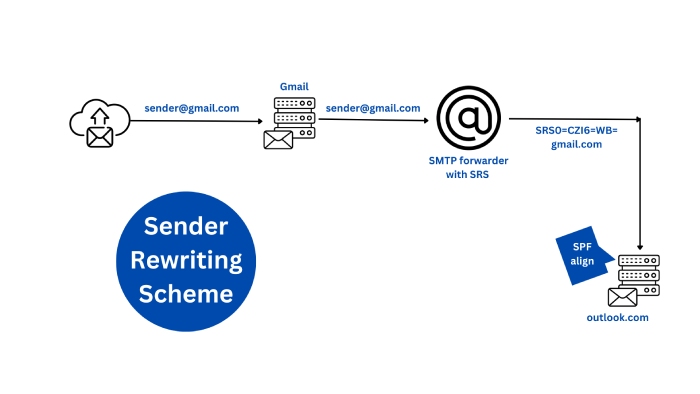
Sender rewriting scheme
For forwarded emails, SRS can help maintain SPF validity, but it does not directly address DKIM. Combining SRS with ARC can provide a more comprehensive solution.
DKIM Syntax
Here’s a breakdown of the most used DKIM syntax elements-
‘v’ tag (mandatory)
It stands for the ‘version’ tag that basically indicates the DKIM version you use. Currently, there is only one version, so it is always ‘v=1.’
‘a’ tag (mandatory)
It stands for the ‘algorithm’ tag and specifies the algorithm used to generate a signature. Common algorithms are rsa-sha256 and rsa-sha1.
‘d’ tag (mandatory)
It stands for the ‘domain’ tag and indicates the domain that is claiming responsibility for the message.
‘s’ tag (mandatory)
It stands for the ‘selector’ tag that specifies the DKIM selector used to locate the public key in DNS.
‘c’ tag (optional)
It stands for the ‘canonicalization’ tag and tells the canonicalization algorithms for the header and body. Two types are allowed: simple and relaxed.
‘q’ tag (optional)
It stands for the ‘query method’ tag and defines the method used to retrieve the public key. Typically, this is dns/txt.
‘t’ tag (optional)
It stands for the ‘timestamp’ tag and provides the signature timestamp in Unix time format.
‘x’ tag (optional)
It stands for the ‘expiry’ tag and specifies the expiration time for the signature in Unix time format.
‘h’ tag (mandatory)
It stands for the ‘signed headers’ tag and lists the headers that are included in the signing process. Common headers include From, To, Subject, etc.
‘bh’ tag (mandatory)
It stands for the ‘body hash’ tag and contains the hash of the canonicalized body part of the message.
‘b’ tag (mandatory)
It stands for the ‘signature data’ tag and holds the actual digital signature, which is usually a base64 encoded string.
‘l’ tag (optional)
It stands for the ‘body length count’ tag and species the length of the canonicalized body that has been signed.
‘z’ tag (optional)
It stands for the ‘copied headers’ tag and provides a list of header fields copied from the email and their values, which can be used for diagnostic purposes.
Final words
Avoid creating a DKIM record manually, as this approach is more prone to human errors. Instead, use one of the online DKIM generator tools. Once your DKIM record is produced, update it on your domain’s DNS and regularly run it through one of the DKIM lookup tools to see if there are any errors in it. If detected, fix the errors without any delays to prevent threat actors from exploiting your vulnerable DKIM record. For any help, contact us.