Email communication remains one of the most essential tools for businesses and individuals alike, but ensuring its authenticity is critical to protecting recipients from phishing and spoofing attacks. One of the key mechanisms for verifying the legitimacy of an email is DomainKeys Identified Mail (DKIM), which uses cryptographic signatures to confirm that messages haven’t been altered in transit and truly originate from the claimed domain.
However, when DKIM signature validation fails, legitimate emails may end up flagged as suspicious or rejected altogether, disrupting communication and damaging sender reputation.
Understanding DKIM: What is DomainKeys Identified Mail?
DomainKeys Identified Mail (DKIM) is a pivotal email authentication protocol designed to ensure message integrity and sender authentication. By leveraging cryptographic signatures embedded within email headers, DKIM enables the receiving mail transfer agent (MTA) or email gateway to verify that the email was indeed sent by a legitimate domain owner and that the message content was unaltered during transit. Developed through extensive collaboration, including contributions from DKIM Core, this mechanism has become a cornerstone of email security practices employed by major platforms such as Google Workspace, Microsoft Office 365, and Amazon SES.
DKIM functions through the use of a public key infrastructure (PKI) embedded within DNS TXT records published by the sending domain. The corresponding private key is used by the sender’s outbound email filtering system or SMTP protocol client to generate digital signatures. These signatures are included in the email headers and subsequently validated by recipient servers to prevent email spoofing and enable effective phishing protection.
The Role of DKIM in Email Authentication and Security
DKIM is a fundamental component within a triad of email authentication standards alongside the Sender Policy Framework (SPF record) and the DMARC protocol. While SPF determines which servers are authorized to send emails on behalf of a domain, and DMARC enforces policy rules about how unauthenticated emails should be handled, DKIM focuses on message authentication by verifying digital signatures to guarantee email content integrity.
The use of cryptographic signatures in DKIM bolsters email fraud prevention strategies deployed by organizations and services, including Microsoft Exchange Server, Mailchimp, and SparkPost. It significantly enhances email reputation by demonstrating commitment to sender authentication and message authentication standards. Additionally, it improves inbound email filtering effectiveness by validating the trustworthiness of emails before they reach the recipient’s email client.
Enterprises and IT admins, leveraging solutions from vendors such as Proofpoint, Barracuda Networks, Trend Micro, and Agari, integrate DKIM verification as part of broad email security architectures that also include bounce management and header analysis to maintain email compliance and reduce the risk of domain spoofing.
How DKIM Signature Validation Works
When an email is composed and sent via an SMTP protocol-enabled system—such as Postfix, OpenDKIM, or Microsoft Exchange Server—the sender’s mail transfer agent signs specific headers and the body of the message with a private key. This signing process generates a digital signature that is inserted into the email headers as a DKIM-Signature field.
Upon receipt, the recipient’s email gateway or inbound email filtering system extracts the DKIM signature from the email headers. It then retrieves the corresponding public key from DNS TXT records using the domain information specified in the signature. This exchange relies heavily on the DNS infrastructure, with many services including Cloudflare and DomainTools providing DNS management and monitoring tools.
The public key is used to decrypt the signature and compare the hash of the received content with the hash generated by the signing process. If the hashes match, message integrity is confirmed, indicating that the email’s header and body have not been tampered with en route. This process serves to authenticate the sender and affirms the email’s legitimacy, improving trust verification and supporting phishing protection mechanisms.
Common Causes of DKIM Signature Validation Failures
DKIM signature validation failures can arise from a variety of issues, each impacting email delivery and security:
Incorrect DNS TXT Records Configuration:
If the public key DNS TXT records are missing, malformed, or outdated, validation will fail. This is common when domains change DNS hosts or when keys are rotated without proper publishing, a frequent challenge for administrators using DNS providers like Cloudflare or when migrating between services such as Google Workspace and Microsoft Office 365.
Message Modification in Transit:
Some email intermediaries or gateways—including certain configurations of Mimecast or Barracuda Networks—may alter email headers or bodies for security scanning or compliance reasons. Even benign changes can invalidate the DKIM signature, causing failures in message authentication.
Selector Misconfiguration:
DKIM uses selectors to identify which key to use for validation. Mismatches between the selector specified in the email headers and the published DNS TXT records prevent successful verification.
Outdated or Expired Keys:
Failing to update or rotate DKIM keys regularly—as recommended by security standards and enforced in enterprise environments like Microsoft Exchange Server or Gmail—can result in invalid signatures.
Multiple DKIM Signatures:
Emails signed by multiple services (for example, Mailchimp and SendGrid in concert) may have conflicts if signature headers aren’t properly ordered or maintained, complicating header analysis and increasing the chance of validation errors.
SPF Record Conflicts:
Although SPF is a separate verification tool, SPF misconfigurations can indirectly cause alignment issues when combined with DKIM under the DMARC protocol, which ties together the authentication results of SPF and DKIM for comprehensive email fraud prevention.
Bounce Management Systems:
Improper handling of bounce messages and auto-replies by outbound email filtering solutions can sometimes result in damaged or stripped DKIM headers.
Identifying DKIM Validation Failures: Tools and Techniques
A systematic approach to diagnosing DKIM signature validation failures includes both manual and automated methods leveraged by IT professionals and email security vendors:
Header Analysis:
Examining raw email headers using email client features (such as in Gmail or Microsoft Outlook) or web-based tools helps identify missing or corrupted DKIM-Signature fields. Header analysis tools offered by Mimecast, Proofpoint Essentials, or LuxSci provide detailed insights into deviations in email headers that may invalidate signatures.
DNS Diagnostics:
Tools like DKIM Core Validator, DomainTools, and the command-line `dig` utility allow administrators to query DNS TXT records and verify correct key publishing. This step is essential to ensure that public keys are accessible and correctly formatted for the selectors in use.
Email Gateway Reports:
Advanced email security platforms—such as Agari, Valimail, Symantec, and McAfee—deliver comprehensive trust verification reports and DKIM status tracking, assisting organizations with continuous monitoring of email compliance and reputation.
SPF and DMARC Integration:
Using DMARC reporting tools provided by providers like Dmarcian and Netcore Cloud offers aggregated visibility into failures tied to both DKIM and SPF, helping correlate validation problems and potentially identify phishing attempts or email spoofing activities.
Testing Environments:
Services like SparkPost and SendGrid enable sending test emails signed with DKIM to various inboxes, including Yahoo Mail, Gmail, and Zoho Mail, allowing evaluation of how recipient servers handle DKIM validation under real-world email delivery conditions.
Deploying automated DNS monitoring and digital signature verification tools, combined with manual header analysis performed by security teams using platforms from Cisco or Trend Micro, equips enterprises to detect and remediate DKIM signature validation failures swiftly, preserving message integrity and strengthening email security.
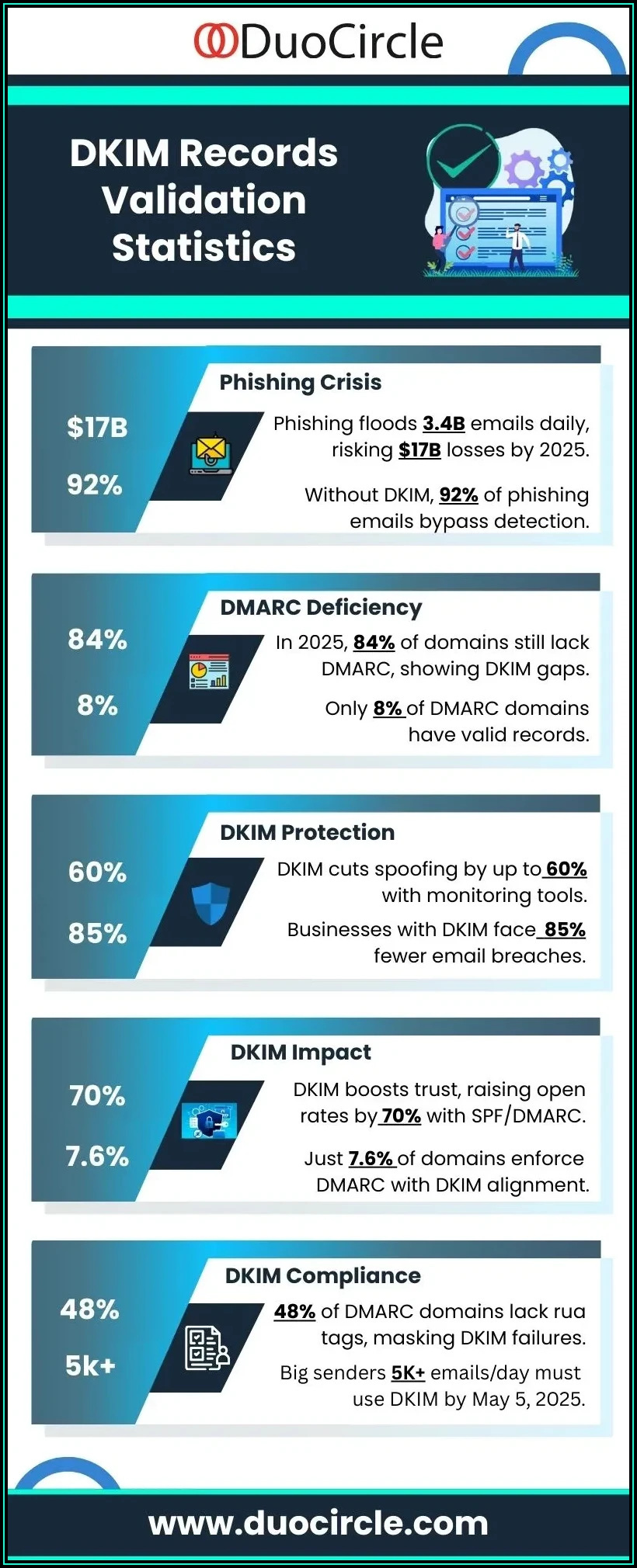
Statistical Data: DKIM Adoption and Validation Failure Metrics
- Over 90% of Fortune 500 companies implement DKIM as part of their email authentication strategy
- Approximately 15% of emails with DKIM signatures fail validation due to configuration or transit modifications
- Domains employing both DKIM and SPF under DMARC see a 75% reduction in phishing-related complaints
- Email spoofing attempts decrease by up to 60% in organizations utilizing comprehensive DKIM monitoring tools
How to Check Your DKIM Records for Correctness
Verifying the accuracy of your DomainKeys Identified Mail (DKIM) records is fundamental to sustaining robust email authentication. This process ensures that your cryptographic signatures and public key infrastructure (PKI) are properly aligned to validate message authenticity, safeguard against email spoofing, and enhance email reputation.
First, review the DNS TXT records where your DKIM public key resides. Tools such as DKIM Core‘s validator, DomainTools, and Google‘s Admin Console can perform DNS lookups to confirm the presence, syntax, and formatting of these records. For organizations using Cloudflare or Microsoft Office 365 for DNS hosting, checking the propagation and correctness is equally critical.
Next, analyze your email headers from outbound messages. This header analysis reveals the presence of a valid DKIM signature, the selector used, and the algorithm for the digital signature. Email clients like Gmail, Yahoo Mail, and Outlook—within Microsoft Exchange Server—display these headers clearly. Additionally, email gateways such as Proofpoint Essentials or Mimecast offer enhanced inbound email filtering that flags DKIM-related discrepancies before messages reach end users. Alongside authentication checks like DKIM, following an email signature guide ensures that your emails not only pass technical verification but also maintain a professional appearance.
Ensuring message integrity and sender authentication via DKIM is a significant layer in the DMARC protocol implementation. Platforms such as Agari and Valimail provide comprehensive dashboards that cross-verify DKIM and SPF record alignments, highlighting potential gaps in message authentication. Using these tools for routine checks aids in proactive email fraud prevention and phishing protection.
Configuring DNS Records Properly for DKIM
Proper configuration of DNS records is critical for DKIM effectiveness. Since DKIM relies on DNS TXT records to publish the public key used for verifying the digital signature, any misconfiguration impairs the mail transfer agent’s (MTA) ability to authenticate the message, potentially harming email security and delivery rates.
When setting up DKIM, ensure your DNS host (Cloudflare, Microsoft, or Google Workspace) allows TXT record entries with the correct selector name, usually in the format `selector._domainkey`. Your DKIM public key must be placed under this subdomain with no extra characters or whitespace, adhering to the standards defined by the DKIM Core specifications.
Email service providers like SendGrid, Mailchimp, and SparkPost simplify this process by automatically generating the required DNS TXT records. However, third-party email gateways or internal mail servers running Postfix or OpenDKIM require manual addition of these entries. Misconfigured DNS records can lead to failed sender policy framework (SPF) checks, DMARC non-compliance, and email delivery challenges.
Regular DNS propagation monitoring, using tools from DomainTools or network diagnostic utilities integrated into Symantec or McAfee security suites, helps identify any propagation delays or conflicts in DKIM DNS record configurations.
Generating and Deploying DKIM Keys Safely
Generating DKIM keys involves creating a cryptographic key pair: a private key maintained securely within your mail transfer agent or email gateway, and a public key published as a DNS TXT record. Key management practices are paramount to maintain the confidentiality of the private key and uphold message authentication integrity.
Industry-standard tools like OpenDKIM or Microsoft‘s Exchange Server DKIM utilities facilitate secure key generation and deployment processes. For cloud-based solutions such as Amazon SES and Microsoft Office 365, key generation often occurs within the platform, with instructions provided for DNS TXT record updates.
Security best practices recommend generating keys with at least 1024-bit encryption, preferably 2048 bits for better protection, to resist brute-force attacks. Since the private key signs outbound emails at the MTA or email gateway level, ensure this key is stored in a highly secure environment with controlled access, consistent with email compliance standards.
By implementing outbound email filtering policies within appliances by Trend Micro, Barracuda Networks, or Cisco, organizations can ensure that only DKIM-signed emails leave their infrastructure, enhancing phishing protection and maintaining email reputation.
Ensuring Email Headers Remain Unchanged During Transit
Preservation of email headers is vital for message authentication because DKIM’s cryptographic signature includes select email headers. Any modification to these headers during email delivery—by MTAs, forwarding systems, or email gateways—can cause DKIM verification failures.
To mitigate this, configure mail transfer agents like Postfix, Microsoft Exchange Server, or outbound filtering systems from Proofpoint or Netcore Cloud, to avoid altering signed headers. Email gateways, particularly those functioning as inbound email filters, must be set to respect the integrity of DKIM-signed headers or resign messages post-modification.
Email protocol compliance within SMTP environments ensures consistent treatment of email headers across hops. Monitoring bounce management data and header analysis logs using tools like Dmarcian or Valimail enables identification of where header modifications may compromise message authentication.
For organizations employing multiple email clients—Gmail, Yahoo Mail, Zoho Mail—consistency in header handling during forwarding or mailing list distribution is essential to prevent inadvertent DKIM and SPF alignment issues.
Resolving Alignment Issues Between DKIM and SPF Records
Effective email fraud prevention mandates the correct alignment of DKIM and SPF records as specified in the DMARC protocol. Misalignment occurs when the domain in the DKIM signature or SPF “MAIL FROM” does not match the domain in the “From” header, causing trust verification failures and increased email delivery failures.
To resolve these issues, administrators should audit their SPF record thoroughly, ensuring that all mail sources—whether internal MTAs or third-party services like SendGrid, Mailchimp, or SparkPost—are included in the SPF record. SPF misconfigurations may inadvertently block legitimate emails, despite correct DKIM signatures.
Conversely, the DKIM selector and signing domain must align with the domain used in the email client and DMARC policy. Organizations using Microsoft Office 365 or Google Workspace frequently leverage integrated DKIM and SPF management tools to maintain alignment and assure email security.
Regular header analysis through inbound email filtering solutions like Proofpoint or Mimecast can detect alignment discrepancies early, guiding necessary adjustments in public key infrastructure or sender policy framework entries.
Updating or Rotating DKIM Keys Without Causing Failures
Key rotation is a critical aspect of maintaining email security and message authentication hygiene. Regularly updating DKIM keys reduces the risk of key compromise while supporting ongoing email fraud prevention and phishing protection.
To update keys without causing failures in email delivery, adopt a phased deployment strategy. Begin by publishing a new DKIM public key under a new selector in DNS TXT records via your DNS provider, such as Cloudflare or Microsoft DNS. Using DNS management tools, verify new key propagation before configuring the mail transfer agent or email gateway to start signing outgoing emails with the new private key.
During this overlap period, maintain the old DKIM key active to validate emails sent before the transition, ensuring uninterrupted trust verification. Communications from vendors like Agari and Dmarcian recommend notification of receiving domains and email clients if feasible, especially for high-volume senders (Google, Microsoft) to prevent bounce management issues.
Automated DKIM key management features offered by LuxSci or Netcore Cloud help streamline this process in complex environments, preventing outages caused by DNS propagation delays or email protocol inconsistencies. Keeping thorough logs and performing post-rotation header analysis assists in fine-tuning configurations for optimal email delivery and security compliance.
Best Practices for Testing DKIM Signatures Before Deployment
Before fully integrating DomainKeys Identified Mail (DKIM) into your email infrastructure, it’s crucial to rigorously test the cryptographic signatures to ensure proper message authentication and email delivery. Testing DKIM signatures helps maintain message integrity, supports sender authentication, and reduces the risk of email spoofing and phishing protection failures.
One of the best practices is to begin by publishing DKIM public keys as DNS TXT records in a controlled subdomain. This approach allows IT administrators to verify the signing process through header analysis without impacting the primary email flow or email reputation. Tools such as DKIM Core and services offered by Dmarcian enable IT teams to validate DKIM signature generation and verification processes against the public key infrastructure.
Testing should leverage mail transfer agents like Postfix, Microsoft Exchange Server, or open-source options like OpenDKIM, integrating with SMTP protocols that facilitate outbound email filtering. Using controlled outbound email samples sent through services like SendGrid, Amazon SES, or SparkPost can simulate real-world email delivery scenarios. These tests verify that digital signatures in email headers align with the published DKIM DNS entries.
Furthermore, testing environments should include multiple email clients such as Gmail, Yahoo Mail, Zoho Mail, and Microsoft Office 365 to ensure widespread compatibility regarding inbound email filtering and trust verification. Many Email Gateway products from Proofpoint, Barracuda Networks, and Mimecast offer DKIM diagnostic features to analyze message authentication failures before deployment.
Integrating SPF record and DMARC protocol testing alongside DKIM evaluation is critical. This combined approach improves the accuracy of sender policy frameworks and enhances email fraud prevention and compliance monitoring. Additionally, leveraging bounce management systems during testing ensures that any issues with DKIM signature validation don’t escalate into email delivery failures or brand trust impact.
Handling DKIM Failures in Major Email Service Providers
Despite rigorous testing, DKIM failures can occur in production environments, particularly given the complexity of DNS TXT records and public key infrastructure management. Major email service providers like Google, Microsoft, and Cisco have developed sophisticated inbound email filtering mechanisms to detect and handle DKIM signature validation issues effectively.
For instance, Gmail applies strict header analysis policies that assess digital signatures and message authentication data in real-time, which helps prevent email spoofing and phishing attacks. When a DKIM check fails, Gmail relies on the reputation of the sending domain, SPF record alignment, and DMARC policy enforcement to decide whether to mark an email as spam or reject it outright. Outlook and Microsoft Office 365 employ similar processes where the Exchange Online Protection gateway enforces DKIM compliance coupled with SPF and DMARC protocols to optimize email security.
To resolve DKIM failures within these ecosystems, organizations should begin by reviewing the DNS TXT records and ensure the selector and domain align. Tools like DomainTools and Cloudflare can assist in DNS propagation analysis, confirming that the hashes generated by the signing private key correspond with the public key entries.
In scenarios where signed emails fail header analysis, examining Email headers manually or by leveraging solutions such as Proofpoint Essentials or Agari may reveal issues related to the mail transfer agent configuration or header modifications during outbound email filtering.
Additionally, feedback loops and bounce management offered by providers like Trend Micro and Symantec help IT teams track affected email clients or gateways, making it easier to pinpoint breakdowns in sender authentication or message integrity processes.
Monitoring and Maintaining DKIM to Prevent Future Failures
Ongoing monitoring and maintenance are pivotal to sustaining DKIM effectiveness and preventing unforeseen failures. Continuous trust verification, email compliance checks, and real-time header analysis contribute to strong email reputation and email fraud prevention.
Organizations can implement automated monitoring tools provided by Dmarcian and Valimail that track DKIM signature validation results and correlated SPF and DMARC status flags. These tools use extensive data analytics to flag anomalies indicating misconfigured DNS TXT records, compromised cryptographic keys, or mail transfer agent issues.
Routine audits of DKIM selectors and private key rotations should be scheduled to strengthen the public key infrastructure and reduce vulnerabilities related to digital signature expiration or key leakage. Integrating these practices within email protocol workflows handled by email gateways such as Mimecast and Barracuda Networks safeguards against message authentication degradation.
To complement DKIM, reinforcing SPF record policies and DMARC protocol enforcement ensures holistic email security. Advanced message authentication frameworks also support inbound and outbound email filtering where suspicious email headers or message anomalies can trigger alerts or automatic quarantine, preventing email spoofing and phishing attacks.
Cloud-based email systems like Google Workspace and Microsoft Office 365 provide centralized dashboards for DKIM monitoring, allowing IT administrators to manage compliance, bounce management, and trust verification from a unified interface. These platforms also facilitate incident response coordination by integrating with security information and event management infrastructures.
FAQs
What is the importance of DNS TXT records in DKIM implementation?
DNS TXT records store the public key necessary for verifying DKIM cryptographic signatures in outgoing emails. Proper configuration ensures that recipient servers can perform message authentication and protect against email spoofing.
How do SPF and DMARC protocols complement DKIM?
SPF records specify authorized mail servers for a domain, while DMARC enforces policies combining SPF and DKIM results. Together, they enhance trust verification, phishing protection, and email fraud prevention.
Can DKIM failures affect email delivery to major providers like Gmail or Microsoft?
Yes, DKIM failures may result in messages being marked as spam or rejected by inbound email filtering systems used by providers such as Google Workspace, Microsoft Office 365, and Yahoo Mail, impacting email reputation.
What tools assist in monitoring DKIM status post-deployment?
Services like Dmarcian, Valimail, and Proofpoint Essentials offer automated monitoring, real-time DKIM validation reporting, and integration with bounce management systems, supporting ongoing email compliance.
How often should DKIM cryptographic keys be rotated?
It is recommended to rotate DKIM keys periodically, typically every 6-12 months, to maintain email security and minimize risks from potential key compromise within the public key infrastructure.
Key Takeaways
- Rigorous testing of DKIM signatures using DNS TXT records and header analysis is essential before deployment to ensure message integrity and sender authentication.
- Major email providers like Google and Microsoft enforce DKIM compliance alongside SPF and DMARC through inbound email filtering and reject or quarantine emails failing message authentication.
- Continuous monitoring and maintenance with tools from Dmarcian and Valimail help prevent DKIM failures, support bounce management, and protect overall email reputation.
- Real-world case studies highlight how resolving DKIM validation failures requires collaboration among mail transfer agents, DNS management, and email gateways for robust email security.
- Integrating DKIM with SPF record and DMARC protocol forms a comprehensive framework for phishing protection, email fraud prevention, and email delivery optimization.