Logitech Data Breach, Mass Router Hijack, Android Trojan Sturnus – Cybersecurity News [November 17, 2025]
Here are this week’s cybersecurity updates, bringing you headlines that made news around the world. Princeton University reported a data breach impacting alumni and donors, and the Clop extortion gang’s activity continued, with Logitech confirming data theft linked to a third-party zero-day.
Meanwhile, Operation WrtHug has silently hijacked over 50,000 outdated ASUS routers globally, and a dangerous new Android trojan called Sturnus has emerged, one that can entirely bypass end-to-end encryption on secure messaging apps. There’s also news of an actively exploited RCE flaw in 7-Zip that requires immediate patching. Here’s what is happening in the cybersecurity world and how you can protect yourself!
Logitech Confirms Major Data Breach Linked to Notorious Extortion Gang
Hardware giant Logitech International S.A. officially confirmed a data breach this week where threat actors made away with sensitive information in a zero-day cyberattack.
The attackers exploited a weakness in a third-party software platform, suspected to be the same zero-day flaw in the Oracle E-Business Suite that the Clop gang previously leveraged in their massive data-theft campaign over the summer. The organization filed with the U.S. Securities and Exchange Commission (SEC) to confirm the incident, which occurred despite the zero-day vulnerability being patched as soon as the fix became available from the vendor.
Clop has since added Logitech to its public data-leak site, threatening to release nearly 1.8 terabytes of allegedly stolen data. Logitech carried out an internal investigation and shared that the employee, consumer, customer, and supplier data is at risk, but there is no personal data, such as national ID numbers or credit card information, at risk.
The investigation is still active, and Logitech is managing the fallout, so consumers should remain vigilant against targeted phishing attempts.
Mass Router Takeover: Operation WrtHug Hijacks 50,000+ Outdated Routers
Researchers have uncovered a wide-ranging operation that has pulled tens of thousands of outdated ASUS routers into a single network. Most of the activity has been seen in Southeast Asia, North America, and some parts of Europe.
SecurityScorecard’s STRIKE team has labeled the activity Operation WrtHug. Their review suggests the attackers are leaning on several older, publicly known vulnerabilities in end-of-life ASUS WRT models to gain control of devices that are no longer supported. Over the past half-year, more than 50,000 unique IPs tied to compromised routers have been logged.
All affected units were presenting the same self-signed TLS certificate. Nearly every service using that certificate was tied to ASUS AiCloud, a feature meant to give remote access to local storage. According to the report, the intruders appear to use privilege-escalation flaws in AiCloud to take over these routers.
While the operators behind WrtHug haven’t been identified, the concentration of infections in Southeast Asia and the technical similarities to earlier Asia-nexus campaigns point to a possible link. Owners of older ASUS routers should consider replacing unsupported models and updating to the newest firmware available for their specific device.
New Android Banking Trojan ‘Sturnus’ Can Read Encrypted Messages
Sturnus is a new Trojan possessing advanced capabilities to bypass end-to-end encryption on apps like Signal and WhatsApp and achieve complete remote control of a compromised device for financial fraud.
It is currently under testing, but fully functional and already targeting financial institutions across Europe using region-specific overlay templates to steal banking credentials. The infection begins when a user downloads a malicious Android Package Kit (APK) file, which is often disguised as a legitimate application like Google Chrome or Preemix Box. Once installed, it immediately registers with its command-and-control (C2) server through a cryptographic exchange, establishing both an encrypted HTTPS channel for commands and data exfiltration and an AES-encrypted WebSocket channel for real-time Virtual Network Computing (VNC) operations.
Sturnus gains extensive control over victim devices and can read all on-screen text, monitor inputs, and detect app launches. It can also perform actions like clicking buttons or injecting text to navigate the phone. It uses these permissions to monitor secure messaging apps (WhatsApp, Telegram, and Signal) by reading the screen after the legitimate app has decrypted messages.
The solution to this is simple. Just avoid downloading APKs from outside the official Google Play Store, and keep Google Play Protect active.
7-Zip Hit by Actively Exploited RCE Vulnerability (CVE-2025-11001)
This week, a critical remote code execution flaw (CVE-2025-11001) was discovered in the popular file archiver 7-Zip and is now being actively exploited in the wild.
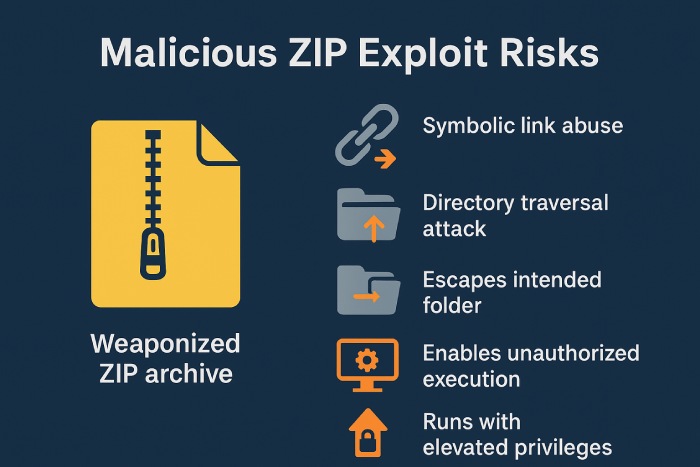
The vulnerability was assigned a CVSS score of 7.0 and works within how 7-Zip handles symbolic links inside ZIP archive files. Basically, threat actors can craft a malicious ZIP archive that exploits this flaw to allow the extraction process to traverse outside its intended folder. This directory traversal can ultimately enable threat actors to execute unauthorized code on the infected system, running it with the privileges of a service account or an elevated user.
Security researchers Ryota Shiga (GMO Flatt Security Inc.) and Takumi-san.ai initially reported the issue, but there’s also a publicly available proof-of-concept (PoC) exploit by another researcher, Dominik (aka pacbypass). All 7-Zip users should immediately update to version 25.00 or later to prevent potential attacks, as active exploitation of this serious flaw is confirmed.
Princeton Data Leak Exposes Alumni and Donor Contact Records
Princeton University says one of its databases was accessed by an outside party earlier this month after a staff member fell for a phishing email.
The breach was spotted on November 10 and involved a system tied to alum relations and fundraising activity. According to the school, the attackers were able to reach a collection of routine contact records that Princeton has gathered over decades. These entries included names, phone numbers, email addresses, and mailing addresses connected to alums, donors, current students, parents, and faculty and staff from different periods. Relatives of alums were listed as well.
University officials stressed that this database wasn’t linked to financial records, passwords, or federally protected student files, and that employment data wasn’t involved unless the employee happened to be a donor. Princeton says it cut off access once the activity was noticed and has not seen signs that the intruders moved to any other systems. When asked for the number of individuals affected or whether any demands were made, the school referred all questions back to its FAQ.
Anyone who might have been swept into this should be careful with emails or calls that claim to be from the university and ask for personal details.