Askul Ransomware Disruption, Qilin Targets Habib, Google Exposes Malware – Cybersecurity News [November 03, 2025]
This week saw a surge in major cyber incidents worldwide. A ransomware attack crippled Japan’s Askul retail network, Qilin claimed Habib Bank AG Zurich, and Google uncovered AI-powered malware that rewrites its code. Cisco issued urgent fixes for firewall exploits, while Oglethorpe and NMHC disclosed healthcare data breaches.
Ransomware Attack on Askul Disrupts Japan’s Retail Supply Chain
Japanese retailer Askul has stopped online orders and product shipments after a ransomware attack incapacitated its systems, disrupting several major retail partners that rely on its logistics network. The Tokyo-based company discovered the breach over the weekend, forcing it to shut down operations across its three e-commerce platforms, including Askul for office supplies, Lohaco for household goods, and Soloel Arena for corporate clients. All new orders and user registrations have been paused, existing shipments cancelled, and customer inquiries temporarily disabled. Askul said it is still investigating the scale of the incident, including whether any personal or customer data was compromised. The attack has also caused a ripple effect across Japan’s retail sector.
Muji, which depends on Askul’s logistics arm, has halted domestic online sales and parts of its mobile app, although physical stores remain unaffected. Other retailers, including Loft and Sogo & Seibu, have also faced service disruptions connected to Askul’s logistics network. The breach comes when a surge of cyber incidents is happening across Japan. Earlier in November, Asahi Group Holdings confirmed a ransomware attack by the attackers that disrupted production, while Sagawa Express reported unauthorized logins to customer accounts linked to stolen credentials. The wave of attacks shows how ransomware and data theft continue to challenge Japan’s critical business operations.
Qilin Ransomware Gang Claims Habib Bank AG Zurich as Latest Victim
The Switzerland-based Habib Bank AG Zurich is the latest victim to show up on the Qilin ransomware gang’s dark web site. The group claims to have stolen around 2.5 terabytes of data, including nearly two million files. To back up its claims and pressure the bank to negotiate, the gang has posted screenshots said to come from the stolen data. Researchers at Cybernews, who reviewed the samples, noted that they appear to include customer account details such as passport numbers, balances, and transaction records. The attackers also say they nabbed source code for internal tools, which raises alarms about potential security flaws in the bank’s systems.
Habib Bank, which operates in several countries, hasn’t commented on the breach yet. The Qilin ransomware group has been active since 2022 and has become one of the most prolific gangs out there, targeting hospitals, manufacturers, and major companies like Volkswagen Group France and Nissan. This incident is just the latest in a growing list of cyberattacks hitting the global financial sector, as groups like HSBC USA and Jordan Kuwait Bank have also recently suffered data breaches, showing that financial institutions are still prime targets.
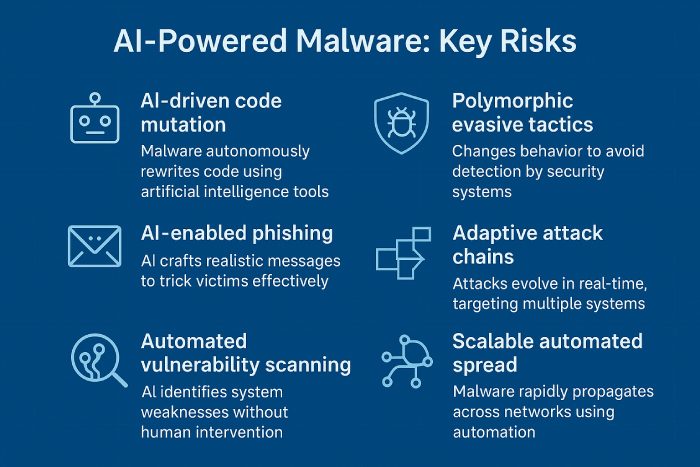
Google Uncovers AI-Powered Malware That Rewrites Its Own Code
Google just spotted a new experimental malware called PROMPTFLUX, and it’s pretty concerning. It actually uses Google’s own Gemini AI model to rewrite its code, making it better at hiding from antivirus software. The VBScript malware pings the Gemini API to ask for code changes and then generates new versions of itself, saving them in the Windows Startup folder to stick around. Researchers think PROMPTFLUX is still in development, since its self-changing feature isn’t active yet. Still, its design points to a new phase of AI-powered malware that can evolve in real time.
Google says the attackers seem financially motivated and are testing AI-driven replication. But they’re not the only ones. The company is also seeing other AI-powered malware, like FRUITSHELL, PROMPTLOCK, and QUIETVAULT, using large language models to create or change code on demand. Beyond just experimental tools, Google has tracked several state-linked groups using generative AI for phishing, data theft, and building malware. The company warns that this shows a shift toward fully integrated, automated cyber operations. As more hackers experiment with generative AI, Google expects these tools will become standard for building large-scale, adaptive attacks.
As cyberattacks surge worldwide, implementing strong email security through SPF, DKIM, and DMARC is crucial to defend against spoofing, phishing, and evolving AI-driven threats.
Cisco Issues Urgent Fixes After Fresh Firewall Exploitation Detected
Cisco has warned that attackers are now exploiting a new variant of attacks targeting its Secure Firewall (ASA) and Threat Defense (FTD) software. This campaign affects devices vulnerable to two recently disclosed flaws, CVE-2025-20333 and CVE-2025-20362. The company says the exploit can cause unpatched devices to reload unexpectedly, resulting in a denial-of-service (DoS). Cisco is urging customers to apply the latest patches right away to avoid potential disruption.
As per the UK’s National Cyber Security Centre, these flaws were already being used as zero-days in attacks that deploy malware like RayInitiator and LINE VIPER. The first bug lets attackers run code remotely, while the second allows unauthorized access to restricted URLs. Cisco also released fixes for two critical flaws in its Unified Contact Center Express platform that could let attackers upload files, bypass authentication, and run commands with root privileges. They also patched a high-severity DoS flaw in the Identity Services Engine that could allow attackers to repeatedly restart affected systems.
Oglethorpe and NMHC Report Data Breaches Linked to Cyber Incidents
Two U.S. healthcare providers have just reported separate data breaches. Tampa’s Oglethorpe, which runs mental health and addiction recovery centers in Florida, Louisiana, and Ohio, had a cyber incident that disrupted its systems between May 15 and June 6, 2025. Investigators confirmed attackers stole files with patient Personally Identifiable Information (PII), including names, birth dates, Social Security numbers, driver’s license details, and medical info. This breach hit 92,332 people, including 85 in Maine. Oglethorpe says it hasn’t seen any data misuse yet, but it’s offering 12 months of free credit monitoring and has rebuilt its systems to boost security.
In a separate case, Northern Montana Health Care (NMHC) said it was impacted by a breach at its debt collection partner, Wakefield & Associates. The good news is that the problem was limited to Wakefield’s network, and no NMHC systems were affected. Wakefield is notifying the affected individuals directly and offering them credit monitoring and identity protection. The total number of patients impacted hasn’t been confirmed yet. As of now, neither of these breaches has popped up on the HHS Office for Civil Rights portal.