How cybercriminals use DNS hijacking to bypass DMARC policies
Email authentication protocols like SPF, DKIM, and DMARC are supposed to stop attackers from pretending to be you and dupe your clients. But what if they target the very system that these protocols depend on?
Here, we are talking about the DNS.
Your DNS is essentially your domain’s control centre, from which you can manage all authentication protocols, such as your SPF record, DKIM public keys, DMARC policy, and any other instructions that tell the internet how to treat your emails. Now, if attackers get access to this control room, they can practically take over your entire email identity. All they need to do is make a few changes without you knowing, and the entire foundation of your email ecosystem starts working for them instead of you. This is called DNS hijacking.
So, basically, instead of sliding into your clients’ inboxes as a suspicious or unauthenticated sender, they make their way in as someone who looks completely legitimate. Let’s dig deeper to understand how they pull it all off and what this means for your domain.
How do attacks hijack your DNS and rewrite authentication records?
Since the entire control of all your email activity lies in the DNS, the attackers know that if they can gain access to your DNS account, they can easily change the entire configuration of your domain. This includes how your emails are checked and verified by receiving mail servers.
For these attackers, getting into your DNS is no longer tricky. They usually get in by installing malware that changes DNS settings, breaking into unsecured routers, intercepting DNS requests, exploiting DNS server flaws, poisoning DNS caches, or stealing DNS account credentials to edit the records directly. And once they are in, all they have to do is edit the records that control your authentication protocol, and the control shifts to their side.
After that, they can decide which servers are allowed to send emails as your domain, replace your DKIM key with their own, or loosen your DMARC policy. Once these changes are saved, any email they send using your domain will pass all checks and look completely valid to the receiving server.
How does DNS hijacking help attackers bypass SPF, DKIM, and DMARC?
Once attackers gain control of your DNS, they go after the most critical target—your email authentication protocols. These cybercriminals know that manipulating your authentication protocols can cause the most significant damage and, more importantly, allow them to gain access to your recipients’ inboxes without raising any eyebrows.
Here’s how they take advantage of DNS changes to bypass SPF, DKIM, and DMARC and make their emails look completely legitimate.
Adding their sending servers to the SPF record
When attackers get access to your DNS, they go straight for the SPF record. These cybercriminals add their own servers to the list of authorized senders in the SPF record. Once their server is added, any email they send using your domain will pass the SPF check because the receiving mail server sees their server as “allowed.” This makes their fake emails look completely valid from the SPF point of view.
Replacing your DKIM public key
The primary goal of cybercriminals when hijacking your DNS is to deceive receiving servers into thinking the fraudulent email is from you, an authorized sender. To make that happen, they replace your authentic DKIM public key with one that belongs to them. Once this is done, any email they send, signed with their matching private key, will pass DKIM verification without any issues. So, when the receiving server gets an email, it checks the DKIM signature against the public key stored in the DNS. Since the attacker has replaced your key with their own, the signature matches perfectly. As a result, the email is treated as legitimate, even though it was sent by the attacker.
Making DMARC pass automatically
Since DMARC is built upon SPF and DKIM, it wants at least one of these checks to pass and align with the “From” domain. Once attackers manipulate your DNS and make both SPF and DKIM point to their infrastructure, DMARC has no reason to mark these emails as suspicious. So, when the receiving server looks up your DNS, sees that the SPF record approves the attacker’s server and that the DKIM signature matches the key stored in DNS, it treats the email as fully compliant.
Weakening or disabling your DMARC policy
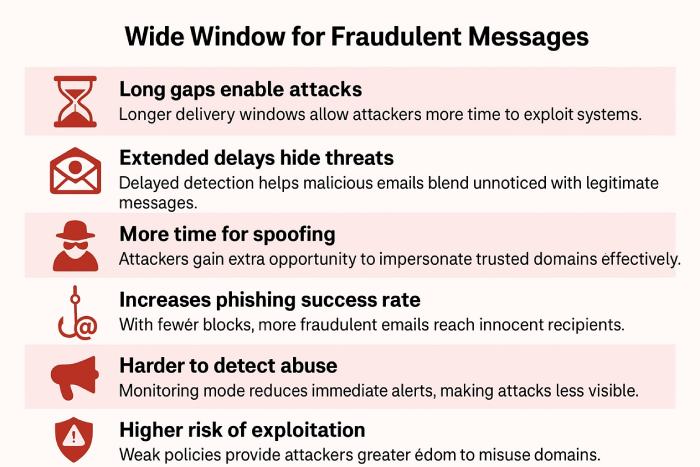
Attackers leave no opportunity to weaken your domain’s protection. Once inside your DNS, they can simply change your DMARC policy to a less strict setting, such as p=none. When your DMARC policy is set to monitoring mode, instead of enforcement mode, suspicious emails are still delivered to the inbox. This gives attackers a wide window to send fraudulent messages using your domain without being blocked or quarantined.
What does this mean for your domain and recipients?
When attackers hijack your DNS and bypass authentication protocols, their impact will be felt by both you and your recipients. Since your domain now appears to send fake emails under the garb of legitimate ones, your recipients can easily fall for scams, share sensitive information, or click on harmful links, thinking the email is from you. While all of this is happening, your domain’s reputation will also go for a toss, and email providers will start blocking or filtering even your genuine emails. All of this affects your communication, weakens trust in your brand, and creates a long-lasting risk for you and everyone who relies on your domain.
What should you do?
Now that you know how DNS hijacking can affect your business and your clients, and your email security it’s important that you take the right measures before it’s too late. Start by securing access to your DNS and monitoring your DNS records regularly for any changes you did not authorize. It is also a good idea to implement DNSSEC for added protection.