This is the 4th edition of January, and last week witnessed multiple ups and downs in the cybersecurity ecosystem. Microsoft turned out to be the most mimicked brand in the last quarter of 2025, while experts realized the imminent cyber threat during the Winter Olympics. A West London council was targeted by hackers, leading to a breach of sensitive personal data. Meanwhile, a group of experts has stated that 2026 is going to witness highly sophisticated social engineering tactics over vulnerability-oriented cyberattacks.
Key data breach trends in 2026
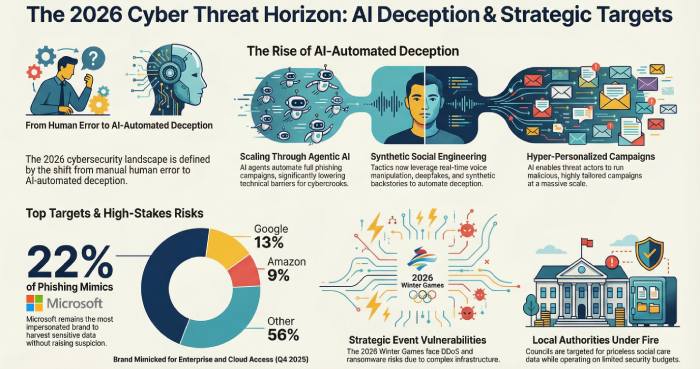
Cybersecurity experts believe that AI-backed social engineering tactics might be the new favorite among cybercrooks in 2026. The CEO at HYPR, Bojan Simic, has stated that “what once targeted human error now leverages AI to automate deception at scale.” He believes that cybercrooks are all set to leverage techniques like video manipulation, deepfakes, real-time voice manipulation, synthetic backstories, and so on.
Experts feel that while the social engineering basics will remain the same, cybercrooks will simply refine them to improve quality, increase speed, and scale the process.
With the help of artificial intelligence, threat actors will be able to run hyper-personalized malicious campaigns at a huge scale.
They believe that the agentic AI can be the game-changer for these cybercriminals.
It is highly likely that with the help of AI agents, hackers seamlessly run full-fledged phishing campaigns without requiring any manual intervention. It is because of these advanced AI agents that the technical barriers are significantly lowered, enabling more and more cybercrooks to join the bandwagon.
Deploying high-end, enhanced detection tools is the only key to safeguarding businesses and their data from AI-backed social engineering attacks. The world immediately needs better deepfake detection tools. Besides, intricate people processes can also be helpful.
Microsoft- The most mimicked brand in Q4 2025 phishing attacks!
As per research, Microsoft was the most mimicked brand in Q4 2025 phishing attempts. Around 22% of phishing attempts have unabashedly imitated Microsoft to carry out their malicious campaigns. This is not the first time that Microsoft turned out to be the hackers’ favorite.
Microsoft continues to be a top pick among threat actors as a renowned and trusted brand that enables them harvest sensitive user data conveniently without raising much suspicion.
Google ranked second with 13% of the share, and Amazon ranked third with 9% of the share. Facebook, too, has joined the list after a long time, and managed to be in the fifth position.
Hackers primarily targeted the technology sector to run brand phishing campaigns in Q4 2025. This clearly hints towards the fact that cybercriminals are more interested in gaining enterprise access, identity platforms, and cloud services.
The Milano Cortina Winter Games are on the radar of threat actors!
The much-awaited winter games are all set to begin on February 6. However, not only the athletes but also the threat actors are keenly awaiting the global event. Cybersecurity experts have already warned of potential risks, including Distributed Denial-of-Service (DDoS) attacks, ransomware, and disruptions to digital infrastructure.
A threat assessment report claims that there are multiple factors that make this event a treasure trove of opportunities for threat actors. While visitors like business leaders, A-listed celebs, and politicians make this event a high-profile one, the intricate infrastructure setup (ticketing systems, water and power utilities, point-of-sale terminals, etc.) makes this event all the more susceptible to cyber mishaps. The not-so-pleasant geopolitical climate nowadays can also significantly add fuel to the fire.
Experts believe that organizers and all the major stakeholders must be well-prepared to combat nation-state groups, hactivists, and financially motivated cybercrooks.
Personal data compromised because of the recent cyberattack on the West London council
The Kensington and Chelsea Council was recently targeted by threat actors. The council spokesperson has stated that the cyberattack was carried out with “criminal intent” and that the threat actors have managed to get access to sensitive data.
The cybersecurity team jumped into action immediately and successfully managed to limit the extent of the damage. The West London Council has already informed the Information Commissioner’s Office about the cyber mishap.
Graeme Stewart, a cybersecurity expert, believes that local authorities are the favorite targets of hackers because of the type of activities they carry out on a regular basis. Generally, local authorities are responsible for offering social care. They also manage housing and other relevant records. That’s exactly what the cybercrooks come running after– the priceless data!
Besides, local authorities are mostly running on limited budgets. That’s why they tend to have weak cybersecurity mechanisms, which make them easy targets for threat actors.
The targeted London Councils are working closely with the National Cybersecurity Center to nab the perpetrators and monitor the compromised data.