7 reasons why DKIM fails and how to fix it
Sometimes your email just doesn’t reach its recipient. You’ve done everything right— crafted the perfect message, sent it to the correct address, and even authenticated your domain with email authentication protocols. Yet, it gets flagged or doesn’t even land in the receiver’s mailbox.
There could be many reasons that this happens, but one of the most common and overlooked ones is a failed DKIM (DomainKeys Identified Mail) check.
DKIM is one of the three major email authentication protocols (along with SPF and DMARC), which help verify the integrity and authenticity of your email. Speaking of DKIM, it ensures that your emails haven’t been altered in transit and that they truly come from the domain they claim to. When DKIM fails, it tells the receiving servers that something might be wrong with the incoming message, so it’s best to withhold the message or mark it as suspicious. Although it is a behind-the-scenes step, it directly affects your deliverability, especially if you’re sending the emails to a large audience.
In this article, we will look at the seven most common reasons why DKIM fails — and how to fix them so your emails can land exactly where they’re supposed to: the inbox.
What happens when DKIM fails?
DKIM essentially vouches for your outgoing emails to the receiving server by attaching a cryptographic signature that proves your domain authorized the message and hasn’t been tampered with in transit.
If the receiving server doesn’t get this assurance because the signature is missing, broken, or can’t be verified, it thinks the message might be fake or changed. As a result, the server may mark the email as suspicious, send it to the spam folder, or even reject it outright, especially if your domain has a strict DMARC policy in place.
Why does this happen?
If an email fails DKIM, it means the public and private keys didn’t match, and the receiving server couldn’t verify that the message really came from your domain or that it wasn’t changed along the way. This mismatch can happen because of various reasons; here are some of them:
You haven’t configured DKIM at all
If you haven’t set up DKIM at all— haven’t added the required keys or the protocol is disabled for your email service provider, your emails won’t have a DKIM signature. So when the receiving server tries to verify your email, it won’t find anything to check, and the email will likely fail DKIM authentication.
There are problems with the setup
Another reason your email might fail DKIM is incorrect setup. Chances are, you might have configured DKIM manually, without using a proper DKIM record generator, which can lead to errors in the public key format, selector name, or DNS entry.
Even the slightest mistake, like missing characters or poor formatting, can break the record and make the signature unverifiable by the receiving server.
The headers are missing
When you implement DKIM, it doesn’t sign just the body of your email to verify the integrity of its contents; it also signs specific email headers. These are listed under the h= tag in the DKIM signature. For instance:
DKIM-Signature: v=1; a=rsa-sha256; c=relaxed/relaxed; d=yourdomain.com;
s=myselector; h=from:to:subject:date:message-id; bh=base64_body_hash;
b=base64_signature;
Here, even if one of these headers, like “From,” “To,” “Subject,” “Date”, or “Message-ID,” is missing or altered by the time the email arrives, the server won’t be able to match the signature with the expected hash. This causes the DKIM check to fail.
There is no public key
If you have configured DKIM but haven’t added the public key to your DNS, the receiving server won’t be able to verify your email’s signature. For DKIM to do its job, you need both keys— a private key (used to sign the email) and a public key (stored in DNS for verification). And often, most teams simply forget to publish the public key or assume the email service provider has done it for them, which causes DKIM to fail.
Issues in server communication
Sometimes, the problem might not be at your end, but at the server’s end. Even if your DKIM setup is correct, temporary DNS lookup failures, timeouts, or network issues on the receiving server’s end can prevent the server from retrieving your public key or verifying your DKIM signature, ultimately causing DKIM to fail.
The message was modified
If your outgoing message was altered in transit to the recipient, the DKIM signature can break. If even a single character changed along the way, the receiving server won’t be able to match the hash with the original signature, and the DKIM check will fail. This usually happens when emails pass through forwarding services, mailing lists, spam filters, or antivirus tools, which might add footers, change headers, or reformat content without you knowing.
The DKIM keys expired
For DKIM to work properly, it is important that you rotate the keys regularly and keep both the private key (used to sign your emails) and the public key (published in your DNS) in sync. If the keys are outdated, expired, or no longer match, the receiving server won’t be able to verify your email’s signature, and the DKIM check will fail.
How to fix DKIM failure?
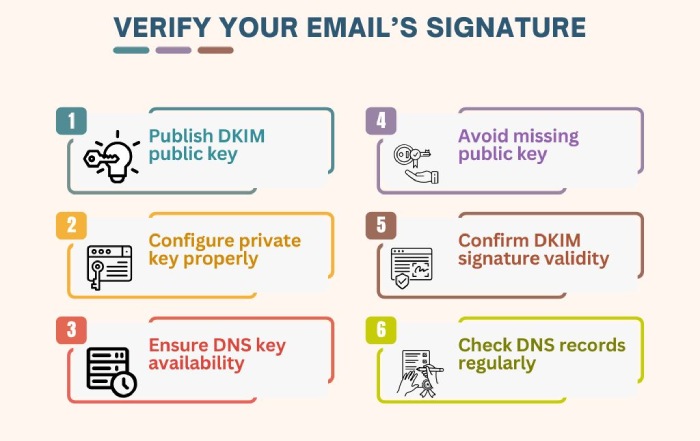
Here’s how you can fix the DKIM failure issue:
- Enable DKIM in your email provider settings
- Add the public key to your DNS under the correct selector
- Instead of typing everything manually, use a DKIM record generator to avoid formatting mistakes
- Sign all required headers and use relaxed/relaxed canonicalization
- Rotate your keys regularly and update the new ones on the DNS
- Avoid services that modify emails after sending
- Test your DKIM setup
Do you need help implementing DKIM? It’s best if you don’t try to do it manually. Reach out to DuoCircle to get started with error-free DKIM setup.