Configuring DKIM to sign mail from your Microsoft 365 domain
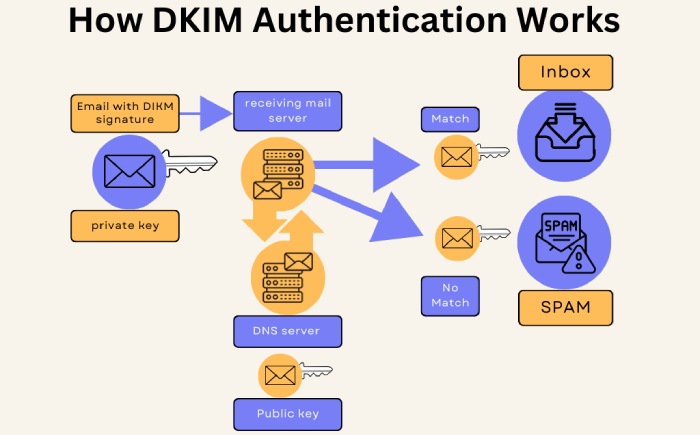
The main purpose of DKIM is to verify whether a malicious entity tampered with email content in transit. To ensure this, a pair of public and private keys are produced for your domain and used by the source email systems to digitally sign the headers of outgoing messages. This digital signature remains valid until intermediate email systems modify the signed part. The d= value represents the signing domain in the header field.
The public key corresponding to your domain is stored as a CNAME record in Microsoft 365. Please note that most other email systems save them as a TXT record.
The recipients’ email servers use the d= value in the header field to identify the signing domain and find your domain’s DKIM public key in the DNS. After retrieving the public key, both private and public keys are matched– DKIM passes if the keys align; otherwise, it fails.
General facts about DKIM
Here are two general yet important facts about DKIM-
- The DKIM signing domain does not need to match the domain in the MAIL FROM or FROM addresses in the email; they can be different.
- An email can have multiple signatures by different domains. Many hosted email services first sign messages using their own domain. After the customer sets up DKIM signing for their domain, the messages are signed again using the customer’s domain.
DKIM in Microsoft 365 based on your email domain
For MOERA users
Microsoft itself takes care of public keys for Microsoft Online Email Routing Address or MOERA domains. There will be a 2048-bit pair of public and private keys, and all the outgoing emails are signed using the respective private key.
However, you are free to manually set up DKIM signing using the .onmicrosoft.com domain.
For custom domain users
Microsoft automatically signs all the outgoing emails, however, there are still a few things that you need to take care of-
- For DKIM to pass DMARC validation, the domain signing the message and the domain in the From address must match.
- For third-party email services (like bulk email services), use a subdomain instead of your main domain. This prevents issues with these services from affecting your main domain’s reputation. Remember, each domain has to have its own DKIM configuration.
- Do not publish DKIM records for registered but unused (parked) domains. This prevents forged domains from passing DKIM validation.
- To fully protect your custom domains, configure SPF and DMARC along with DKIM as part of your email authentication strategy.
Configuring DKIM signing in Microsoft 365
When you turn on DKIM signing using a custom domain, the signing process switches from using the .onmicrosoft.com domain to the custom domain. You may use a custom domain or subdomain for this process only when the domain is added to Microsoft 365.
To follow the steps mentioned below, you need to first check that the custom domain or subdomain is appearing on the DKIM tab of the email authentication page.
You will come across a details flyout, where you need to ensure the following-
- The ‘Sign messages for this domain with DKIM signatures’ toggle is set to ‘Disabled.’
- The ‘Status’ value should be ‘Not signing DKIM signatures for this domain.’
- The ‘Create DKIM keys’ option should not be there.
- The ‘Rotate DKIM keys’ box should be there, but it should be grayed out.
Move to the next steps if all is fine in the details flyout.
- Go to the Defender portal.
- Choose Email & collaboration > Policies & rules > Threat policies > Email authentication settings page.
- Click on the ‘DKIM’ tab, followed by selecting the custom domain to configure by clicking anywhere in the row except the check box next to the name.
- There will be a details flyout where you have to select the ‘Sign messages for this domain with DKIM signatures’ toggle that is currently set to Disabled. Also, note the ‘Last checked date.’
- An error box will appear containing the values you have to use in the two CNAME records you create at the domain registrar.
We are considering an example where the custom domain is ‘testing.com’ and the initial domain for Microsoft 365 is ‘testing.onmicrosoft.com.’ As per this example, you will see the following error message-
Microsoft.Exchange.ManagementTasks.ValidationException|CNAME record does not exist for this config. Please publish the following two CNAME records first. Domain Name: testing.com Host Name:selector1._domainkey Points to address or value: selector1-testing-com._domainkey.testing.onmicrosoft.com Host Name:selector2._domainkey Points to address or value:selector2-testing-com._domainkey.testing.onmicrosoft.com.
If you have already published the CNAME records, sync will take a few minutes to as many as 4 days based on your specific DNS. Return and retry this step later.
So, you need to create the following CNAME records for the testing.com domain.
Hostname: selector1._domainkey
Points to address or value: selector1-testing-com._domainkey.testing.onmicrosoft.com
Hostname: selector2._domainkey
Points to address or value: selector2-testing-com._domainkey.testing.onmicrosoft.com
Copy the information from the error dialog and click ‘OK.’
Leave the domain details flyout open.
- Open a new browser tab or window and go to your domain registrar’s platform. There, you have to create two CNAME records using the details from the last step.
- Wait for a few minutes; let Microsoft take its time to detect the newly created CNAME records.
- Return to the details flyout you left open in the 5th step. Select the ‘Sign messages for this domain with DKIM signatures’ toggle.
Just within a few seconds, a dialog box will open in which you have to click ‘OK’ to close it. Then there will be a details flyout where you have to check the following-
- The ‘Sign messages for this domain with DKIM signatures toggle’ is set to ‘Enabled.’
- The ‘Status’ value should be ‘Signing DKIM signatures for this domain.’
- The ‘Rotate DKIM keys’ box should be there without being grayed out.
- The ‘Last checked date’ should be more recent than what you noted in the fourth step.
Use the Defender portal to customize DKIM using the .onmicrosoft.com domain
Although the initial .onmicrosoft.com domain automatically signs all outgoing emails with DKIM, you can use the below-mentioned process to configure it as per your preferences–
- Produce a pair of DKIM keys and add them to the Microsoft 365 data centers.
- Check and ensure the properties of the .onmicrosoft.com domain correctly show in the details flyout of the domain on the DKIM tab of the ‘Email authentication’ settings.
Ensure the details flyout has the following:
- The ‘Sign messages for this domain with DKIM signatures’ toggle is not visible.
- The ‘Status’ value should be ‘No DKIM keys saved for this domain.’
- The ‘Create DKIM keys’ box should be available.
Move to the next steps if all is fine in the details flyout.
- Go to the Defender portal.
- Choose Email & collaboration > Policies & rules > Threat policies > Email authentication settings page.
- Click on the DKIM tab, followed by selecting the .onmicrosoft.com domain to configure by clicking anywhere in the row except the check box next to the name.
- A details flyout will open, select ‘Create DKIM keys.’
- When the DKIM key generation process is done, the ‘Publish CNAMEs‘ dialog will open. Select ‘Close.’
Here, you don’t have to copy the values as you can’t create the CNAME records for the .onmicrosoft domain.
- After you hit the ‘Close’ button, you will be back on the domain details flyout. Here, you turn on the ‘Sign messages for this domain with DKIM signatures’ toggle.
- Once done, click ‘Close.’
Rotating DKIM keys for a custom domain in the Defender portal
- Go to the Defender portal.
- Choose Email & collaboration > Policies & rules > Threat policies > Email authentication settings page.
- Click on the DKIM tab, then select the domain to configure by clicking anywhere in the row except the check box next to the name.
- A details flyout will open; select ‘Rotate DKIM keys.’
- Ensure the details flyout has the following values
- The ‘Status’ should be ‘Rotating keys for this domain and signing DKIM signatures.’
- The ‘Rotate DKIM keys’ box should be grayed out.
6. After four days (96 hours), the new DKIM key will start signing outbound messages for the custom domain. During this period, the current DKIM key remains in use. You’ll know the new DKIM key is active when the ‘Status’ changes from ‘Rotating keys for this domain and signing DKIM signatures’ to ‘Signing DKIM signatures for this domain.’
To verify the corresponding public key used to authenticate the DKIM signature (indicating the private key that signed the message), check the s= value in the DKIM-Signature header field (the DKIM selector; for example, s=selector1-testing-com).
Disabling DKIM keys for a custom domain in the Defender portal
- Go to the Defender portal.
- Choose Email & collaboration > Policies & rules > Threat policies > Email authentication settings page.
- Click on the DKIM tab, then select the domain to configure by clicking anywhere in the row except the check box next to the name.
- A details flyout will open; turn off the ‘Sign messages for this domain with DKIM signatures’ toggle.
Final words
Remember to pair DKIM with SPF and DMARC for optimum protection against email spoofing and phishing. If you need help with email security, authentication, and reporting, reach out to us.