With the rampaging virus and a restriction on movement, most staff have started to work from home. While this change has led to a successful fight against the virus, it has given IT Security teams a lot to work on. A widespread workforce and spread-out security protocols have led to systems and networks becoming increasingly vulnerable to cyber threats like spear-phishing, BEC, etc. Moreover, most enterprises moving to the cloud created an open field for both the victim and the perpetrator.
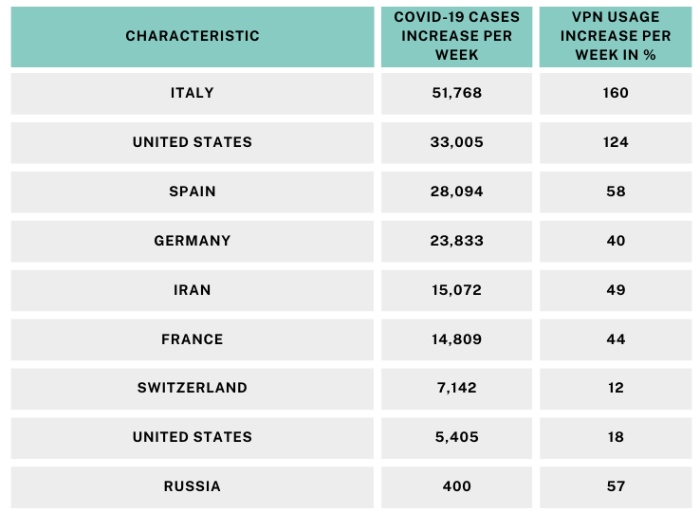
The staggering increase in VPN usage during the peak period of the pandemic is evident from the above table. While such a usage of a legacy technology should not be surprising, it is also an indicator of a domain that provides ample opportunity for exploitation.
What Makes VPNs Vulnerable?
VPN or Virtual Private Network is among the technologies that have been around for some time now. It is no longer a new-fangled concept that would require additional skill and knowledge, and most IT Security executives handle it for their respective organizations today. There are two reasons why VPNs are vulnerable to cyber threats that are slowly emerging from the horizon.
Outdated VPNs
One of the biggest banes in the world of technology is obsolescence. Outdated VPNs are a significant threat to the security of any organization. One reason is that VPNs were only used by travellers and those who wanted to access their office resources off-hours. It led to a small VPN traffic, which was minuscule compared to the overall traffic. IT Security teams often placed VPN servers way below in the pecking order. Hence, no one patched them on time. The slowness of the entire process also led to it being kept as the last item to be done. This is why choosing and maintaining a modern VPN service has become critical, as it is now a core component of everyday network security rather than an occasional remote-access tool.
The sudden rise in the usage of the VPN server led to complications. Suddenly, the security teams had to scramble for countless reasons, including email security, phishing protection, and ransomware protection. It all left too little time to focus on the VPN server. Malicious actors took advantage of this time to test their ware and penetrate the information systems. Moreover, these VPN servers being old and primarily outdated, the probability of them standing the test of modern-day cyber threats was minimal.
The solution to this is to close down the possibility of zero-day vulnerabilities by patching every VPN server and updating firewalls. At the same time, there would still be small gaps that malicious actors can exploit, but they can still avert more enormous catastrophes.
VPN Is An Ideal Portal To Intrude
VPNs have always been an ideal access point for cyber adversaries. They have been exploiting vulnerabilities and gaps to enter networks and cause havoc. There is a reason behind this too. VPNs have never been segmented. That is, it has always been open for both employees and vendors. Entry and access mechanisms have been lax, and intruders have always taken advantage of this vulnerability. Even fully patched VPNs would be unable to resolve this matter since entry and access are done at the enterprise level.
The sole solution to this issue is to monitor traffic and restrict entry and usage. Continuous monitoring reveals vital information like volume of information transfer, user login, etc. Behavioral analytics is critical to weed out the drawbacks and create a protective barrier by forming an entry mechanism. One of the early vulnerabilities that VPNs used to face was weak monitoring. It has now been eradicated with the increased usage of the VPN servers, and constant vigil has been institutionalized. Greater emphasis is being given to policing the VPN servers, and that has been paying dividends.
The Early Warning
The CISA (Cybersecurity and Infrastructure Security Agency) had pointed to an impending disaster after the SolarWinds VPN attack. It said in a statement that long-term actions had taken place and data had been compromised. In a joint advisory, malicious actors took advantage of the old threats that were still present. Both private and public enterprises were unable to revamp their systems thoroughly, and legacy software and hardware posed a challenge in the fight against cybercrime.
What Went Wrong With Organizations
Much has been said about the vulnerabilities. However, the primary reason for it has been the sheer slowness of the entire process.
Patching and upgrading VPNs is a time-consuming affair, which directly impacts the organization’s productivity.
It is one of the reasons why it has been delayed. These are mission-critical software, which, if lost, would be disastrous for the organization. Hence creating backups, including MX backups, was critical to the continuity of the business.
Also, routine vulnerability scans were a non-starter in many organizations, which aggravated the situation. In the same vein, it also needs to be said that with changing mechanisms, it was increasingly difficult for security teams to counter every attempt even with the best of efforts. Some solution to protect VPN networks was required similar to anti-phishing services to fight against phishing attacks.
Final Words
VPN vulnerabilities are a current concern since a more significant chunk of employees are accessing it remotely due to the pandemic. With this, email security has become a concern for many organizations. Due to less usage in the past, the VPN servers haven’t undergone major security patching and face a barrage of cyberattacks. Cyber adversaries have been able to locate vulnerabilities and exploit them, causing major disruptions. Organizations have to patch their VPN servers with the latest security updates and implement stricter entry and access mechanisms to overcome this challenge.
So when using a VPN it is important that you choose top quality and reliable brands as they offer better security and protect your data. NordVPN 3 year offer is currently available even though the prices may be on the higher side but the services offered are worth it.