The psychology of phishing: why smart people still fall for scams
You think you might know it all about the latest cyber scam trends, what to do when one strikes your organization, and how to evade them, so an attacker can never get to you.
We hate to break it to you, but these attackers are always a step ahead of you, and no one is ever really immune to their malicious tactics, especially when it comes to new-age phishing attacks.
These attacks are no longer about the same old obvious spelling mistakes or suspicious links; they are now based on human psychology. The threat actors now understand that technology isn’t the only weakest link anymore; people are. And they capitalize on that, so much so that even the most well-informed people fall prey to their strategies.
In this article, we will understand what makes these phishing attacks so grave and why even smart people still fall for them.
Why is phishing still a problem that we underestimate?
Phishing attacks have been around since the mid-1990s, and even after almost three decades, these attacks continue to be one of the most serious ones of them all. That’s not because the security landscape hasn’t evolved at all since then; in fact, it’s exactly the opposite.
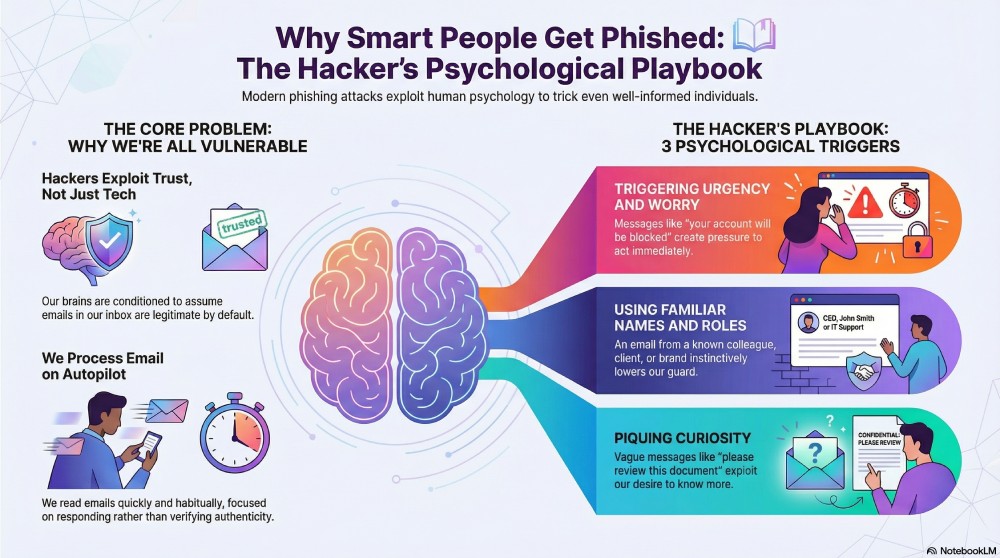
While systems have changed, the way people use email hasn’t. People still read emails quickly, trust familiar names, and respond as part of their daily work.
Most security improvements over the years have focused on systems, such as stronger filters, more robust authentication, and stricter access controls. These measures have helped mitigate certain risks, but they have not changed how people use these systems, communicate, or perceive email security. This is perhaps one of the most significant gaps that no tool or authentication protocol can ever fill.
Remember, email operates on trust, especially when it comes from a brand or an organization. When a message is delivered to the recipient’s inbox, they are conditioned to assume that it’s legitimate by default. It is this assumption that shapes how they read these emails—quickly, habitually, and with an intent to respond rather than to verify.
Phishing works because of it. Instead of looking like an obvious scam, these emails try to blend in with the rest of your incoming messages; they look like emails that you already deal with every day, like an approval request, a shared file, a payment follow-up, or a login alert. Since it feels familiar, your brain treats it as routine work, not something that needs extra checking.
That’s also why phishing is easy to underestimate. And the worst part is that it doesn’t feel like a major security lapse until the damage is already done and visible. By then, the problem is no longer the email itself, but the misplaced trust that underlies email systems and that attackers know how to exploit.
How do attackers manage to get into your head?
As you know, exploiting technical vulnerabilities is no longer the only way attackers deceive you and your clients. They know that these systems can be upgraded or changed, which is why they exploit a fundamental aspect to communication: trust.
Let’s understand how this plays out in practice.
Familiar names and recognized roles
When you see an email from a colleague or a client that you know well, you are instinctively more likely to trust it. You don’t read it the same as you would open a message from an unfamiliar sender. The name, role, or relationship, all of these act like a sign of legitimacy in your head.
Messages that trigger worry
Attackers know that the moment you see an email suggesting that something is wrong, like “your card has been blocked”, your attention shifts immediately. The message creates a sense of worry before you even have a chance to read it properly. At this point, you don’t pause to think that if the message is even legitimate, all you care about is what went wrong and how to deal with it.
This narrows your focus. So instead of verifying the message’s authenticity, you try to fix it as soon as possible. This emotional shift is often enough for the attacker to get the response they want.
Make everything feel urgent
After putting you in a difficult spot, these attackers add further pressure by making it seem like you have very little time to act. For instance, they might warn that your account will be blocked, a payment will fail, or access will be removed if you don’t respond immediately. Messages like these are designed to make you act in haste without verifying the email’s credibility.
Pique curiosity
Phishing emails are meant to pique your curiosity. They hint at something without explaining it fully, like a document you weren’t expecting or a message that says you need to “take a look.” When something feels vague like that, it’s hard to ignore. You end up opening the email just to see what it says. It might not feel risky in the moment, which is why it works.
Opening the message might seem like a normal thing to do, and not a serious mistake. Attackers rely on that moment of curiosity to get you to take the next step, where you unknowingly divulge your sensitive information or download malware into your system.
Why is awareness alone not enough to make you immune to phishing?
We understand that comprehensive knowledge of these attacks is important, but that alone isn’t enough. Phishing attacks are not something that people fall for because they didn’t know enough about them, mostly because they didn’t bother to think in that moment.
When an email arrives that looks normal and fits into what they’re already doing, they act on it without giving it much thought.
So, having more knowledge about these attacks won’t protect you, unless you really understand how and why phishing works on you. What’s important is being deliberate in how you respond to emails. Slow down when something feels urgent, take a second look at requests that seem familiar, and get into the habit of checking before acting.
Need help defending your organization and clients against phishing? Reach out to us.