Google Warns AI Hacking, First Contact Health Sanctioned, German Warning Messaging Phishing – Cybersecurity News [February 9, 2026]
This is the 4th edition of cyber news for the month of February. This bulletin includes the top cyber incidents that kept cybersecurity experts on their toes. While Google believes that artificial intelligence is adding speed and efficacy to threat campaigns, German intelligence issues a warning against state-sponsored phishing campaigns that might abuse messaging apps. Meanwhile, First Contact Health got sanctioned because of a phishing breach. Also, there has been a sudden spike in overall phishing attacks due to Valentine’s Day celebrations.
Google warns against AI-led swift and smooth hacking campaigns!
Google’s Threat Intelligence Group (GTIG) has stated that artificial intelligence is speeding up the existing threat campaigns. The tech giant believes that AI helps in hyper-personalization of the campaigns, and also makes it easy to evade the detection tools.
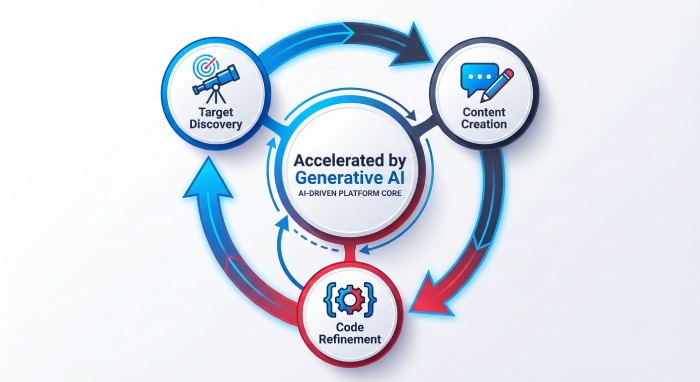
Threat attackers and hackers are misusing generative AI tools to carry out real-world cyber campaigns. They consider AI tools as something that boosts their overall operations and helps them scale the attacks smoothly. They are misusing AI tools across multiple stages of cyber campaigns, such as finding the targets, creating the phishing messages, and fixing the malicious codes, thereby “increasingly leveraging generative AI across multiple stages of the attack lifecycle.”
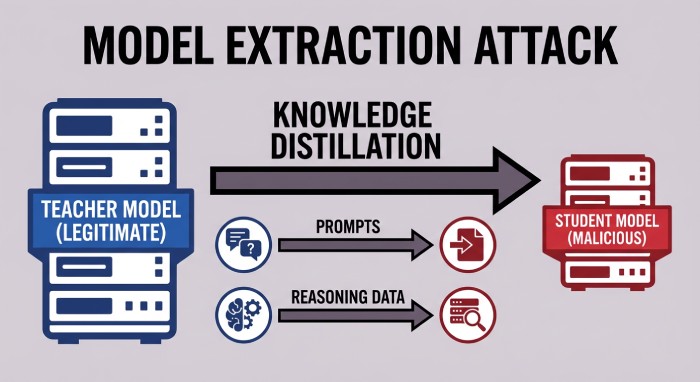
Google also warns against MEA attacks. This involves scammers abusing legitimate access to penetrate into the systems of a machine learning model and extract sensitive data that is used to train another new model. Cybercriminals use a technique called Knowledge Distillation (KD to carry out this intricate process. That’s exactly why MEA attacks are also known as distillation attacks.
Threat actors use prompts to instruct the “teacher” model to share the reasoning processes or data it would have used to train the “student” model. Experts have identified 100,000 such prompts. Some of the prompts instructed the teacher model to mimic Gemini’s reasoning ability across non-English languages.
With such detailed information, attackers are equipped and prepared now more than ever to come up with hyper-personalized and credible phishing campaigns.
First Contact Health sanctioned by the Office of the Data Protection Authority over a phishing mishap!
First Contact Health came to know about the cyber mishap back on 21st May 2024. They became aware of the breach when fraud attempts were made linked to the compromised email account of one of their employees.
First Contact Health informed the concerned authorities about the cyber incident to concerned authorities well within the stipulated timeline. But authorities decided to carry out a formal enquiry because of potential inadequacies in security measures before the cyberattack took place.
The enquiry revealed that First Contact Health had failed to deploy adequate safety measures. The gravity of the First Contact Health’s negligence deepens as its daily operations involve processing sensitive health information.
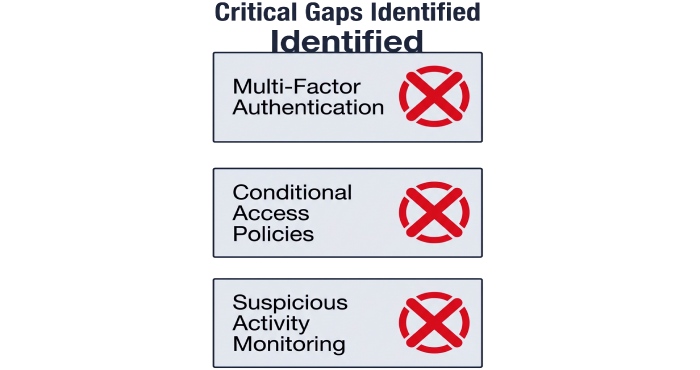
Apart from this, the probe discovered multiple other failings, such as the absence of a Multi Factor Authentication system, no traces of additional conditional access policies, and zero deployment of monitoring tools to track suspicious activities.
An enforcement order has been imposed that requires First Contact Health to bolster the overall safety systems. In case the organization fails to follow the instructions, the Data Protection Authority will take stringent action.
Commissioner Brent Homan stated that organizations responsible for managing sensitive data, such as health information, should implement robust authentication measures to prevent cyber incidents.
German intelligence issues a warning against messaging app-based phishing attacks!
A sophisticated phishing campaign is doing the rounds in Germany. It has gained the attention of the German intelligence team and targets high-profile individuals like military officers, politicians, and diplomats. Cybercrooks use messaging apps like Signal to target these victims.
Experts believe that these cyberattacks can be state-sponsored and that the threat actors are using social engineering techniques instead of deploying malware or abusing technical vulnerabilities in the messaging app.
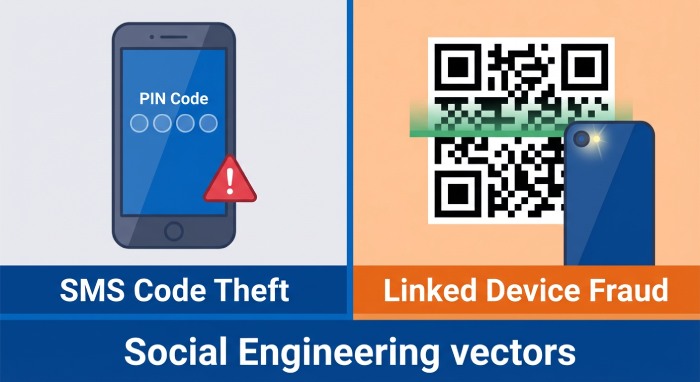
The threat actors pose as messaging app support team members or chatbots and trick victims to sharing sensitive data. The intelligence team has identified two main attack variants. The first one enables the threat actors to gain full account takeover by abusing Signal PINs or SMS verification codes. The second one involves abusing the linked-device option by persuading users to scan any QR code.
The concerned authorities have urged users to avoid interacting with any customer support systems of Signal and other similar apps for the time being.
Valentine’s Day leads to a sudden spike in phishing incidents!
Valentine’s Day celebration involves elements of surprise, curiosity, and urgency. Couples plan surprises for their partners and place online orders for gift items. Threat actors this season seem quite invested in Valentine’s Day celebrations.
Phishing attacks have increased all of a sudden since the beginning of February. Cyber incidents like brand impersonation are doing the rounds. Fraud attempts like sneaking up in email inboxes, DMs, and text messages have also become quite common.
From sending fake admirer messages to flower deliveries, cybercrooks are leaving no stone unturned to break into the systems of victims.
Last year, something similar happened, according to Check Point research. The experts discovered a live phishing campaign that involved threat actors sending malicious emails to victims. Each email claimed that the recipient had won a “Valentine’s basket.” It required the victims to click on malicious links, which further redirected the victims to credential harvesting websites.
Another form of cyberscam that is doing the rounds is false social media and dating profiles. The scammers are trained enough to win the trust of their victims. Once they gain their trust, the scammers create a situation of urgency and ask for monetary help from the victims. Such scams often involve tactics like deepfakes and vishing to trick naive victims.
Authorities have urged couples to stay vigilant and avoid going for offers that sound too good to be true. It is better to place orders from only reputed brands, and also, trusting your instincts can actually help you prevent these threat actors from ruining your special day.