Trust Wallet Hack, Browser Extension Espionage, Unleash Protocol Loss – Cybersecurity News [December 29, 2025]
This week’s cybersecurity news highlights how trust-based digital systems continue to be exploited across crypto platforms, browser ecosystems, and online marketplaces. Trust Wallet disclosed a major supply-chain attack that led to millions in stolen crypto, while researchers uncovered a long-running browser extension campaign tied to corporate espionage.
A separate smart contract breach drained funds from Unleash Protocol, and AI-generated images are now being used to scale refund fraud across Chinese e-commerce platforms. Here’s what happened and why it matters.
1. Trust Wallet Chrome Extension Hack Leads to $8.5 Million Crypto Theft
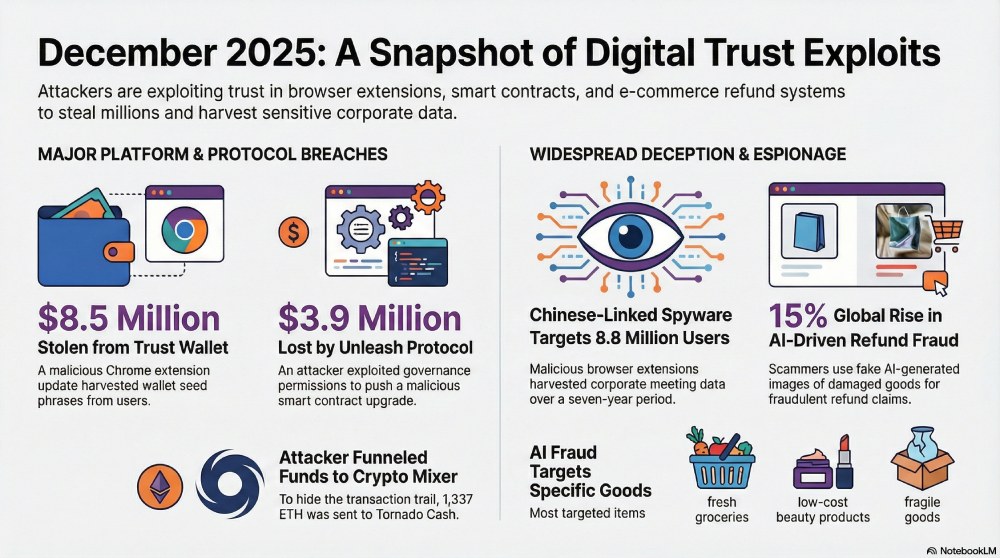
Trust Wallet has confirmed that a compromised Google Chrome browser extension was used to steal approximately $8.5 million worth of cryptocurrency from users, following a supply-chain attack traced back to November last year. The incident affected the Trust Wallet Chrome extension after attackers gained unauthorized access to its release pipeline.
According to the company, the breach occurred after developer GitHub secrets were exposed, giving attackers access to the extension’s source code and its Chrome Web Store (CWS) API key. With full CWS API access, the threat actor was able to upload malicious builds directly to the Chrome extension marketplace, bypassing Trust Wallet’s standard internal approval and review process.
The attackers pushed a tampered version of the extension (v2.68) on December 24, 2025, embedding a backdoor designed to harvest wallet mnemonic seed phrases. The malware exfiltrated the data to attacker-controlled infrastructure hosted on a lookalike domain, metrics-trustwallet[.]com. Researchers found that the malicious code activated whenever the wallet was unlocked and collected seed phrases from all wallets configured in a user’s account, regardless of whether biometric or password authentication was used.
Security firm Koi reported that the stolen data was disguised as routine telemetry, making the activity difficult to detect during casual code review. Analysis also showed the attack was premeditated, with infrastructure staged weeks before the malicious update was deployed. The campaign ultimately impacted 2,520 wallet addresses.
Trust Wallet has since urged its roughly one million Chrome extension users to upgrade to version 2.69, which removes the malicious code. The company has launched a reimbursement claims process for affected users and says it has added additional monitoring controls around its software release processes.
2. Chinese-Linked Malicious Browser Extensions Tied to Corporate Espionage Campaign
Security researchers have uncovered a large-scale malicious browser extension campaign linked to a Chinese threat actor that has quietly harvested corporate meeting data from millions of users across major browsers. The activity, tracked by Koi Security under the name DarkSpectre, has affected an estimated 2.2 million users of Google Chrome, Microsoft Edge, and Mozilla Firefox.
DarkSpectre has now been linked to two earlier extension-based campaigns, ShadyPanda and GhostPoster, bringing the total number of impacted users across all three operations to more than 8.8 million over a seven-year period. The campaigns relied on seemingly legitimate browser extensions that were later weaponized to steal data, manipulate search results, hijack affiliate traffic, and conduct advertising fraud.
The most recent DarkSpectre operation, also referred to as the Zoom Stealer campaign, involved at least 18 extensions posing as tools for recording or managing online meetings. Once installed, the extensions harvested sensitive meeting data in real time, including meeting links, embedded passwords, IDs, schedules, participant details, and webinar metadata from platforms such as Zoom, Google Meet, Microsoft Teams, Cisco WebEx, and GoTo Webinar.
Indicators linking the campaigns to China include command-and-control servers hosted on Alibaba Cloud, Chinese-language artifacts in the code, and infrastructure registrations tied to Chinese provinces.
3. Unleash Protocol Loses $3.9 Million After Unauthorized Smart Contract Upgrade
Decentralized intellectual property platform Unleash Protocol has confirmed a security breach that led to the theft of about $3.9 million in cryptocurrency after an unauthorized change was made to its smart contracts. The incident was disclosed on January 1, with blockchain security firm PeckShieldAlert separately estimating the total losses.
Unleash said the attacker was able to gain enough signing permissions within its multisig governance system to act as an administrator. Using this access, the attacker pushed an unapproved contract upgrade that enabled withdrawals that were never authorized by the Unleash team and fell outside normal governance procedures.
Unleash Protocol is designed to turn intellectual property into tokenized blockchain assets that can be used in decentralized finance applications. By exploiting the unauthorized upgrade, the attacker unlocked withdrawal features and drained several assets from the platform, including USDC, wrapped IP, stacked IP, voting-escrowed IP, and wrapped Ether.
According to PeckShieldAlert, the stolen funds were then moved through third-party bridging services and sent to external wallets to make tracking more difficult. The attacker later deposited around 1,337 ETH into Tornado Cash, a crypto mixing service often used to hide transaction trails.
Following the incident, Unleash Protocol has paused all platform activity and started a full investigation with external security firms. Users have been advised not to interact with Unleash smart contracts until further updates are shared through official channels.
4. AI-Generated Images Fuel Refund Scams Across Chinese E-Commerce Platforms
Online sellers in China are dealing with a rising number of refund scams in which fraudsters use AI-generated images and videos to fake damaged products. The issue is spreading across major e-commerce and social shopping platforms, many of which rely on customer-submitted photos instead of physical returns when approving refunds.
Merchants on platforms like RedNote and Douyin have shared several examples of suspicious claims. These include photos of bed sheets that appear unrealistically shredded, ceramic cups that look torn like paper, and shipping labels with distorted or unreadable text. Sellers say certain product categories are being targeted more often, especially fresh groceries, low-cost beauty items, and fragile products, since refunds in these cases are usually issued without requiring a return.
One case that gained widespread attention involved a live crab seller who received photos and videos claiming that most of the crabs arrived dead. The scam unraveled after the seller noticed clear inconsistencies, including incorrect crab anatomy. Police later confirmed the images were fabricated and briefly detained the buyer, making it one of the first known cases in China where AI-based refund fraud led to enforcement action.
This trend isn’t limited to China. Fraud detection company Forter reports that the use of AI-altered images in refund claims has increased by more than 15 percent globally this year. Researchers warn that easy access to image-generation tools is lowering the barrier for large-scale refund fraud, pushing online platforms to rethink how trust-based refund systems work.