Last week was replete with unfortunate phishing mishaps. Here are the top cyber incidents that we have covered for you to keep you updated. While Amazon, the e-commerce giant, is being targeted by phishing actors, left, right, and center, LinkedIn is also becoming a popular playground for cybercrooks. The crypto community is already in shock because of the Ledger customer data breach incident. Meanwhile, a highly sophisticated campaign is targeting the user credentials by impersonating Google Support.
Amazon users around the globe are prone to threat attacks!
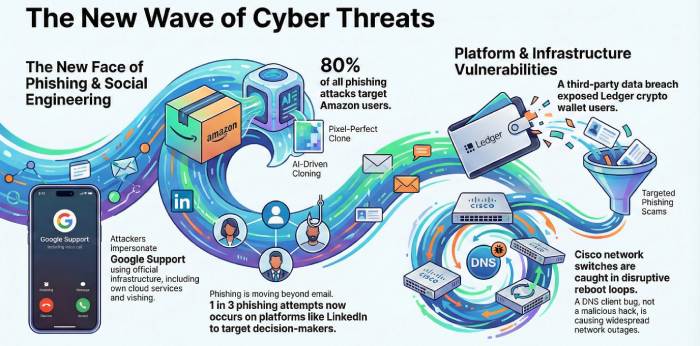
Threat attacks on Amazon have surged since Christmas 2025. Even the New Year could bring no relief. According to Darktrace, Amazon accounts for almost 80% of phishing attacks. Amazon users around the world are receiving daily piles of emails asking them to update or verify their Amazon account details. The latest campaign is designed to target Apple users specifically.
It says– “following a New Year system update, iCloud has started routine security verification to protect accounts from unusual sign-ins, unfamiliar devices, and outdated login details.” The same message instructs the Apple user to click on the “Update Account” button. When the victim clicks on the legitimate-looking, yellowish Update Account Information button, they get redirected to a malicious sign-in page. This page has been designed to extract security credentials.
Cybersecurity experts have urged Amazon users to avoid updating their accounts at any cost. Also, it is advised to review the user guidance Amazon provides to help users avoid such phishing scams.
Experts state that AI has made it easy for threat actors to create “pixel-perfect” clones of renowned brands, which they use to target unsuspecting users. They have urged users to avoid signing in to any account via links in SMS or email. Using the official website or the app is a smart and well-informed move in such situations.
LinkedIn is increasingly becoming a top pick among threat actors!
Phishing tactics have evolved tremendously in the past couple of years. The latest trends show that phishing actors are now choosing social media apps like LinkedIn to fulfil malicious intentions. In fact, 1 out of every 3 phishing attempts takes place outside email inboxes.
LinkedIn is gradually becoming a popular choice among phishing actors because the platform provides convenient, straightforward access to top decision-makers. It is equally easy to get in touch with the employees of any specific company that the cybercrooks may be targeting. Those associated with platforms like Google Workspace and Microsoft Entra are being targeted specifically. The idea is to zero in on a couple of companies and enterprises where the response action, logging, and visibility systems are evidently weak.
LinkedIn phishing is a considerably safe action plan for threat actors as the platform helps them bypass conventional security tools conveniently. Besides, LinkedIn phishing is cheaper and scalable as compared to other forms of phishing. Also, because of the inherent nature of the platform, any unsolicited message in your DMs does not seem suspicious.
Cybersecurity experts have urged LinkedIn users to treat every DM, message, and connection request as vigilantly as they would with regular emails. Enabling Multi-Factor Authentication is also advisable to minimize the effect of stolen passwords.
Ledger customer data breach- how to stay safe and secure as a customer
Ledger is a well-known brand among crypto enthusiasts. This Monday, the hardware wallet manufacturer confirmed that during a recent data breach incident, customer data was compromised. Ledger has claimed that the cyber mishap took place because of Global-e, its third-party e-commerce partner.
Because of the cyber incident, personal data like contact details and names of users have been compromised. However, Ledger has claimed that phishing actors could not access payment details, private keys, or wallet funds.
Users have already started witnessing a sudden spike in scam and phishing attempts. The threat actors are trying to impersonate Global-e support or Ledger to trick users into sharing sensitive data.
Experts believe that whether or not your Ledger data has been leaked, you can still fall prey to a phishing attempt if you happen to own a Ledger hardware wallet.
Cybercrooks posing as the Google Support team to gain access to user credentials
A whole new, high-end phishing campaign has been doing the rounds. The campaign involves threat actors posing as Google Support team members. The cybercrooks have strategically blended spoofed domains, vishing, and Google’s own infrastructure to gain credibility and higher success rates.
First, they connect over calls and use vishing and mimic Google Support executives. Next, they share a malicious link in follow-up emails to further gain the trust of the victim. The biggest concern is that cyberattackers are exploiting Google Cloud Application Integration services rather than using a false domain. When a victim clicks a malicious link, they are redirected to pages that can display fake CAPTCHA verification screens.
Cisco switch reboot issue
Cisco networking switches from several product lines, including CBS250, CBS350, SG350/550X, and Catalyst 1200/1300, have been caught in continuous reboot loops due to a DNS client bug, disrupting networks globally. The problem began around the same time across multiple systems, with affected devices logging fatal DNS lookup errors, such as failing to resolve or time servers, and then rebooting every few minutes.
Administrators found temporary workarounds by disabling DNS resolution, turning off time sync (SNTP), or blocking outbound internet access from switch management interfaces, which helped stabilize devices. Cisco acknowledged the issue privately to some customers, noting it affects small-business-series switches, and said changes in upstream CDN behavior were recently rolled back, reducing the immediate impact.