GitHub Backdoor Threat, Cartier Data Breach, Fake RubyGems Steal – Cybersecurity News [June 02, 2025]
From hidden backdoors on GitHub to fake Fastlane plugins hijacking social media bots, this week’s cyber updates spotlight how trust in familiar tools is being silently exploited. Major brands like The North Face and Cartier are also dealing with breaches, and U.S. agencies face urgent patch deadlines due to active vulnerabilities. Let’s take a closer look!
Backdoored GitHub Repos Leveraged by Threat Actors to Target the Mob
A hacker is running a large-scale campaign targeting gamers, developers, and even fellow hackers by planting backdoors in code shared on GitHub.
The attack relies on disguising malicious scripts, game cheats, and exploit tools as legitimate open-source software. The activity came to light after Sophos researchers were approached about the Sakura RAT–an openly available remote access trojan on GitHub. Though the tool itself looked nonfunctional, the team discovered a hidden PreBuildEvent in its Visual Studio project that silently pulled malware when someone tried to compile it. The publisher behind it, going by “ischhfd83,” was tied to at least 141 repositories, 133 of which were linked to malware.
These repositories hosted everything from Python scripts with obfuscated payloads and Unicode-tricked .scr files to JavaScript and Electron-based files with encoded malware. Commits to these projects are automated to simulate active development, with one project racking up nearly 60,000 commits since March 2025. The traffic comes from YouTube, Discord, and cybercrime forums, drawing in unsuspecting users.
Once downloaded, the victims were hit with multiple stages of infection, ultimately receiving trojans like Remcos or Lumma Stealer. Many of the repositories are still live, so you should be cautious. Always inspect code and check for hidden build events before compiling anything from GitHub.
Cartier: A Victim of Data Breach Following Cyberattacks on Luxury Brands
This week, Cartier notified its customers of a data breach after unauthorized access to its systems was detected, which led to the exposure of personal client information.
The luxury brand has confirmed the incident and addressed the scope of the compromised information. Threat actors were able to access its systems temporarily, making away with limited customer data. Said data includes names, email addresses, and their home countries. The brand emphasized that no sensitive financial info, such as passwords, banking details, or credit card numbers, was accessed during the breach. They highlighted they were able to promptly contain the incident have cautioned customers that while the exposed data may seem minimal, it could be used for phishing or other targeted scams. Cartier has involved law enforcement and is collaborating with a third-party cybersecurity firm to investigate the breach as part of its remediation efforts.
Customers are advised to stay cautious and report any suspicious messages. The organization has not disclosed the full scope of the incident, and investigations remain ongoing.
To further protect customers from phishing attempts following such breaches, organizations should implement SPF, DKIM, and DMARC to ensure email authentication and enhance email security.
Fake RubyGems Masquerading as Fastlane Steal Telegram API Credentials
Two malicious RubyGems packages disguised as Fastlane plugins have been caught intercepting Telegram bot communications, putting developers’ sensitive data at risk.
These lookalike plugins have managed to stay live and attract hundreds of downloads, raising concerns about supply chain security in open-source ecosystems. The incident revolves around two gems, fastlane-plugin-telegram-proxy and fastlane-plugin-proxy_teleram, which imitate the legitimate fastlane-plugin-telegram, a tool used by mobile developers to receive CI/CD updates via Telegram.
While they appear identical in function and presentation, the difference lies in a hidden redirection: instead of routing messages through Telegram’s official API endpoint, these packages silently redirect all traffic to an attacker-controlled proxy—rough-breeze-0c37[.]buidanhnam95[.]workers[.]dev. This proxy captures Telegram chat IDs, messages, uploaded files, proxy login details, and even bot tokens—any of which could allow the attacker to hijack bots or spy on developer activity. Despite claiming not to log this data, the proxy’s behavior can’t be verified.
Researchers at Socket, who uncovered the attack, emphasize that Cloudflare Workers used in the proxy are opaque and can be abused without visibility. Developers should uninstall them immediately, revoke any affected bot tokens, and rebuild impacted binaries. Blocking wildcard access to *.workers[.]dev is also recommended.
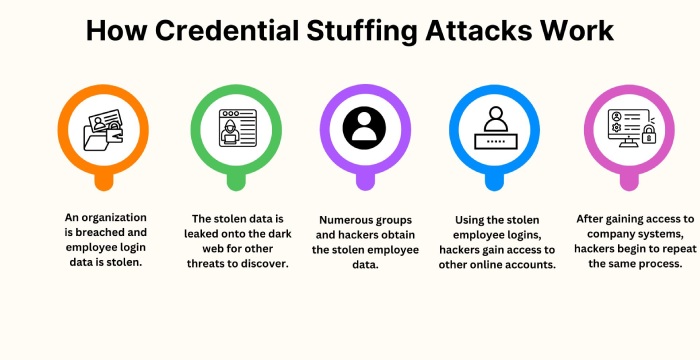
The North Face Alerts Users to April Credential Stuffing Incident
Cartier isn’t the only brand to suffer an attack this week. The North Face also alerted customers to a data breach caused by credential stuffing attacks on its website in April.
The brand is known for its outdoor gear and apparel, with online sales forming a major part of its business. On April 23, 2025, suspicious activity was detected on thenorthface.com, prompting an immediate investigation. It was later confirmed that attackers had launched a credential stuffing attack, an automated method where stolen username-password combinations from past breaches were used to break into accounts. Since many users reuse passwords across sites, the method often succeeds unless Multi-Factor Authentication (MFA) is enabled. The attackers were able to access customer data, including full names, shipping addresses, email addresses, phone numbers, dates of birth, and purchase history.
However, no payment details were affected as they are handled externally. They are still notifying affected users. Customers are advised to update their passwords and enable MFA to better secure their accounts.
CISA Flags Actively Exploited Vulnerability in ConnectWise ScreenConnect
Federal agencies in the U.S. are being warned about active cyberattacks that exploit a vulnerability in ConnectWise ScreenConnect, recently patched in late April. The flaw, if abused, allows attackers to run malicious code on targeted servers.
Alongside this, several other serious vulnerabilities in ASUS routers and Craft CMS are also being actively targeted. The ScreenConnect issue tracked as CVE-2025-3935, involves improper authentication and can be used for a ViewState code injection attack. Since ASP.NET Web Forms use ViewState to maintain page state with base64-encoded data protected by machine keys, a threat actor who gains access to those keys could execute code remotely on the server.
The vulnerability gained attention following a breach at ConnectWise suspected to involve state-sponsored attackers. ConnectWise has not detailed the attack or confirmed a link to this flaw, but many users believe it’s related. The vendor acknowledged that only a small number of ScreenConnect users were impacted. On the other hand, CISA also flagged four exploited bugs–two critical ones in ASUS routers (CVE-2021-32030, CVE-2023-39780) and two in Craft CMS (CVE-2024-56145, CVE-2025-35939).
They have added all five vulnerabilities to their Known Exploited list and have asked agencies to apply fixes or stop using affected systems by June 23. Users should update their devices and CMS platforms promptly to reduce exposure.