Spotify Copyright Scrape, n8n Code Execution, MacSync Stealer Installer – Cybersecurity News [December 22, 2025]
Cyber incidents this week ranged from large-scale scraping to high-impact software and supply chain risks. An activist group claims to have scraped tens of millions of tracks from a major streaming platform, raising fresh copyright concerns. Separately, a critical n8n flaw could allow code execution on exposed instances. Other reports covered a notarized macOS stealer campaign, a GitLab breach impacting a car maker’s customers, and malicious Chrome extensions abusing proxy access to steal credentials.
Anna’s Archive Claims Massive Spotify Scrape as Copyright Row Intensifies
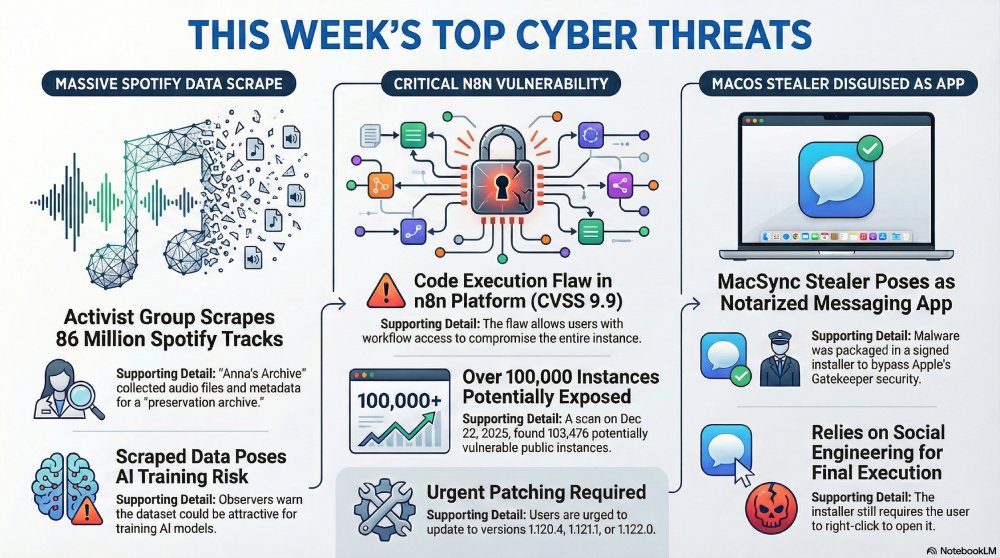
An activist group, Anna’s Archive, claims it has scraped a large volume of music and metadata from Spotify and is preparing to publish it online. The group says it collected 86 million audio files and 256 million rows of metadata such as artist and album names, while Spotify confirmed the material does not represent its full catalogue. Spotify said it detected unlawful scraping activity, disabled the accounts involved, and found that a third party had scraped public metadata and used illicit methods to bypass DRM to access some audio files. Spotify added that it does not believe the scraped music has been released yet, while Anna’s Archive describes the effort as a “preservation archive” and says it plans to share files via torrents.
Strong SPF, DKIM, and DMARC enforcement helps prevent domain abuse, spoofing, and data theft seen in modern cyber incidents.
Observers warn that the dataset could be attractive to AI developers looking for modern training material. A copyright campaigner said pirated content is frequently used to train models and argued that regulators should require AI firms to disclose their training data. The group’s site references other piracy-linked archives that have been cited in litigation involving AI training. Spotify said it has added new safeguards and is monitoring for suspicious behavior as the broader debate over AI and copyright continues, with a Western government expected to publish policy proposals by 18 March 2026.
Critical n8n Vulnerability Enables Code Execution Risk
A critical security flaw has been found in the n8n workflow automation platform that could allow arbitrary code execution in certain conditions. Tracked as CVE-2025-68613 and rated CVSS 9.9, the issue was reported by security researcher Fatih Çelik. The n8n package is widely used, with around 57,000 weekly downloads on npm. The maintainers said the risk arises when expressions entered by authenticated users during workflow setup are evaluated in a context that is not adequately isolated from the underlying runtime. In practical terms, a user with workflow configuration access could potentially abuse this behavior to execute code with the privileges of the n8n process, leading to full compromise of the instance, unauthorized data access, workflow tampering, and system-level actions.
The vulnerability affects versions 0.211.0 and later up to, but not including, 1.120.4. Fixes are available in 1.120.4, 1.121.1, and 1.122.0. Internet exposure may be significant: It was reported that 103,476 potentially vulnerable instances as of 22 December 2025, with large concentrations across several major regions. Users are urged to patch quickly. Where updates cannot be applied immediately, organizations should restrict workflow creation and editing to trusted users and run n8n in a hardened setup with limited operating system privileges and controlled network access.
MacSync Stealer Masquerades as Signed Messaging Installer
Cybersecurity researchers have revealed a new variant of the MacSync macOS information stealer that is being distributed through a digitally signed and notarized Swift application disguised as a messaging app installer. The malware is packaged inside a disk image named “zk-call-messenger-installer-3.9.2-lts.dmg” hosted on a lookalike download site, allowing it to run without being automatically blocked by Apple security controls such as Gatekeeper. Even so, the installer still displays guidance telling users to right-click and open the app, a familiar social engineering trick. Apple has since revoked the associated code signing certificate.
Once executed, the Swift-based dropper runs several checks before pulling down the next stage via a helper component. It confirms internet connectivity, enforces an execution interval of around 3600 seconds to limit repeated runs, removes quarantine attributes, and validates files before execution. The download routine has also been adjusted, including changes to curl flags, options such as —noproxy, and dynamically built request elements to make retrieval more dependable and less obvious. The DMG is also inflated to about 25.5 MB by bundling unrelated PDF files. The decoded Base64 payload delivers MacSync, described as a rebrand of Mac.c, using a Go-based agent for data theft and remote command and control.
Nissan Confirms Data Breach Originating from GitLab Repositories
Nissan has confirmed it was impacted by unauthorized access to a self-managed GitLab instance used by the Red Hat Consulting team. The late September intrusion affected repositories holding example code, internal communications, and project documents linked to customer management system development. A group calling itself Crimson Collective later attempted to extort Red Hat, claiming it had taken a large cache of compressed data from thousands of private repositories and suggesting the stolen material could be used to access customer environments.
Nissan says the stolen data included personal information linked to about 21,000 customers of Nissan Fukuoka Sales, previously known as Fukuoka Nissan Motor. The exposed details reportedly include names, addresses, phone numbers, partial email addresses, and information used for sales activities. Nissan stated that no credit card data was involved and that no additional customer information was stored in the compromised repository. The company was notified by Red Hat on 3 October, around a week after the incident, and says it has reported the matter to the relevant authorities and begun notifying affected individuals. Nissan also noted it could not confirm claims that the stolen information may have been used multiple times by the attackers.
Chrome Extensions Pose as VPN While Intercepting User Sessions
Security researchers have identified two Google Chrome extensions called Phantom Shuttle, published by the same developer, that appear to operate as a paid “VPN” while secretly intercepting traffic and stealing credentials. Marketed as a multi-location network speed test for developers and business users, the add-ons charge a subscription and grant “VIP” access after payment. At that point, they automatically enable a proxy mode that routes traffic for more than 170 selected domains through infrastructure controlled by the operator. The extensions still run real latency tests and show connection status, helping maintain the impression that the service is legitimate.
The malicious activity is embedded in bundled JavaScript. It hooks into Chrome’s request flow and responds to HTTP authentication challenges by silently injecting hard-coded proxy credentials, so the user is not shown a login prompt. Once the proxy is connected, the add-on loads a PAC script that lets it switch the proxy off, send all browsing through it, or only route a set list of high-value sites such as developer, cloud, and enterprise services. Researchers also saw the extension call back to an external server at regular intervals, with reports that VIP login details may be sent in plaintext. Users should uninstall the extensions, and organisations should restrict approved add-ons and pay close attention to proxy-related permissions.