Discover the latest cybersecurity news from around the world with our latest cybersecurity bulletin sharing supply chain attacks, security updates from Apple, threat actors exploiting crypto bugs, hacking competitions, the arrest of an Australian BEC threat actor group, and ChatGPT’s data exposure. Let’s get into it.
Supply Chain Attack Compromises 3CX Desktop Application
Customers of the VoIP IPBX software development enterprise 3CX are being targeted as part of an ongoing supply chain attack with the threat actors employing digitally signed, trojanized versions of the enterprise’s software.
Sophos and CrowdStrike’s security researchers alerted individuals that the threat actors target both Windows and macOS users of 3CX’s softphone application. The supply chain attack is being dubbed “Smooth Operator” by SentinelOne and is not limited to individuals. Global organizations like American Express, Coca-Cola, McDonald’s, BMW, Honda, Air France, Toyota, Mercedes-Benz, IKEA, and the UK’s National Health Service use the software.
All these organizations may be potential victims of the attack as well. Researchers suspect Smooth Operator to be the work of the North Korean state-backed hacker group Labyrinth Collima. Smooth Operator malware is a highly sophisticated tool that steals information by downloading encoded payloads to computer systems and includes many advanced capabilities such as harvesting device information, exfiltrating data, and stealing stored credentials from multiple browsers.
The Smooth Operator malware connects to threat actor-controlled domains such as akamaicontainer.com, msedgepackageinfo.com, and azureonlinestorage.com. You need to stay vigilant if you are a user of 3CX’s desktop client software or connected to any organizations that do.
SafeMoon Liquidity Pool Drained $8.9 Million Due to ‘Burn’ Bug Exploitation
Another significant loss in the crypto space took place, this time on the SafeMoon token liquidity pool, due to a threat actor exploiting a “burn” smart contact function to make away with $8.9 million.
The threat actor artificially inflated the token’s prices and sold them to innocent individuals at elevated prices to generate profit. The threat actor sold SafeMoon at the manipulated price leading to the large-scale drain from SafeMoon’s WBNB liquidity pool.
John Karony, SafeMoon’s CEO (Chief Executive Office), confirmed the cybersecurity incident, highlighting that the exploit has been successfully located and that SafeMoon has hired a chain forensics consultant to investigate the nature and extent of the attack. Karony went on to clarify that the tokens of its users are safe. No other tools, upgrades, or releases on the DEX (Decentralized Exchange) were affected.
PeckShield’s researchers shed light on the attack, sharing that the “burn token” smart contract function was set to public with any restrictions which allowed the threat actor to exploit said function and cause this large-scale crypto attack.
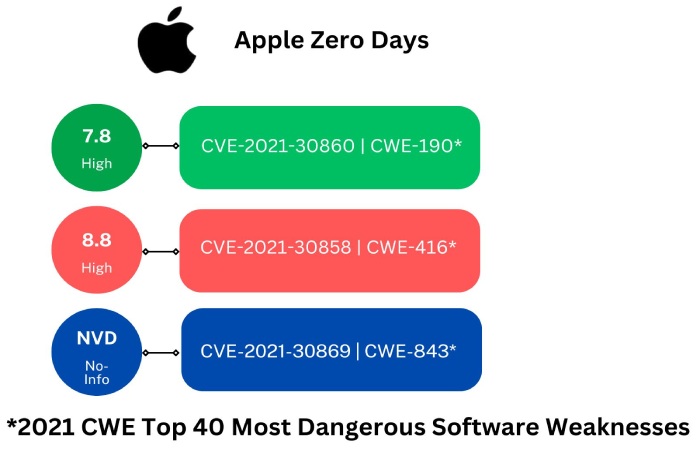
Apple Addresses Webkit Zero-Day on Older iPhones With New Fix
Apple is one of the most recognizable and prominent tech giants in the world, known for the security of its devices. However, the organization recently discovered a significant vulnerability, releasing a new patch.
Apple launched a security update to patch the CVE-2023-23529, a WebKit-type confusion vulnerability fixed for the latest iPhones and iPads, on 13 February 2023. Any threat actor exploiting the vulnerability could trigger OS (Operating System) to crash and gain code-executing capabilities on Apple devices. After gaining access, threat actors could also execute arbitrary codes, leading Apple users to malicious web pages. Apple received reports that the vulnerability was being actively exploited, which led to the fix.
The security update to take care of the vulnerability was released for older devices that received improved checks. Apple has not released any information regarding threat actors exploiting the vulnerability, which is the organization’s standard procedure. Apple restricts access to technical details so individuals can secure their devices, so any threat actors trying to exploit said vulnerability on older devices cannot. It is recommended that iOS users update their devices to the latest software that includes the security patch.
Pwn2own Vancouver Sees Hackers Earn $1,035,000 for Exploiting 27 Zero-Days
The Pwn2own hacking competition 2023 took place in Vancouver from 22 March to 24 March 2023, where hackers showcased their talents by targeting devices in multiple categories.
The competition had multiple categories, such as Virtualization, Servers, Automotive, EoP (Escalation of Privileges), and more, with a prize pool of $1,000,000 and a Tesla Model 3. The hackers exploited 27 zero-day vulnerabilities and multiple bug collisions in patched systems like Windows 11, Microsoft Teams, Microsoft SharePoint, macOS, Ubuntu Desktop, VMware Workstation, Oracle VirtualBox, and the Tesla Model 3.
The Pwn2own competition was dominated by Team Synacktiv, who won 53 Master of Pwn points, winning nearly $530,000 from the competition and taking home the Tesla Model 3 during the three days when the contest lasted.
After the zero-day vulnerabilities were exploited and reported, the vendors now have 90 days to release security fixes to said vulnerabilities before TrendMicro discloses them to the public as part of its Zero Day Initiative.
Australian Police Apprehend Four BEC Actors Responsible for $1.7 Million Theft
The AFP (Australian Federal Police) arrested four members of a threat actor syndicate laundering $1.7 million stolen from nearly 15 individuals between 2020 and now.
AFP had been investigating the threat actors since 2021, following a BEC (Business Email Compromise) attack on an Indonesian business that led to a loss of $100,000.
The threat actor syndicate comprises 4 young adults, two men, and two women, that were arrested from Brisbane, Adelaide, and Melbourne. The threat actors conducted large-scale BEC attacks targeting individuals that utilized the Facebook Marketplace, offering them fraudulent superannuation investments and Ponzi schemes.
The threat actors laundered the money using 180 bank accounts, some of which were opened using impersonated identities. The threat actors now face charges for multiple accounts, such as producing or processing false documents, money laundering, dealing in proceeds of crime, and a couple more. Two threat actors may receive a maximum penalty of 10 years, while the other faces up to 20 years.
AFP has highlighted the ongoing need to stay protected and urges organizations and individuals to exercise caution when dealing with online transactions. Educating yourself on the latest scans is also crucial to staying protected.
OpenAI Acknowledges Open-Source Bug as Cause of ChatGPT Payment Data Leak
OpenAI revealed that a bug in its Redis client open source code library was the cause of its outage on its AI (Artificial Intelligence) product, ChatGPT, on Monday (20 March 2023).
ChatGPT has taken the world by storm and is one of the most popular and widely used AI chatbot services; that allows individuals to generate content by asking the chatbot queries. Multiple individuals reported seeing random chat queries in their chat that were later found to be of other individuals using the ChatGPT platform when ransom email addresses started appearing on the subscription pages too.
OpenAI took its service offline to investigate the issue causing the ruckus and released a report highlighting the cause of the incident. The report shed light on the incident, sharing that a bug in its Redis client caused the exposure of 1.2% of ChatGPT Plus members, revealing their names, email addresses, and payment addresses. The expiration dates and the last four digits of customer credit card numbers were also exposed.
Since the number of people affected by the incident is low, OpenAI took action to keep exposure to a minimum and is contacting all affected users, apologizing for the incident.