Here is the latest edition of the weekly cybersecurity bulletin to update you about the most recent news associated with the digital security landscape.
Phone Tracking App LetMeSpy Claims Thousands of Users’ Privacy Breached After Being Compromised
LetMeSpy, a widespread phone monitoring app used for surveillance, has fallen victim to a recent attack. The app, known as stalkerware or spouseware, discreetly operates on Android phones, making it difficult to detect and remove. The application uploads text messages, call logs, and precise location data to its servers without the user’s knowledge. It made it easy for the threat actors to track the victims in real time.
The leaked data, analyzed by TechCrunch, contains call logs and text messages covering years since 2013. The compromised database includes records of at least 13,000 devices, although some have minimal or no associated data.
The LetMeSpy website’s functionality appeared broken for a while, and its activity counters showed zero usage. The malicious actor responsible for the breach remains unidentified, but they claimed to have deleted LetMeSpy’s databases stored on the server.
A copy of the compromised database has surfaced online and was shared with TechCrunch by the transparency collective DDoSecrets, with limited distribution to journalists and researchers due to personal information concerns.
This breach adds to a growing list of compromised spyware and phone monitoring apps, emphasizing the risks associated with such tools. Xnspy, KidsGuard, TheTruthSpy, and Support King have also experienced similar breaches, highlighting the need for increased awareness and security measures surrounding such applications.
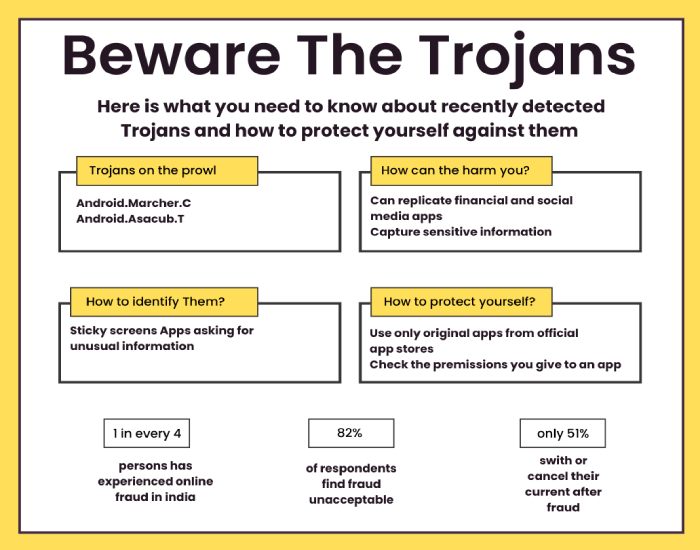
Anatsa Android Trojan Expands Its Reach, Targeting Banking Information in the US, the UK, and Other Countries
Mobile malware has targeted banking customers in the US, the U.K., Germany, Austria, and Switzerland since March of this year. Security researchers from ThreatFabric have discovered that the campaign distributes the Android banking trojan ‘Anatsa’ through the official Android app store, Google Play.
In November 2021, ThreatFabric identified a previous Anatsa campaign on Google Play, where the trojan was disguised as various apps, leading to 300,000 installations. After a six-month hiatus, the threat actors resumed their malicious activity by launching a new campaign, enticing victims to download Anatsa dropper apps from Google Play.
The dropper apps mimic legitimate office and productivity apps like PDF viewers and editor apps. When the malicious apps were reported and removed from the store, the attackers swiftly uploaded new dropper apps with different disguises.
Once installed, the dropper apps retrieve Anatsa payloads from GitHub, disguised as text recognizer add-ons for Adobe Illustrator. Anatsa then steals financial information through overlaying phishing pages and keylogging.
The trojan targets nearly 600 financial apps and utilizes the stolen information for on-device fraud, making it challenging for anti-fraud systems to detect. The stolen funds are converted into cryptocurrency and circulated through a network of money mules.
Users are advised to exercise caution, avoid dubious publishers, check reviews for suspicious behavior patterns, and refer to the ThreatFabric report for identifying and removing Anatsa-related apps.
Malvertising Emerges as a Sneaky Pathway for Infostealers and Ransomware Attacks
Malvertising is making a stir lately in the cybersecurity landscape. New research by Malwarebytes reveals a concerning rise in malvertising, with over 800 attacks reported in 2023, averaging almost 5 per day.
Infostealer malware varieties like IcedID, Aurora Stealer, and BATLOADER are commonly delivered through these malicious ads, compromising user credentials and paving the way for future ransomware attacks.
Ransomware gangs often purchase stolen credentials from initial access brokers, while some use malvertising directly to launch their attacks. Detecting malvertising is challenging as threat actors pose as legitimate brands, making it deceptive for users. Even Google experts struggle to identify malicious redirects.
Organizations should focus on advanced cybersecurity tools to combat malvertising rather than solely relying on brand imitation detection.
AEI Reports Threat Actors Focus on High-Profit Organizations
An AEI (American Enterprise Institute) study found that malicious actors prefer to target highly profitable organizations with abundant cash reserves and significant advertising expenditures.
The research analyzing cyberattacks from January 1999 to January 2022 suggests that successful organizations may be targeted for industrial espionage. The study also highlighted that many organizations fail to comply with the SEC (Securities and Exchange Commission) rules by not reporting cyberattacks.
However, the likelihood of reporting such incidents increases when subjected to external investor scrutiny and media coverage. The FBI said there is an increase in potential losses from cyberattacks and cyber fraud, reaching $10.2 billion last year compared to $6.9 billion in 2021.
FBI Deputy Director Paul Abbate warned of the escalating threats, with over 100 ransomware variants wreaking havoc on businesses. Furthermore, ransomware, malware, and distributed denial of service (DDoS) attacks were identified as the most damaging, impacting organization valuations by turning off IT systems and denying access to data and services.
The AEI researchers emphasized that the consequences of cybercrime extend beyond targeted establishments, adversely affecting peer organizations and the broader economy. Organizations linked to the primary victims experience average losses of 44% of the financial damage suffered by the immediate victim.
The researchers urged organizations to enhance their ransomware protection and cybersecurity measures to combat cyber threats effectively.