Welcome to this week’s edition of the ‘Weekly Cybersecurity Bulletin’ where we slice through the complexity of the digital security landscape to bring you the most pertinent news and updates making headlines around the world. From threat actors lodging SEC complaints to Phaas gangs getting arrested, this text has it all.
Ransomware Group Lodges SEC Complaint Regarding Victim’s Unrevealed Breach
The ALPHV/BlackCat ransomware crew has taken things up a notch by filing a complaint with the U.S. Securities and Exchange Commission (SEC). They’re pointing fingers at one of their supposed victims for not spilling the beans within the four-day window about a cyber hit.
Earlier today, these digital troublemakers put MeridianLink, a software enterprise, on blast in their data leak. They threatened to spill the beans on allegedly pilfered data unless a fat ransom is coughed up in the next 24 hours. MeridianLink is a big player in the digital solutions game, serving up tech goodies for banks, credit unions, and mortgage lenders.
So, the story goes like this: The ALPHV ransomware gang claims they busted into MeridianLink’s network on November 7, snagged some company secrets, and didn’t even bother encrypting anything. Just to prove they mean business, ALPHV posted a screenshot on their site showing the SEC complaint they filed.
In their own words, the hackers told the SEC that MeridianLink had a “big breach” and didn’t spill the beans, as required in Form 8-K, under Item 1.05. ALPHV also shared on their site the response they got from the SEC, just to show the complaint got through.
FBI and CISA Issue Alert on Rhysida Ransomware’s Opportunistic Attacks
The FBI and CISA issued a warning about the Rhysida ransomware gang pulling sneak attacks on various types of organizations. Rhysida made headlines in May 2023 when it hacked the Chilean Army, leaking their data online.
Recently, the US Department of Health and Human Services (HHS) jumped in, pointing fingers at Rhysida for hitting healthcare organizations. The joint cybersecurity advisory dropped some useful info for defenders – things like indicators of compromise, detection tips, and the tactics Rhysida uses.
They gathered all this from investigations up to September 2023. The agencies spilled the beans, saying Rhysida ransomware likes to hit ‘targets of opportunity’ in education, healthcare, manufacturing, IT, and government. These guys work like a ransomware-for-hire service, hitting up schools, tech companies, and government offices. If a ransom gets paid, they share the loot with their crew.
The Rhysida troublemakers don’t play fair and have been caught breaking into third-party services, like VPNs, by using stolen credentials to get in and hang out in victims’ networks. These types of cyber incidents underscore the requirement for robust ransomware protection across all kinds of institutions. The adoption of these phishing protection measures is essential to safeguard against potential threats.
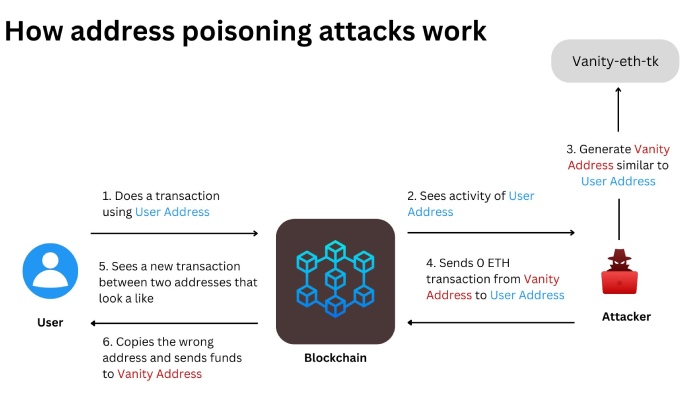
Ethereum Feature Exploit Leads to $60 Million Theft from Victims
Anti-scam experts at ‘Scam Sniffer’ uncovered a concerning trend involving the misuse of Ethereum’s ‘Create2’ function.
The researchers discovered that threat actors have been circumventing wallet security alerts, resulting in the misappropriation of approximately $60 million in cryptocurrency. They stole from 99,000 victims within a span of 6 months.
Ethereum’s ‘Create2’ function facilitates the creation of smart contracts on the blockchain. Unlike its predecessor, ‘Create,’ it enables the calculation of addresses before contract deployment. The report from Scam Sniffer shares how ‘Create2’ can be exploited to generate new contract addresses without a history of reported malicious transactions. This effectively evades wallet security alerts. So, whenever a victim approves a malicious transaction, the attacker deploys a contract at a pre-calculated address, resulting in an irreversible transfer of the victim’s assets. A highlighted case showed a victim losing $927,000 worth of GMX after unwittingly signing a transfer contract.
In August 2023, a Binance operator mistakenly sent $20 million to scammers employing the ‘address poisoning’ strategy. However, the error was detected in time, and the recipient’s address was frozen.
Law Enforcement Dismantles BulletProftLink, a Large-Scale Phishing Provider
The Royal Malaysian Police took down the notorious BulletProftLink phishing-as-a-service (PhaaS) platform.
PhaaS platforms are a huge threat as they provide low-level and wannabe cybercriminals with tools for phishing attacks. These platforms provide ready-to-use phishing kits, customizable templates, page hosting, credential harvesting, reverse proxying tools, and more.
BulletProftLink came into existence in 2015 and gained attention, amassing thousands of subscribers. Malaysian police apprehended 8 threat actors on 6 November 2023, including a self-taught threat actor believed to be the leader of the gang. They seized cryptocurrency wallets, servers, computers, jewelry, vehicles, and payment cards, amounting to about $213,000. The threat actors also had servers that the police will now use to identify users of the seized platform.
Intel471 reported that BulletProftLink had 8,138 active subscribers with access to 327 phishing page templates as of April 2023. This is a 403% increase since Microsoft’s 2021 report.