Healthcare Email Breaches, Wi-Fi Exploits Uncovered, Malware Exploits Avast – Cybersecurity News [November 25, 2024]
In this week’s cyber update, let’s examine the following case scenarios closely: a significant email data breach affecting multiple healthcare organizations, the discovery of a new Wi-Fi exploit used in targeted attacks, a malware campaign exploiting an outdated Avast driver, a high-profile extortion campaign targeting cloud storage platforms, and recent intrusion attempts on telecom infrastructure. These headlines are followed by matter-expert suggestions highlighting best practices one could follow to mitigate potential risks in the future.
Email Data Breaches Exposed in Multiple Healthcare Organizations
It has been reported that several employee accounts have been allegedly compromised. The affected entities include various healthcare industries, and let’s briefly dissect each of them below.
HealthFund Solutions
HealthFund Solutions (Florida) reported unauthorized access to compromising data for 5,198 individuals. The breach, which was detected in August 2024, was investigated, and it hasn’t yet resulted in the misuse of the exposed information. It’s become important for organizations to ensure robust email security and implement further authentication layers like MFA (multi-factor authentication).
Option Care Health
Option Care Health (Illinois) also experienced a breach that revealed patient data, which affected 2,897 patients’ data in July 2024. However, the company responded quite swiftly, giving credit monitoring and making sure of security hygiene in environments(sensitive) and the need for rapid response.
Liberty Endo
Unauthorized access was identified by Liberty Endo (New York) to an employee’s email account that ended up affecting 942 patients during July and August 2024. The affected individuals are being offered identity theft protection. Increased digitization of healthcare data has led Organizations to implement stringent email security practices to avoid such compromises.
United Seating and Numotion
Another company, Numotion, a provider of mobility solutions, has also reported access to several email accounts affecting 2,319 individuals. This occurred between August and September 2024. The company went forward to also offer complimentary identity theft protection services to the victims. Implementing multi-layered security controls and comprehensive monitoring is crucial for mitigating these risks.
For more details, you can visit the official page of The HIPAA Journal.
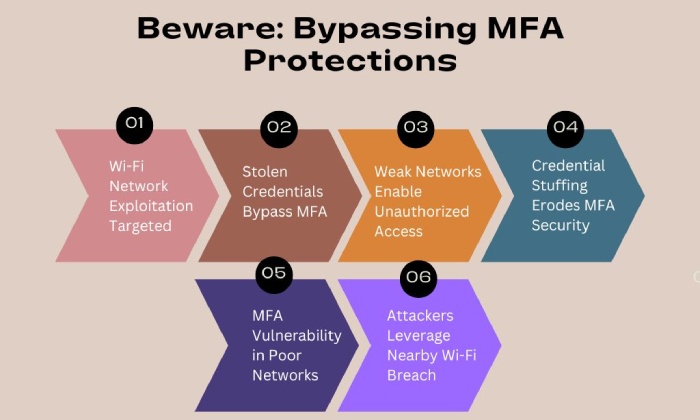
Researchers Discover New Wi-Fi Exploits in ‘Nearest Neighbor’ Attacks
Volexity researchers have uncovered a new method of attack that is called the “Nearest Neighbor Attack.” This technique allows the threat actors to exploit weak Wi-Fi networks to gain unauthorized access to the target systems. The attack involved tactics including credential stuffing and the bypass of Multi-Factor Authentication (MFA), which was allegedly used to infiltrate neighboring Wi-Fi networks, after which the attackers stole credentials for further exploitation. The hackers exploited weak Wi-Fi networks that lacked proper security measures, which gave them illegal entry into the targeted network of the organization, which they leveraged to bypass MFA protections using stolen credentials.
Experts have extensively emphasized the importance of implementing MFA for both web services and Wi-Fi networks, suggesting that organizations should consider establishing separate network environments for Wi-Fi and Ethernet-based systems to mitigate such attacks. This protects sensitive resources more effectively, monitors network access, and also gives a reminder of the vulnerabilities posed by unsecured Wi-Fi networks.
Malware Campaign Exploits Vulnerable Avast Driver to Disable Security Defenses In Place
A malware campaign has been contemporarily discovered, solely abusing a vulnerable Avast anti-rootkit driver in order to turn off security defenses and take privileged control over infected systems. The attack allegedly attempts to leverage a kernel-mode driver to manipulate the operating system’s core functionalities, allowing the malware to turn off security processes that have been established. It exploits outdated but trusted software, which critically highlights the risks posed by unpatched drivers that can be managed or, more precisely, exploited by cybercriminals to gain illegitimate control and access over valuable information assets and systems.
The driver we are discussing interacts directly with the core of an operating system, positively allowing malware to bypass security measures and disable key protective software. To prevent such attacks in the future, subject-matter experts recommend implementing specific rules to block vulnerable drivers and using technologies like Hypervisor-Protected Code Integrity (HVCI) to safeguard against exploitation. Organizations must ensure they are vigilant in updating their drivers and security software to avoid falling victim to such attacks.
Cyber Extortion Incident Involving Cloud Data Storage Unveiled
The news freshly curated from authentic sources highlights the advent of an extortion campaign that involves and/or simply leverages cloud data storage services, being allegedly used by black hat hackers to sell stolen data from several organizations, enjoying a handsome amount of monetary benefits out of it. This attack was carried out by first exploiting weak security measures within the cloud storage platform. The weak measures included the lack of Multi-Factor Authentication (MFA) and layered defense strategies.
Malicious attackers exfiltrate sensitive data from several organizations, including telecom and financial companies, gaining unauthorized access to data-sensitive systems. These ill-intent attackers threatened their victims to pay hefty ransoms, failing to which the data would be released on public platforms. But to our relief, reports suggest that the attacker has been allegedly arrested and put behind bars for his illegal deeds.
This cybersecurity incident highlights the need to deploy robust authentication measures when utilizing cloud storage services. Experts advise organizations to safeguard against such attacks and to ensure that MFA is implemented across all platforms—particularly those used for processing and storing sensitive PII (Personal Identifiable Information) relating to customers.
Telecom Company Detects Intrusion Attempts from External Network
Recently, this burning news has been making headlines in the esteemed columns of newspapers. T-Mobile, a well-established US-based telecom company, formally reported to have detected intrusion attempts from an external network that were explicitly considered malicious. Illegal attempts were made to infiltrate the telecom’s systems, but to our relief, T-Mobile already had well-established layered security defenses in place, which potentially helped contain the adverse effects of the attack. The organization found that the attackers were using discovery-related network commands in an attempt to probe the topography of its network and assess potential vulnerabilities.
After the incident was first identified, T-Mobile acted promptly by meticulously cutting off connectivity to the external network and preventing any lateral movement across its systems. This timely report underscores the importance of robust monitoring and swift action when dealing with such external threats. This cybersecurity incident, yet it didn’t materialize in the first place, highlights the growing trend of cyber espionage targeting telecom companies, especially those with vital infrastructure.