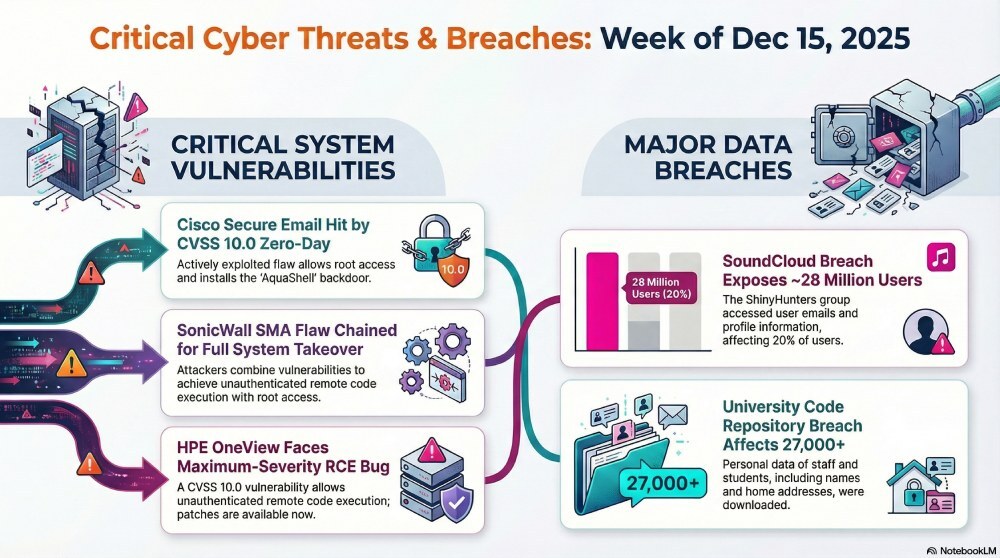
Cisco AsyncOS Exploited, SonicWall SMA Fix, HPE OneView Patched – Cybersecurity News [December 15, 2025]
Cybersecurity and email security teams faced a busy week as active exploitation targeted core infrastructure and widely used platforms. Cisco warned of a critical AsyncOS zero-day affecting Secure Email appliances, while SonicWall patched an SMA 100 flaw reportedly chained for root-level takeover. HPE fixed a maximum-severity OneView RCE issue. SoundCloud also confirmed a breach exposing user emails and profile data, alongside outages, VPN blocks, and follow-on disruption.
Cisco AsyncOS Zero Day Exploited in the Wild
Cisco has warned of a critical zero-day in AsyncOS, CVE-2025-20393 (CVSS 10.0), affecting Cisco Secure Email Gateway and Cisco Secure Email and Web Manager. Cisco said it identified active exploitation on December 10, 2025, and that the flaw could allow attackers to run commands with root access on the underlying operating system. It also found evidence of a persistence mechanism used to maintain access. Exploitation requires the Spam Quarantine feature to be enabled and exposed to the internet, which is not the default setting. Activity appears to date back to late November 2025. Cisco observed attackers deploying tunnelling tools, cleaning logs, and installing a small Python backdoor called AquaShell that waits for specially crafted unauthenticated HTTP POST requests and then runs commands.
Until Cisco ships a patch, the priority is to shrink the attack surface. Cisco recommends moving these systems back to a hardened configuration, cutting off unnecessary internet access, and only allowing connections from trusted hosts. It also advises separating administrative access from mail traffic and keeping a close eye on web logs for anything out of the ordinary. Cisco said that if an appliance is confirmed compromised, a full rebuild is currently the most reliable way to remove the persistence left behind. CISA has since added the CVE to its Known Exploited Vulnerabilities list and set a mitigation deadline of December 24, 2025.
SonicWall SMA Fix Targets Exploited Privilege Escalation Flaw
SonicWall has released security updates for Secure Mobile Access (SMA) 100 series appliances after confirming active exploitation of a vulnerability in the Appliance Management Console. Tracked as CVE-2025-40602 with a CVSS score of 6.6, the issue is a local privilege escalation caused by insufficient authorization checks in the management interface. On its own, CVE-2025-40602 is a local privilege escalation issue, so it does not automatically give an attacker remote control of a device. However, SonicWall said it has been used together with CVE-2025-23006, a higher-severity vulnerability, to create an attack chain that can end in unauthenticated remote code execution with root-level access. Although SonicWall patched CVE-2025-23006 in January 2025, the latest advisory suggests threat activity is still focused on chaining multiple weaknesses to increase the overall impact.
The affected builds include SMA 12.4.3-03093 (platform hotfix) and earlier, and SMA 12.5.0-02002 (platform hotfix) and earlier. SonicWall has provided fixes in 12.4.3-03245 and 12.5.0-02283. Researchers from Google’s threat intelligence team, Clément Lecigne and Zander Work, are credited with reporting CVE-2025-40602. SonicWall has not disclosed who is behind the exploitation or how widely it has been used. Separately, Google previously reported activity targeting end-of-life SMA 100 devices to deploy a backdoor called OVERSTEP, though it is not yet clear if the campaigns overlap. CISA has added CVE-2025-40602 to its Known Exploited Vulnerabilities list, with a remediation deadline of December 24, 2025.
HPE Patches Critical OneView Remote Code Execution Bug
Hewlett Packard Enterprise (HPE) has fixed a maximum-severity vulnerability in OneView Software that could allow remote, unauthenticated attackers to achieve remote code execution. Tracked as CVE-2025-37164 (CVSS 10.0), the issue affects all OneView versions prior to 11.00. HPE said the flaw is addressed in OneView 11.00 and has also provided a hotfix for customers running OneView versions 5.20 through 10.20, giving organizations an option to remediate without immediately moving to the latest major release.
HPE highlighted a few practical points for administrators applying the update. The hotfix needs to be reapplied after upgrading from version 6.60 or later to version 7.00.00, and it must also be reapplied following any HPE Synergy Composer reimaging operations. Separate hotfix packages are available depending on the deployment, including variants for the OneView virtual appliance and for Synergy Composer2. HPE did not indicate that the vulnerability is being exploited in the wild, but given the severity and unauthenticated RCE risk, customers are expected to patch quickly. The advisory comes after other recent HPE security updates affecting products like StoreOnce and earlier OneView releases that addressed third-party component flaws.
SoundCloud Confirms Breach Behind Outages and VPN Blocks
SoundCloud reported that the recent service disruptions and widespread VPN access failures were linked to a security breach that exposed user email addresses and basic profile information. Over the past few days, many users reported they could not reach the site while using a VPN, often seeing 403 “forbidden” errors. SoundCloud said it detected unauthorized activity involving an ancillary service dashboard and triggered its incident response process. The company confirmed that an attacker accessed some data but described the exposure as limited. SoundCloud said no sensitive data, such as passwords or financial details, was accessed, and that the exposed information was limited to just email addresses and profile details already visible on public SoundCloud pages.
The breach is reported to affect about 20% of users, which could mean roughly 28 million accounts based on publicly available user figures. SoundCloud said it has cut off the unauthorized access and does not believe there is an ongoing threat to the platform. It also rolled out additional security measures, but a configuration change made during the response caused VPN access problems, and the company has not shared when that will be fully resolved. SoundCloud also faced denial-of-service attacks that briefly impacted availability. The ShinyHunters extortion group is responsible and is attempting to pressure SoundCloud following the data theft.
University of Sydney Code Repository Breach Exposes Personal Data
The University of Sydney has confirmed that attackers accessed an online coding repository and downloaded files containing personal information relating to staff and students. The university said it detected the suspicious activity last week and confirmed it was limited to a single system. It quickly blocked the unauthorized access and secured the environment, and has notified the New South Wales Privacy Commissioner, the Australian Cyber Security Centre, and relevant education regulators. While the repository is primarily used for code storage and development, the university said it also held historical data files that should not have been retained there.
More than 27,000 people are affected, including about 10,000 current staff and affiliates as of 4 September 2018, around 12,500 former staff and affiliates from the same date, and roughly 5,000 students and alumni linked to datasets from around 2010 to 2019, plus six supporters. The staff data includes names, dates of birth, phone numbers, home addresses, and job-related details. The university confirmed the information was accessed and downloaded, but said it has not found evidence that it has been posted online or otherwise misused so far.
The university has started sending personalized notifications and expects to finish contacting affected individuals by next month. It has also set up a dedicated support service and published an FAQ page. As a precaution, people are being advised to watch for suspicious messages, update their passwords, and enable multi-factor authentication where possible.