Enforcement rules for DMARC for optimum protection against phishing and spoofing
Just like SPF offers domain owners the choice between Softfail and Hardfail, DMARC has three enforcement rules: none, quarantine, and reject. Each has its own significance and relevance in the DMARC compliance journey.
The adoption rate took a steep surge after Google and Yahoo made it mandatory for all bulk senders to deploy DMARC. As of September 2024, nearly 6.8 million domains had email sender authentication configured.
However, there is still confusion among domain owners as to which policy is right for their domain. Here is a detailed article on each of the DMARC policies and the percentage tag.
The ‘none’ policy
The ‘none’ policy is represented by p=none, and it is the most permissive setting in DMARC. It’s actually meant only for monitoring purposes. When you deploy this policy, no punitive action is taken against emails that didn’t pass DMARC checks. Emails are delivered as usual to recipients, irrespective of passing or failing the authentication checks.
It’s recommended that the ‘none’ policy be applied in the initial stage of DMARC setup so that it helps you observe and gather data on how recipients’ mailboxes are handling emails sent from your domain. You get the information that enables you to decide whether it’s time to step up the security game and start with stricter policies (quarantine or reject).
As a domain owner, you can identify the legitimate sources sending emails on behalf of your domain without disrupting email flow. What else you will know is if any spoofing or phishing attack is being attempted in your name. With the collected data, you can adjust your SPF, DKIM, and DMARC records before you apply the ‘quarantine’ or ‘reject’ policy.
Use cases for the ‘none’ policy
This monitoring policy is generally advised to be used in these three conditions–
- Companies that have just deployed DMARC start with the p=none policy so that they can understand if their SPF, DKIM, and DMARC records are correctly configured.
- Businesses that have complex email services spanning across multiple channels, like marketing, transactional, and promotional, use the p=none policy to ensure that legitimate sources are authenticated correctly before enforcing stricter rules that come with p=quarantine or p=reject.
- Lastly, p=none is used for domains that are not actively used for sending emails.
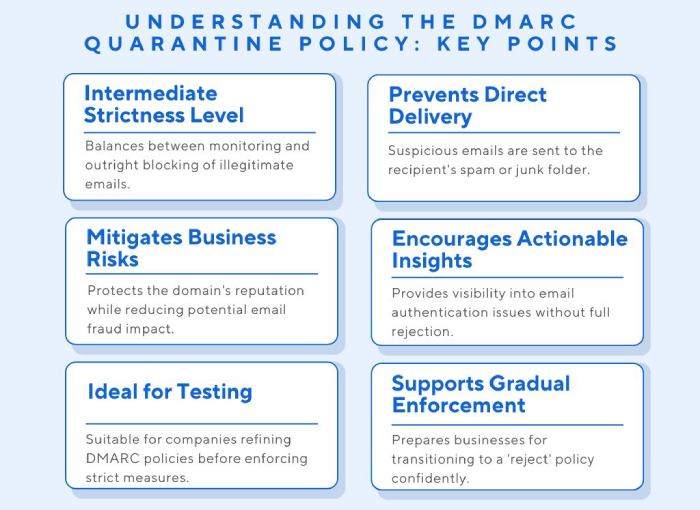
The ‘quarantine’ policy
The ‘quarantine’ policy is stricter than the ‘none’ policy. It’s useful for companies that are ready to take action on illegitimate emails sent from their domain but are still not confident to have such emails blocked outright.
When enforcing the ‘quarantine’ policy, you instruct the receiving mailboxes to deliver unauthenticated emails to spam folders. This is a safer policy because it preserves visibility while preventing phishing. The flagged emails remain accessible to recipients, allowing them to review the content if necessary.
The ‘quarantine’ policy is the stepping stone or the transitional step between p=none and p=reject. With this, you can continue collecting data through DMARC aggregate and forensic reports and use them rationally to understand if SPF, DKIM, and DMARC records need any changes.
If an unauthorized person sends a potential phishing email to one of your clients, and your DMARC policy is set to ‘quarantine,’ then the recipient’s mailbox will place it in the spam folder. This minimizes the chances of the target falling into the trap and getting duped. This ultimately reduces the rate of phishing attacks targeting your brand’s reputation, helping to instill trust among your customers.
It’s considered a safe option because if there is a false positive, the quarantined emails will remain accessible in spam folders. This way, recipients can still open the messages and report them as legitimate if necessary.
Use cases for the ‘quarantine’ policy
The ‘quarantine’ policy is mainly used in three cases-
- The p=quarantine policy is often used when domain owners are confident in their SPF and DKIM setups but want to test stricter enforcement without completely rejecting emails.
- Domains frequently targeted by spoofing, such as those in finance, healthcare, or e-commerce, often use p=quarantine to improve security while minimizing operational risks.
- Misconfigurations in email sources are quickly identified, as legitimate emails ending up in spam can be reviewed and adjusted (e.g., updating SPF/DKIM records).
The ‘reject’ policy
This is the strictest DMARC policy enforced to provide maximum protection against email spoofing, phishing, and other email-based threats, ensuring optimal email security for your domain. With the ‘reject’ policy, the receiving mail server rejects emails that fail DMARC checks. Such emails are never delivered to recipients’ inboxes (not even in their spam folders), ensuring the targets don’t open them. The rejected emails usually generate a bounce notification, providing information about the failure to the sender if they are legitimate.
However, it comes with the risk of false positives if legitimate emails from misconfigured sources get blocked. It will impact communication and reputation. There is also a drawback of operational dependencies because if you have applied the strictest DMARC policy, you must have a well-maintained email ecosystem. Moreover, you need to hire someone to monitor and analyze DMARC reports.
Use cases for the ‘reject’ policy
Not many domain owners use the ‘reject’ policy because the confidence to handle it isn’t easy to come by. Here are the situations in which enforcing the ‘reject’ policy is ideal-
- It should only be used when the domain owner or the DMARC administrator is confident that all legitimate email sources are authenticated adequately with SPF and DKIM. Companies handling sensitive data should use the ‘reject’ policy for their domains.
- This policy is also best suited for primary domains handling sensitive communications or transactional emails, where security is paramount.
The DMARC percentage (pct) tag
The percentage (pct) tag in a DMARC record lets domain owners apply their policy (‘none,’ ‘quarantine,’ or ‘reject) to a specified percentage of emails. This gradual rollout helps test the policy’s impact before full enforcement. For example, setting ‘pct=20’ applies the policy to 20% of outgoing emails, leaving the rest unaffected. This reduces the risk of disruptions from misconfigurations and allows organizations to monitor DMARC reports for issues, such as legitimate emails failing checks. It’s especially useful when transitioning to stricter policies like quarantine or reject while fine-tuning email systems.