Laposte.net’s 2025 email authentication shift: strategic insights and implementation best practices for enterprises
La Poste, France’s leading email service provider, which serves millions of users with private email addresses, has introduced mandatory email authentication requirements starting in September 2025. Now, what this means is that every email sent to Laposte.net addresses must pass SPF, DKIM, and DMARC authentication checks. If the senders don’t adhere to this, their emails will be relegated directly to spam.
The new requirement is so strict that there are no exceptions; it doesn’t matter if you are sending a transactional email from your app, a marketing campaign blast, or a simple B2B communication. If your authentication is not in accordance with La Poste’s requirements, your message won’t be placed in the inbox.
These sorts of shifts and controls are not limited to France, but are also being actively promoted in other parts of the world. It’s a clear signal of an accelerating global trend towards zero-tolerance email security policies to ward off spoofing and phishing attempts.
Why Laposte.net’s change is a sign of things to come globally
With the frequent emergence of new email authentication developments on the internet, it’s understood that email security is no longer optional or ‘nice-to-have’; it is, instead, a fundamental expectation.
Here is what is happening:
Regulatory frameworks are raising the bar
Regulatory frameworks, such as the GDPR in Europe and the CCPA in the US, have consistently focused on protecting the personal data of individuals. In this effort, they continue to enforce newer and stricter privacy policies, raising the standards. But lately, they are directing their efforts more towards email authentication and domain security as critical components of data protection.
This is happening because most phishing attacks and spoofed communications are the result of either ignored or misconfigured security measures. These vectors then lead to data breaches, ransomware attacks, business email compromises, and massive compliance violations.
Governments and regulators now know that if companies do not keep their email systems safe, it can cause big problems for everyone. That is why more and more rules are being made that require businesses to take care of how they send and protect their emails.
Laposte.net’s new rule is part of this bigger change. It is a smart way to make sure companies fix their email security before threat actors can use it to trick others or cause harm.
Laposte.net is a microcosm of industry expectations
When prominent email service providers like La Poste come with stricter rules about email security, it becomes evident that more and more companies will be doing the same sooner or later. The truth is, the whole industry is moving towards not accepting emails that are not properly authenticated.
Other big companies are already doing this. Microsoft makes sure emails follow DMARC rules for Outlook. Gmail has strong filters to block spam and detect fake emails. Yahoo also punishes senders who do not use proper email security. These changes are not random. They happen because bad actors are sending more and more tricky fake emails to steal information or cause harm.
Businesses that ignore this important change are putting themselves at risk. Just as new laws about protecting personal data have forced companies to change how they keep information safe, stricter email rules will force businesses to rethink how they send and protect their emails from scratch.
Future-proofing email infrastructure beyond just deliverability
All advanced organizations are adopting the future-proof mindset. They care for more than just email deliverability; they thrive on building resilience, trust, and defense-in-depth against evolving threats.
This is not limited to just service providers; even consumers want authentication and security protocols to be in place. They don’t just want emails to work; they want assurance that communication is safe and from a legitimate entity. With BIMI (Brand Indicators for Message Identification) emerging as the next frontier, proper authentication becomes a badge of trust.
Strategies for seamless compliance with La Poste’s new policy
Complying with La Poste’s new requirements is more than just deploying SPF, DKIM, and DMARC. You basically need to ensure the protocols are correctly configured and the sources are updated adequately. The whole effort is towards a headache-free email security setup.
So, here are some advanced practices that go beyond the basics-
Maintaining a relevant sender inventory
One of the most overlooked steps in securing your email system is knowing exactly who is sending emails on your behalf. That’s where a robust sender inventory comes in.
Every domain and subdomain matters. Even if you only actively use your main domain for sending emails, subdomains like marketing.yourcompany.com or support.yourcompany.com can also be used by third parties or attackers to send unauthorized emails. If left unmonitored, they become easy entry points for spoofing and phishing attacks.
A practical and efficient way to manage this is by using automated tools that can scan your domain catalog, map out every authorized sending service, and reveal any unknown or misconfigured sources.
This visibility helps prevent surprises later when authentication failures start impacting your deliverability.
SPF flattening and alignment optimization
SPF is a robust tool, but it has a few challenges, especially when you have to scale. One of the common issues is the limit of a maximum of 10 DNS lookups. If your SPF record refers to too many external services or uses multiple ‘include:’ statements, you’ll hit this limit, causing SPF to fail. This is where SPF flattening comes in.
The role of flattening is to convert multiple ‘include’ statements and lookups into a single list of IP addresses, making the SPF record more reliable. However, you should keep in mind that this comes at the cost of requiring constant maintenance.
As an alternative, you can also introduce SPF macros to your record, but these are complicated to add and should be done by an expert.
Alignment is equally important. It’s not enough for SPF to pass; you must ensure that the sending IP is aligned with your domain. In multi-tenant environments, where multiple services send on your domain’s behalf, strict alignment rules prevent gaps that attackers could exploit.
Best practices to rotate DKIM keys
DKIM helps make sure your emails are not changed by anyone while being sent. However, keeping DKIM working properly, especially for large businesses, requires careful attention.
One important rule is to change your DKIM keys regularly. This way, if a key gets stolen, it can only be used for a short time before it stops working.
The hard part is changing keys without causing email problems. You need to add the new DKIM settings to your DNS early, check that everything works well, and only remove the old settings after the new ones are ready.
Large companies often utilize multiple DKIM settings simultaneously. This helps when they have different teams or use outside services. To handle this smoothly, they should have clear rules and use automated tools as much as possible.
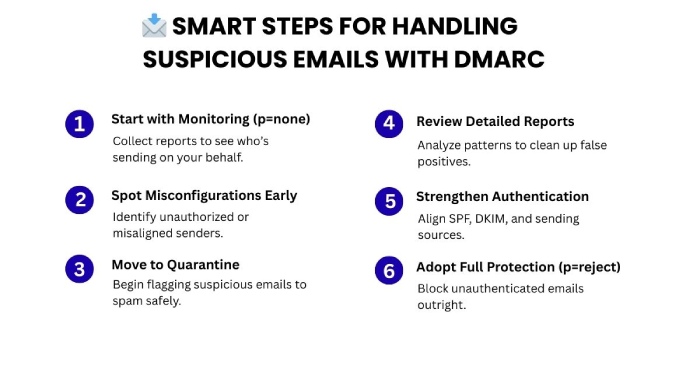
Adopting a phased approach for DMARC policy enforcement
p=reject offers the strongest protection against phishing and spoofing. But you should never jump to this policy with a new DMARC record. Doing so without careful preparation can cause legitimate emails to bounce and damage your business operations.
The smarter way to implement DMARC enforcement is a phased rollout:
- Start with p=none: Monitor reports to see who is sending emails on your behalf and identify misconfigurations or unauthorized senders.
- Move to p=quarantine: Gradually begin flagging suspicious emails to spam, while still collecting detailed reports. This helps you clean up issues without causing major delivery failures.
- Finally, adopt p=reject: Once you are confident that your legitimate senders are properly aligned and configured, enforce rejection of unauthenticated emails.
At every step, it is very important to keep checking your DMARC reports. These reports show you if any important emails are still having problems passing the security checks. This way, you can fix the issues before they cause big problems.
Taking it slow and steady helps you avoid suddenly having your emails blocked or ending up in spam. It makes sure your move to full DMARC protection happens smoothly without stopping your important messages from reaching people.
Don’t wait for the deadline
Trying to manage email security all by yourself can be tricky and risky. That is why working with experts like DuoCircle makes a big difference. DuoCircle offers powerful tools to monitor your domains and help you set up and manage SPF, DKIM, and DMARC the right way.
The best time to start is now, not when the deadline is right around the corner. Make sure your email system is safe, trusted, and ready for Laposte.net’s new rules by partnering with experts.