How does DMARC p=reject work against phishing attempts?
It’s well known that you need to have a strong defence mechanism in place to ward off phishing attacks. Speaking of which, Domain-based Message Authentication, Reporting, and Conformance (DMARC) stands out as an email security protocol. Not only does it protect your domain from being misused by attackers, but it also gives you control over how unauthenticated emails are handled.
With phishing attacks becoming more frequent and menacing than ever, your defence strategy should be such that attackers stand no chance against it. Well, that’s not exactly possible, but you certainly need a setup that makes it really hard for them to succeed. And that’s where DMARC with p=reject comes in.
DMARC lets you decide what to do with the emails that fail authentication tests like SPF and DKIM. So, if you have implemented your DMARC policy to p=reject, you’re essentially taking the strictest route. This policy tells receiving email servers to outright block any message that claims to be from your domain but fails SPF and/or DKIM checks. This means that the email won’t find its way to the targeted recipient’s mailbox— no inbox, no spam, simply blocked.
Now, let’s understand why this is the best approach to follow if you want to protect your domain from unauthorized use.
What does DMARC p=reject actually do?
Every time someone sends an email pretending to be from your domain, the receiving server checks whether that message passes two tests: SPF and DKIM. These are basic checks to confirm that the email is genuinely coming from your approved sources.
If it fails both, and your DMARC policy is p=reject, the server acts right away. The mail doesn’t reach the user at any capacity whatsoever. This means there is no possibility of it seeping into the inbox or lingering in the spam box. It’s cut off before it even reaches the recipient’s mail system.
This is what makes p=reject such an effective defense. It blocks spammers at the door, preventing them from using your domain to deceive anyone. Because the message never arrives, there’s no possibility of someone accidentally opening it or clicking on a malicious link.
Moreover, it tells the mail servers that your domain is well protected, which helps your real emails land in inboxes more reliably.
So essentially, what p=reject does is it stops the bad emails before they even get a chance to be seen, and makes sure your genuine emails are treated with more trust.
Is it really a step ahead of p=quarantine?
Yes, in terms of security, p=reject is definitely a step ahead of p=quarantine. But that’s only one side of the story.
With p=quarantine, if an email doesn’t pass the checks, it’s still delivered, even though to the spam folder. There’s still a possibility that someone will read it, but at least it’ll be marked as suspicious. But p=reject does more than that. It blocks the email entirely, so the recipient never even sees it. That works well in terms of security, but it also means you must be absolutely certain your own emails are properly configured. Let’s say if something is misconfigured at your end, even slightly, even a little, your actual emails may be blocked as well.
Why isn’t “p=reject” always the first step?
The right approach to effective DMARC enforcement is to take small steps. Just as you wouldn’t go all out with blacklisting everyone at the door without knowing who’s invited, implementing p=reject right off the bat might block your own guests.
If you directly jump to p=reject without analysing your email traffic and understanding who is sending emails on your behalf, you run the risk of blocking even the legitimate emails.
Let’s say you have third-party platforms like Customer Relationship Management, marketing services, or payment gateways sending emails on your behalf, and you forget to authenticate them properly with SPF or DKIM—they’ll fail the checks. With p=reject in place, those emails won’t just be flagged; they’ll be dropped completely. That could mean your marketing campaigns or invoices won’t reach the recipients.
So, it is important to understand that the problem isn’t the “p=reject” policy but the incorrect implementation of it. This is why we suggest that you follow a phased approach with DMARC enforcement, that is, gradually tighten the security, moving from quarantine to reject.
When should you move from quarantine to reject?
Now that you know that you can’t directly jump to the p=reject policy, let us understand when exactly you should make the switch from quarantine to reject.
You should move from quarantine to reject only when you’re sure that all your legitimate email sources are properly set up and passing authentication checks. That means every service or platform sending email on your behalf, whether it’s your main email server, a marketing tool, or a payment system, should have working SPF and DKIM records, and those emails should be aligned with your domain.
The most effective way to find out is by checking your DMARC reports on a regular basis. These will tell you which emails are passing or failing the tests, and from whom they are coming. Once you’ve resolved any problems and feel confident that only unauthorized or suspicious emails are failing, that’s a good time to transition to p=reject.
Why is p=reject the most effective way to shut down spoofing?
You now know that you need a strong defence mechanism to protect your brand from phishers and scammers. And when it comes to email security, p=reject is the strongest move you can make (provided you make a strategic move).
Here are a few reasons why p=reject is the ultimate mechanism for you to implement to prevent phishing.
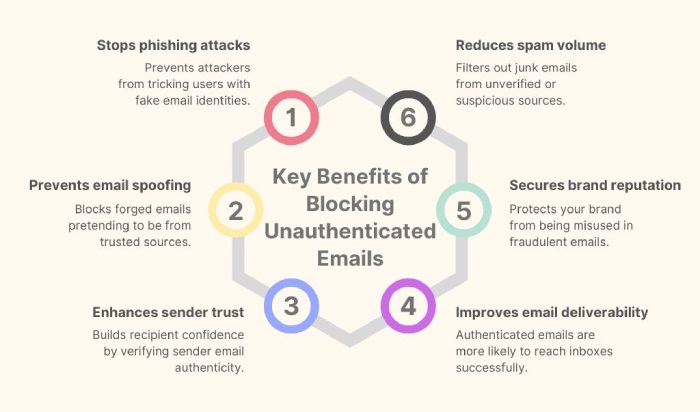
Blocks unauthenticated emails completely
This is perhaps one of the most obvious yet important benefits of using p=reject. When someone tries to send an email on behalf of your domain but fails the initial checks, such as SPF and DKIM, “p=reject” rejects the email immediately.
This step really matters because most phishing and spoofing attacks depend on getting the fake email to reach the victim. If the message doesn’t even make it through to the victim, then there’s no possibility of someone clicking on a malicious link or responding with sensitive information.
Prevents recipients from seeing fake emails
With lenient policies like quarantine, illegitimate emails somehow make their way to the recipients’ mailboxes (even though they are in spam). But with p=reject, it leaves no scope for this to happen. The users never get to see them, which means there is no chance of them falling prey to these emails by clicking a dangerous link or giving away sensitive information by mistake. It’s not just about filtering the fluff — it’s prevention at its best.
Stops domain spoofing at the source
Spammers rely on a classic trick to launch spoofing attacks, that is, sending emails that look like they’re coming from your domain. They don’t intercept your systems or forge passwords; all they do is fake “From” addresses and hope the email goes through. Without DMARC, or with a weaker policy like p=none or p=quarantine, those emails can still be delivered. They might land in the inbox. They might go to spam. Either way, they reach the user. But with p=reject in place, those fake emails are blocked the moment they fail authentication. They never leave the mail server.
Builds trust with recipients
It’s a good thing if your domain consistently passes authentication and follows strict DMARC policies like p=reject, it’s not just email systems that notice—your recipients do too.
Your emails land in the inbox more reliably, and people feel safer opening them because they’re not flagged as suspicious. And eventually, your contacts get used to seeing clean, trusted emails from you, and that builds confidence. Even email service providers (ESPs) like Gmail or Outlook start trusting your domain more, which means your legitimate emails are less likely to end up in spam.
Improves domain reputation
If you only hear bad things about someone, would you trust them? The same goes for your domain and how your recipients see it.
If your domain is being used to send phishing or spoofed emails—even without your knowledge—it hurts your reputation. Even the mail servers begin to raise eyebrows, which means if they think there are a lot of spam emails coming from your domain, they flag even the legitimate ones as well.
But when you use p=reject, you take control. You stop attackers from misusing your domain, which helps clean up your domain’s image. The fewer bad emails coming from your domain, the more trusted it becomes—and the better your real emails perform.
Not sure how to transition from p=quarantine to p=reject? It’s not a decision you take on a whim. Trust our team of experts to help you with your DMARC enforcement journey so that you domain is well protected without compromising on the deliverability.