Microsoft’s 000 Reason for Email Failure With DMARC
If you notice outgoing emails going to spam folders of only Outlook recipients and reflecting a ‘000’ reason, then it means your messages failed DMARC with ‘quarantine’ or ‘reject’ effects. You are likely to see the following snippet from the headers of email messages getting dumped in the spam folders-
Authentication-Results: spf=pass (sender IP is 106.225.909.126) smtp.mailfrom=pm-bounces.yourdomain.com; dkim=pass (signature was verified) header.d=pm.mtasv.net;dmarc=fail action=oreject header.from=domain.com;compauth=fail reason=000
What Does This Mean?
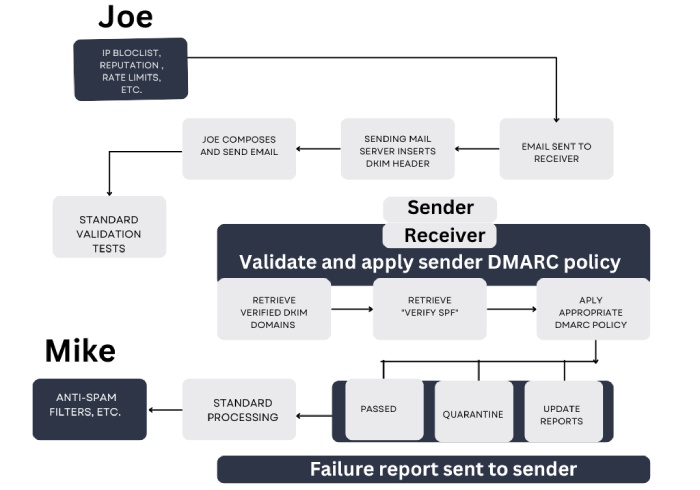
As per Microsoft, emails that failed and reflected a ‘000’ reason are the ones whose SPF and/or DKIM checks pass but DMARC fails.
You can choose to set one of the two DMARC alignment modes in your DMARC records for SPF and DKIM- Relaxed mode (represented by ‘r’) OR Strict mode (represented by ‘s’). The relaxed alignment mode means that the Return-Path domain can be a subdomain of the From address. Whereas, on the other hand, strict alignment mode implies that the Return-Path domain should be exactly the same as the domain in the From address.
Let’s say your DMARC record is set to aspf=r; in that case, the following should be a pass-
From: manager <yourdomain.com>
Return-Path: pm_bounces@pm-bounces.yourdomain.com
Since the Return-Path domain ‘pm-bounces.yourdomain.com” is a subdomain of “yourdomain.com,” the result would be considered a pass.
However, if your DMARC record is set to aspf=s, this would be reflected as a fail as the Return-Path domain and subdomain are not exactly the same.
As per DMARC specifications, either SPF or DKIM should align and pass for DMARC to pass and emails to land in the primary inboxes of the desired recipients. However, Microsoft happens to use a different method when it comes to strict alignment with SPF.
Please note that this situation may only impact you if you have a DMARC policy that allows you to quarantine or reject.
Additional Information
Microsoft refrains from rejecting emails as it takes the occurrences of false positives that may result from email forwarding or using outdated email lists into account. This also prevents legitimate email conversations from getting hampered due to configuration issues on the sender’s end.
Thus, it’s suggested that you create an updated and safe sender list.
Alternatively, you can also create a Microsoft 365 Transport rule to quarantine unauthorized inbound emails. This can be done in two ways. If mail is received by internal domains in the “From” address, you can establish and configure a transport rule to mark the emails as spam. This will place the email into the user’s spam folder instead of their primary inbox.
However, if you receive emails from domains falling outside the scope of your organization (external domains) that fail DMARC, you can set up a disclaimer, alerting users of a possible phishing attack or any other malicious activity.
At DuoCircle, we suggest using SPF, DKIM, and DMARC lookup tools to keep your records non-erroneous and opting for receiving DMARC reports to get insights into your domain’s email activities.