History of phishing-The evolution of tactics
Phishing attacks are gradually becoming commonplace. This is evident from the fact that around 94% of firms experienced phishing attacks in 2023. With time, threat actors have been able to make these attacks more sophisticated and credible. FBI’s Internet Crime Center gets the highest number of complaints of phishing attacks every year.
But the phishing landscape was not this intense for always. Phishing attacks came onto the scene almost 4 decades back. Since then, cyberattackers have been working relentlessly to come up with new phishing strategies to compel victims to share their sensitive details. To safeguard against these advancing threats, it’s essential to stay updated with advanced email security solutions. Let’s find out how phishing attacks evolved with time!
What is phishing?
Phishing is one of the most common cyberattacks that majorly targets victims with malicious emails. The threat actors pose as legitimate organizations and compel the email recipients to click on malicious links or download suspicious files. More often than not, the subject matter of these emails carries a tone of urgency or desperation. The ultimate goal of the threat actors is to gain access to the sensitive data of the victims, such as credit card details, social security numbers, user IDs, passwords, and so on. The moment they get access to such details, they become vulnerable to threats like ransomware attacks, identity theft, credit card fraud, etc.
Mystery behind the use of “Ph” in phishing
Phishing means to ‘fish’ for sensitive user details such as passwords, usernames, credit card PINs, etc. Earlier, scammers preferred using ‘Ph’ instead of ‘F,’ and that’s how gradually the term ‘Phishing’ was coined.
1990s-The starting point for phishing
Back in the 1990s, more and more people were eventually getting introduced to the virtual world called the internet. AOL was a leading internet service provider back then. With the increasing popularity of the internet, the threat of phishing attacks tip-toed into the scene. In the mid-1990s, people had to pay for ‘dial-up’ access. Users could also enjoy a 30-day free trial to the Internet through an AOL floppy disk. Some users came up with tricks to extend their trial periods and keep enjoying the internet for free. Scammers used to mail legitimate internet users and try to get access to their login credentials.
One such trick that became incredibly popular and sown the first seed of phishing was the formation of the Warez community. The community members used to steal the private data of users and then used the stolen data to generate random credit card numbers. The same credit card numbers were then used to create new AOL accounts with a 30-day free trial period.
The turning point in the world of phishing- Love Bug 2000
The Love Bug attack on May 4, 2000, was a major turning point in the history of phishing. It started in the Philippines and gradually spread across the world. People were getting emails with the subject ‘ILOVEYOU.’ When a recipient opened the email, it said- ‘Kindly check the attached LOVELETTER coming from me.’ Many fell for this trap and could not keep a check on their curiosity. Clicking on the seemingly harmless .txt file resulted in downloading a worm that could overwrite image files and send a copy of the same to different contacts on the Outlook address book. As many as 45 million Windows PCs were affected by the Love Bug phishing attack.
Major e-commerce attacks
The 2000s also saw the gradual flourishing of e-commerce. Around this time, hackers shifted their attention to e-commerce and tried to make some easy and quick money through phishing. The first major phishing attack was on E-gold back in June 2001. Soon, in 2003, threat actors replicated popular websites like eBay and PayPal to trap their users by sending spoof emails. Innocent victims often got duped as they shared their personal data, like credit card details.
By 2004, phishing was an extremely popular business for threat actors. More and more hackers started targeting major infrastructure, such as financial enterprises and banks, and their loyal users. Trends such as spear phishing, smishing, vishing, keylogging, etc., also came into the scene at this time.
Ransomware attacks blended with phishing
Around 2010, threat actors started blending ransomware attacks with phishing. Some major cyberattacks around those times were the Cryptolocker ransomware attack (the first of its kind), John Podesta’s Gmail account hacking in 2016, and so on. Scammers were using sophisticated tools such as HTTPS and PowerShell to make their phishing attacks more successful.
Phishing in 2024
Phishing attacks can now impact the global economy. Social media platforms like LinkedIn, X, Instagram, and Facebook now serve as a treasure trove of personal information for the threat actors to make their emails look hyper-personalized and credible. With time, technology, too, has developed manifolds, thereby enabling threat actors to replicate and impersonate authority websites such as Microsoft, Google, and so on. The easy accessibility of artificial intelligence serves as the cherry on the cake. Generative AI tools like ChatGPT, Claude, Gemini, etc., have greatly eased the work for threat actors. Just by typing in the right set of prompts, hackers can now generate flawless emails that look credible and personalized. This not only allows hackers to save time but also increases the chance of users falling prey to malicious emails.
How to safeguard your data from phishing attacks in 2024?
With technological advancements, threat actors have been able to penetrate into our day-to-day lives with state-of-the-art tools. The only way out of this chaos is to be highly cautious all the time.
The tips and tricks below should be implemented in your everyday life to keep threat actors at bay. Have a look!
- Cyber Education is a need of the hour. Study more about the phishing attacks happening around the globe.
- Attend anti-phishing training and workshops to protect your work and personal data.
- Delete any email that raises the slightest sign of suspicion.
- Do not click on any link that you don’t trust completely.
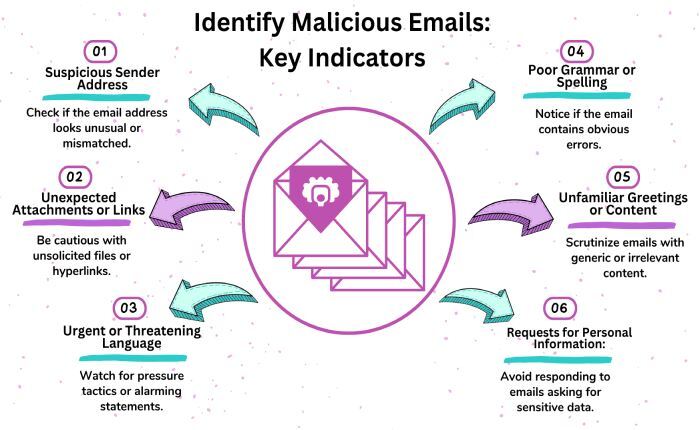
- Keep an eye out for minute details such as the company logo, spelling, content tone, etc.
At present, phishing is a huge menace in the cyber world. Stay well-informed, and stay safe!