Phishing attack on 23rd US-Taiwan Defense Conference averted!
In a recent turn of events, threat actors have been trying to target a US-Taiwanese defense conference. The meeting is going to be held in Philadelphia’s Logan Square neighborhood. Press entry will not be allowed in the meeting. Eminent speakers from different sectors, such as commerce, defense, academia, and government, will be attending the 23rd defense conference. The agenda of the meeting is to discuss the ‘future of US defense cooperation with Taiwan, the defense procurement process, and Taiwan’s defense and national security needs.’
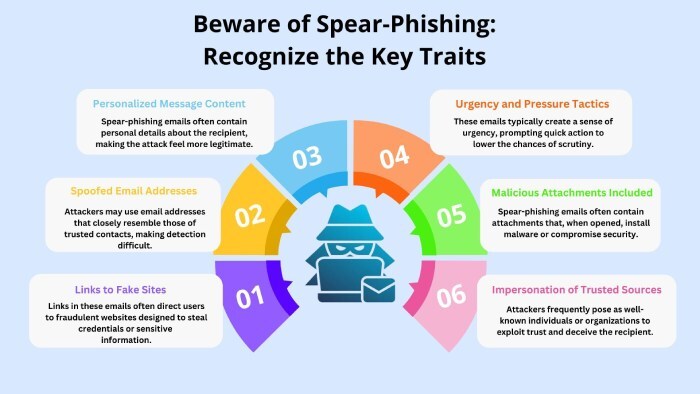
Shockingly enough, the event organizer, the US-Taiwan Business Council, received a malicious registration form. Along with it came information-stealing malware. The malware is designed in a way that its execution happens in memory, thereby avoiding detection by conventional antivirus software. However, the cybersecurity preparations were upto the mark. As a result, authorities could easily detect the attack.
History repeats itself!
A similar attack was planned on Taiwan’s defense industry 8 years ago. Some of the attendees of the 15th US-Taiwan Defense Industry Conference and the members of the Taiwan defense industry received a Chinese phishing email.
The Vice President of the US-Taiwan Business Council said that threat actors attacked them left, right, and center between 2003 and 2011. The situation worsened in 2016 and 2017. However, there has not been much activity since then.
This year, the attack is believed to have targeted the Council rather than the attendees. The threat actor pretended to be a potential attendee and sent out the email. The attacker sent out an already filled-out copy of the conference registration form in PDF format. The document was paired with a ZIP file whose ultimate goal was to download malware. If anyone had opened this LNK file, the Windows Startup folder would have been impacted.
Experts have not yet figured out any specific threat actor behind this attack. However, they believe that Chinese entities are often involved in similar anti-Taiwan activities. They are blaming East Asian geopolitics for this allegedly state-sponsored attack on the US-Taiwan Defense Conference.
Authorities were quick enough to take action, as their 20 years of experience being attacked by spear-phishing emails came in handy. As a result, no one opened the LNK file, flagged it as suspicious, and eventually deleted it after official confirmation.
When asked about their level of preparedness, the Council said that cybereducation had played a great role in keeping such phishing attempts at bay. Their entire staff is well aware of such attacks, and they are trained not to click on malicious links or open documents that appear suspicious. Also, a thorough scanning is done before opening the emails. Restricting the emails to a text-only structure and taking the system offline daily at night and on weekends have helped the Council to avert cyberattacks. They have also been air-gapping the computers and internal IT systems.
Years of experience, elaborate preparations, and a proactive nature have helped the Council to prevent this major attack on the high-profile US-Taiwan Defense Conference.