Enterprises encounter various online threats while thriving in the digital age. Online identity theft happens to be one of the prime threats that all businesses need to address. Identity theft refers to any instance of an unauthorized entity using an entity’s confidential identification data to impersonate them for malicious purposes. Such information includes addresses, names, email addresses, login credentials like username and password, passport numbers, driving license numbers, social security numbers, or bank details.
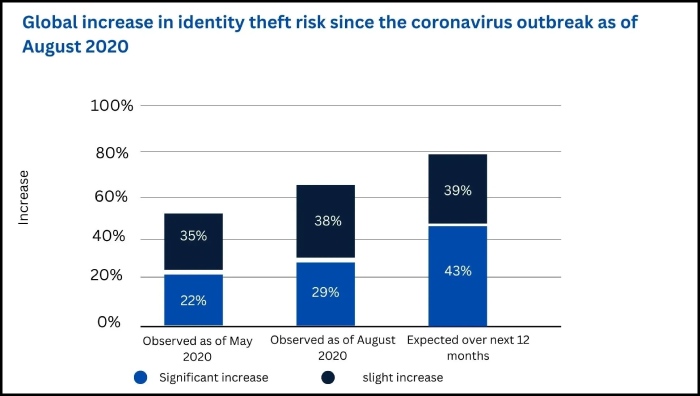
The grim statistics reveal that such malicious activities are increasing over the years, affecting many organizations globally. The imposters often pretend to be employees of an organization for financial benefits or committing other frauds, thus bringing losses for and tainting the organization’s image. The Covid-19 outbreak has also increased cases of identity theft. In a global survey, 29% of respondents pointed out a significant increase in identity theft instances as of August 2020.
What Is Identity Theft And How Has It Become More Prevalent?
The process of identity theft begins when malicious actors gain access to the victim’s personal information. It might happen in several ways, including someone overhearing a credit card number when its owner reads it out over the phone, through email security threats such as phishing, purchasing a user’s information from the dark web, or getting access to such data in any other way. Many corporate organizations are seeking cybersecurity measures to mitigate such issues.
Identity theft has been affecting employees across the globe, ultimately affecting their respective organizations. Here are some of the prevalent instances of identity theft.
- Using someone’s credentials to open different lines of credit or new credit cards
- Availing medical care using another person’s health insurance
- Carrying out unauthorized purchases through stolen debit or credit cards
- Using another person’s social security number while filing a tax return to get a refund on the claim
- Passing employment background check or renting apartments by deploying the financial standing or identity of another individual
Grim Statistics That Reveal The Seriousness Of The Threat
Here are some statistics that show how grave the situation of identity theft is.
- Over 30% of data breach victims get their identities stolen.
- In 2019, more than 14 million consumers were affected by identity theft.
- Children and older adults are critical targets for identity theft.
- It takes as little as 50 cents to purchase stolen credit card data on the dark web.
- Compared to the global average, Americans are twice more likely to be victims of identity theft.
- In 2020, credit card fraud happened to be the most common category of identity theft, followed by cons in government benefits or documents.
What Makes Employees A Prime Target Of Identity Theft?
In general, employees happen to be a soft target for malicious actors carrying out identity theft. It enables the attackers to become successful imposters while gaining access to other credentials of the respective organizations. In most instances, email data breaches lead to identity theft, which is why email security services must be adopted and taken seriously.
Employees are easy targets, given that many of them lack knowledge of sophisticated methods used in information theft. The attackers try to steal their emails, which enables them to harvest data from bank accounts. Besides, malicious actors can easily hack into the unprotected corporate or home network and intercept emails or browsing data. Once they access the employees’ mobile phones, they can quickly harvest the available personal and corporate data.
Employees are susceptible to different types of online threats that can ultimately lead to misusing their identity. They include:
- Phishing
- Skimming
- Wi-Fi hacking
- Data breaches
- Phone scams
- Mail theft
- Malware
- Tax ID theft
- Child ID theft
What Can Small Businesses Do To Secure Their Employees’ Information From Identity Theft?
Considering the seriousness of identity theft, organizations need to protect their employees from becoming victims of the threat. Here are some of the recommended measures that can prove handy.
Protecting Computers And Smartphones
Firstly, employers need to deploy sophisticated tools and software to protect the employees’ computers. These days, many organizations provide additional coverage to their employees to protect their smartphones. It would block one of the most familiar passages for malicious actors to execute their attacks. Every element in the information system network must be kept updated to get the best protection. It’s also wise to consider identity theft protection services for businesses, which can help safeguard both employee and company data from fraud and misuse.
Spotting Scams And Spams
It is relatively easy to identify specific phishing scams, while others are difficult. They are executed through emails, social networking pages, and other websites. The best anti-phishing tools must be deployed for adequate protection. Organizations must also educate employees about the associated risks of phishing, how to spot a phishing attempt, and stay away from such traps.
Strengthen The Passwords
Weak passwords attract online threats. A business owner must educate their employees on how they can deploy strong passwords. Lack of confidentiality of employees’ credentials like account IDs and passwords can easily lead to identity theft. Besides making them familiar with using strong passwords, organizations must also educate them on maintaining best practices. Deploying a two-factor authentication code (2FA) further mitigates the risks of online threats.
Some other recommendations to secure employees’ information include:
- Only purchasing online products from reputed websites
- Checking credit scores regularly
- Shredding documents before disposing of them
- Using sophisticated anti-malware tools
- Securing the organization’s email and other online accounts
With the sophistication of information technology, online threats have also gained an edge. Cybercrime is presently rocketing like never before, which makes it imperative for small and large organizations to use anti-virus and anti-malware software, anti-phishing tools, and other safeguards for protecting their digital assets. Seeking professional help from reputed agencies can strengthen the digital infrastructure of an organization significantly. Besides, small businesses need to educate their employees about possible susceptibilities.