Ransomware EDR Bypass, Apache Parquet Exposure, CISA Oil Threats – Cybersecurity News [May 05, 2025]
This week, attackers found a clever way to slip ransomware past SentinelOne’s defenses using its own update process. A serious Apache Parquet flaw just got easier to exploit thanks to a new public tool. The U.S. government is warning energy sector operators about ongoing cyber threats that use alarmingly basic tactics, and medical tech enterprise Masimo is dealing with production delays after a network breach. Plus, the Darcula phishing service is abusing iMessage and RCS. Full breakdowns below!
Ransomware Attack Leverages New “Bring Your Own Installer” EDR Bypass
A new hacking technique is being used to turn off SentinelOne’s security software during an upgrade, which lets attackers install Babuk ransomware without being detected. The issue takes advantage of a short window during software updates when protection is down.
Security experts at Aon’s Stroz Friedberg team found the issue while helping a client hit by a ransomware attack. Instead of using extra tools, the attackers ran the real SentinelOne installer, waited for it to stop the current version, and then killed the upgrade before it could finish. This left the system open, and the attackers used that moment to launch ransomware. Logs showed the security agent went offline right after the install process was interrupted.
SentinelOne’s “tamper protection” usually prevents these kinds of changes unless authorized, but this flaw lets hackers bypass that. Stroz Friedberg shared the findings with SentinelOne, who then advised customers to turn on the “Online Authorization” setting, which isn’t on by default, which requires upgrade approvals from the main console, preventing silent tampering.
SentinelOne now turns on this setting by default for new users and is reminding current ones to do the same. Anyone using the tool should check their settings to stay protected.
Tool Identifies Servers Exposed to Critical Apache Parquet Vulnerability
There’s also a new exploit tool now available online for a serious vulnerability in Apache Parquet, making it easier for attackers to find and target unpatched servers. The flaw, known as CVE-2025-30065, affects all versions of Apache Parquet up to 1.15.0.
F5 Labs created and released the tool after finding that earlier versions of proof-of-concept tools were weak or didn’t work. Apache Parquet is used by many organizations for processing large data sets, especially in big data platforms. The vulnerability is a deserialization issue in the Parquet Java library’s Avro module.
It was first reported on April 1, 2025, by Amazon researcher Keyi Li, and allows attackers to load Java objects from Parquet files without proper restrictions. Although this doesn’t give full remote code execution, it can still cause unintended actions, like making network requests to attacker-controlled servers. The tool made by F5 Labs, available on GitHub, can help system admins check if their servers are at risk using a harmless test that sends an HTTP request.
It’s best to upgrade to Apache Parquet 15.1.1 or later, and limit allowed packages using the deserialization settings.
CISA Issues Alert on Cyber Threats to Key Oil Infrastructure
Hackers are trying to break into oil and gas systems in the U.S. using very basic methods, and the government is warning organizations to be careful. These attacks aren’t complex but can still cause serious damage if systems aren’t properly protected.
CISA, along with the FBI, EPA, and DOE, said these hackers are going after industrial control systems (ICS) and operational technology (OT) used in the energy and transportation sectors. Even though they’re using simple techniques, like default passwords or exposed systems, the risk is high. Hackers can deface systems, change settings, disrupt operations, and even cause physical damage.
CISA advised organizations to shrink their attack surface by removing internet-facing OT devices, which are easy to find and often lack proper login protections. They also suggested using strong, unique passwords, securing remote access with VPNs and phishing-resistant multi-factor authentication (MFA), and separating IT and OT networks with demilitarized zones.
The advisory recommends regularly testing backups, fail-safes, and manual controls to keep operations running in case of a cyberattack. Right now, there’s no major outage, but the threat is active. Organizations should tighten security, reduce exposure, and follow the latest guidance to stay protected.
Masimo Reports Cyberattack Causing Delays in Medical Device Production
Masimo, the well-known medical tech organization, issued a warning this week about a cyberattack disrupting its manufacturing operations and delaying customer orders.
The enterprise is known for noninvasive medical devices such as pulse oximeters, brain function monitors, and remote patient monitoring systems. With around 3,600 employees and $2.1 billion in annual revenue, they are publicly listed on NASDAQ under the symbol MASI. In a filing to the SEC, Masimo said attackers broke into their on-premise network. In response, they isolated affected systems to contain the damage.
The exact type of attack is still unknown, but they have confirmed that some manufacturing facilities are running below normal levels, which has temporarily slowed down their ability to fulfill and deliver customer orders. They also clarified that cloud systems were not impacted. The investigation is ongoing, and it’s not clear yet whether any customer data was accessed.
Masimo is working with cybersecurity experts and law enforcement. So far, no hacker group has claimed responsibility, and customers are advised to monitor updates and expect some order delays.
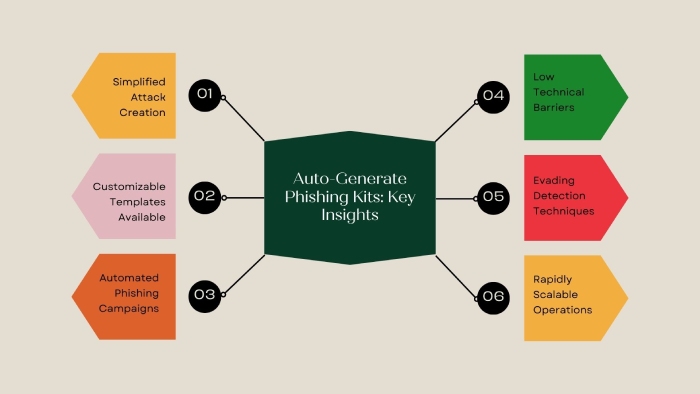
Darcula Phishing Platform Steals 884,000 Credit Cards Through Fake Texts
The phishing platform called Darcula has stolen 884,000 credit cards by tricking people into clicking fake links in text messages. These messages, sent across the world over seven months, generated 13 million clicks.
Darcula is a phishing-as-a-service (PhaaS) platform used by threat actors to target both Android and iPhone users in over 100 countries. It uses around 20,000 fake websites that look like trusted brands, often pretending to be toll fines or package delivery messages. What makes it more dangerous is its use of RCS and iMessage instead of regular SMS, which helps avoid detection.
In early 2025, researchers found it could now auto-generate phishing kits, hide its activity better, and even convert stolen card info to virtual cards. In April, it added generative AI, letting scammers target people in any language. Investigators from NRK, Le Monde, Bayerischer Rundfunk, and security enterprise Mnemonic identified 600 cybercriminals using the tool, along with its creator, who is a 24-year-old, linked to the tool’s core software, “Magic Cat.” They found groups, SIM farms, and photos of the scammers’ luxury lifestyles.
However, Darcula is still active. If you get any unsolicited email or text, don’t click on suspicious links and always verify the source directly through official websites.
To protect against evolving threats like ransomware, phishing, and data breaches, enhancing your email security with robust measures such as SPF, DKIM, and DMARC is crucial for safeguarding your organization’s sensitive information.