Global Data Breach, Nokia Data Sold, Schneider Electric Breach – Cybersecurity News [November 04, 2024]
Presenting a fresh bundle of exciting, handpicked news to enhance your knowledge and keep you informed. We will cover points revolving around news items ranging from a man being allegedly involved in significant data extortion, third-party associated risks hampering the ISMS protocols, a budding ransomware group demanding huge ransom, advancements in AI vulnerability detection, and last but not least, Okta’s recent fix for a username-related security flaw. Let’s dive deep into the details!
Global Data Heist: Hacker Gains Access to Sensitive Data
Allegedly, the sources have suggested that a 26-year-old man has been arrested for stealing data from over 160 countries using Snowflake’s cloud data service. On a provisional arrest warrant from the United States, Canadian authorities detained Alexander Moucka, a.k.a. Connor Riley Moucka, of Kitchener, Ontario. The actor could access customers’ sensitive PII data by intruding into the systems or accounts protected with minimal security.
By the approaching end of 2023, malicious hackers were very well aware of the fact that many large companies have considered Snowflake accounts as a reliable, safe option for storing and transferring volumes of data on cloud systems that were, to our astonishment, protected with little more than just a username and password. After thoroughly searching through the darknet markets for stolen Snowflake account credentials, the hackers began raiding the data storage repositories used by some of the world’s largest corporations, including AT&T. This disclosed the fact that previously personal information and phone records for roughly 110 million people were stolen.
Moucka used the hacker handles Judische and Waifu in an attempt to masquerade himself. He has attributed the Snowflake compromises to a group it calls “UNC5537,” with members based from other possibly involved international countries. This incident highlights the alarming scale of harm an individual can cause using off-the-shelf tools.
Malicious Actor Selling Nokia Data For $20,000, Nokia Remains Silent
There’s an infamous BreachForum criminal marketplace, where a recent post suggests that a hacker known as IntelBroker has breached data claiming to be related to Nokia and also put it on sale. This data has been allegedly compromised by a third-party contractor who has been closely working and collaborating with Nokia. IntelBroker has only suggested the price to be around $20,000 but it has yet not clearly specified.
On the other hand, Nokia has not released an official statement indicating breach attempts. However, the organization is currently investigating the claims and monitoring the situation closely. But still the main issue remains hidden in the fact, which has also kept all cyber security experts puzzled, i.e., why did the third-party contractors have access to Nokia’s source code in the first place? This critically raises concerns about the ISMS (Information Security Management System) handling procedures in an organizational setting. This highlights the need to implement security measures relevant to third-party partnerships.
Schneider Electric Server’s Data Breached by Ransomware
Circling around the media are news headlines in which the Hellcat ransomware group has demanded unusual ransom demand in Monero, a privacy-focused cryptocurrency. This demanded amount sums up to be exactly $125,000 in figures. These malicious threat players are new to the market, and they have publicly claimed to have successfully compromised the crucial systems of Schneider Electric. They also claim to have stolen approximately 40GB of data from established developer servers (valuable information assets).
After closely inspecting the incident, matter expert suggests that such bizarre ransom demand may be a part of the marketing strategy. The alleged group desperately is need of limelight and top position in the cybercrime world. They seemingly want to instill fear and flaunt their hacking skills among innocent mob. Schneider Electric has acknowledged the breach of their data and is investigating the matter.
Google LLM Finds Zero-Day Via Employing AI-Driven Solutions
Through a blog post medium made available from Google’s Project Zero, the masses were provided with a detailed breakthrough. This document listed that Google’s large language model (LLM), commonly called “Big Sleep,” has identified a stack-based overflow in the SQLite database engine. But what makes this identification so celebrated? This identification of vulnerability in the organizational system paves a promising pathway ahead for significant usage and involvement of artificial intelligence solutions to uncover flaws in real-world software. Big Sleep was able to discover a flaw that is yet to be released. This was made possible by explicitly targeting vulnerabilities and analyzing recent commits for similar issues.
SQLite didn’t even wait for a day and quickly patched its software. This incident is proof that AI-driven solutions can enhance the robustness of software security, consequently safeguarding valuable information assets. This highlights the importance of proactive vulnerability management in a continuously evolving threat landscape.
Okta Fixes Long Username Authorization Bypass Vulnerability
Recently, the esteemed news columns suggested that Okta has published an advisory warning regarding the organization’s system being prone or, more precisely, being vulnerable to hacking. They suggested that creating and maintaining lengthy usernames (more than 52 characters) could be easily exploited by malicious, self-centered threat actors for exercising ulterior motives.
This can bypass an Okta AD/LDAP delegated authentication (DelAuth) established mechanism. However, for our information, additional conditions are required for the exploit to work successfully. That condition states that the user needs to have previously authenticated or have created an authentication cache.
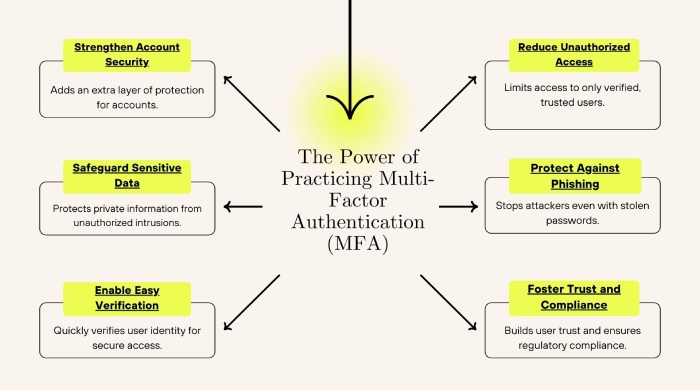
This flaw was first introduced in a July 2024 update and was soon discovered and resolved in Okta’s production environment on October 30, 2024. Most importantly, organizations practicing multi-factor authentication (MFA) were not subjected to damages caused by this flaw.
What’s the takeaway from this cybersecurity incident? Well, it is learning about the importance of multi-factor authentication systems and keenly following best practices on the internet by eradicating the use of long usernames and employing complex passwords (different combinations of alphabets, numerics, special characters, uppercase, lowercase, etc.) in online settings.