Encryption vs hashing– breaking down the differences
Encryption and hashing are the two fundamental techniques of the digital landscape. These are used to protect the integrity and authenticity of data so that threat actors don’t steal or intercept it. At first glance, these two terms may seem the same, which is why many people use them interchangeably. However, they serve distinct purposes and operate in entirely different ways. While encryption is used when you want to secure data by making it unreadable to unauthorized users, hashing does the job of verifying data integrity by generating a unique fingerprint.
It’s important to understand the differences between these two so that you can use them in ideal conditions. If you handle sensitive data, then encryption and hashing both are your fortifiers against digital data thieves.
In this blog, we’ll break down their key differences, explore how each works, and help you determine when to use one over the other.
Let’s dive in!
What is encryption
In encryption, normal readable information, called plaintext, is converted into a garbage message that is not readable. This text is called ‘ciphertext.’ Basically, the data is encoded using an algorithm so that no one except the intended recipient can read it. The intended recipient must have the necessary key to reverse the decrypted data into plaintext that they can read normally. Encryption is a two-way process— the data is first ciphered (encrypted) and then deciphered (decrypted).
Encrypting data is a common practice in industries that deal almost exclusively with private data, such as hospitals, banks, credit unions, defense, legal, energy and utilities, and cryptocurrency.
Encryption dates back to ancient Egypt, where important information was written using hieroglyphics. Only those who knew the translation code could understand the message, much like how encryption works today to protect data.
How encryption works
Encryption is based on specific algorithms that convert normal text into a ciphered form. Encryption algorithm uses a key that determines how the plain text is converted to ciphertext and vice versa. There are two types of encryption keys: symmetric and asymmetric.
Symmetric keys
In this, the same key is used for both encryption and decryption. This means the data will only be decrypted if it’s opened using the key with which it was encrypted.
Asymmetric keys
This method involves using two keys: a public key and a private key. The information is encrypted using the public key, and the private key decrypts it. The private key has to be stored secretly.
Common encryption techniques
There are several encryption techniques, but the most common ones are-
The Advanced Encryption Standard (AES)
AES is an asymmetric encryption algorithm that encrypts data in fixed-size, 128-bit blocks using key lengths of 128, 192, or 256 bits. It’s a highly secure standard that operates through multiple rounds of substitution, permutation, mixing, and key addition. Because it is speedy and strong, AES is primarily used in banking, government, and cloud security applications.
RSA
The widely adopted RSA encryption algorithm is based on the mathematical difficulty of factoring large prime numbers. The public and private keys are generated by choosing two large prime numbers and multiplying them.
Since RSA encryption is asymmetric, it eliminates the need to share a secret key beforehand, making it ideal for secure communication over the internet. However, it is computationally slower than symmetric encryption methods like AES.
The Triple Data Encryption Standard (3DES)
This asymmetric encryption algorithm is the advanced version of the original Data Encryption Standard (DES) in which the DES cipher is applied three times with different keys (168-bit total key length). It’s more often used in banking, financial transactions, and legacy systems as they require strong encryption.
Blowfish
The Blowfish encryption algorithm is a fast, secure, and symmetric block cipher developed by Bruce Schneier in 1993. It was designed as an alternative to outdated encryption methods like DES and offers strong security with variable key lengths (32–448 bits). The algorithm is suitable for applications with limited processing power, as it allows customization of key length for varying security needs.
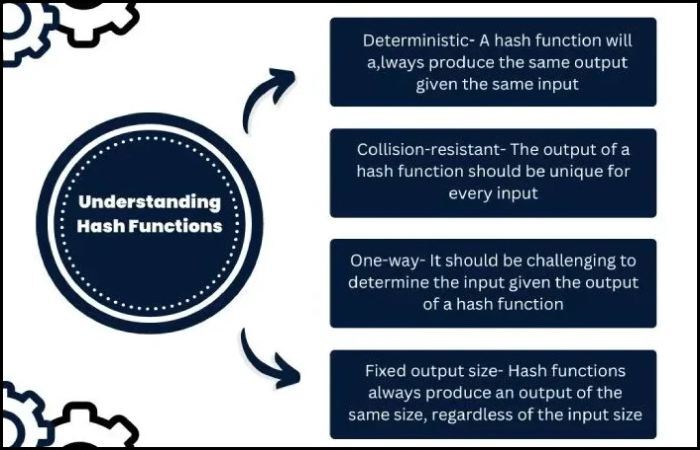
What is hashing?
Hashing converts data into a random fixed-length value. Unlike encryption, hashing is a one-way process that can’t be reversed. Companies transform data using hashing to ensure that critical details are not exploited if they are affected by a breach. It’s a fast and efficient way to deal with large amounts of data.
Usually, the hash keys are stored in the database and are compared to verify if the original information matches. This technique is more often employed in storing login passwords.
How hashing works?
A secure hash algorithm creates unique hash values for different inputs. Ideally, each unique input should produce a distinct hash.
However, in rare cases, two different inputs can generate the same hash, leading to a hash collision. This is a vulnerability that attackers can exploit.
A strong hashing algorithm is designed to resist collisions, ensuring security by making it extremely difficult for two inputs to have the same hash value.
Common hashing algorithms
Just like encryption, there are different hashing algorithms that differ in strengths and use cases-
MD5
The MD5 algorithm was introduced to improve upon its predecessor, MD4, which had severe security gaps. It generates a 128-bit hash value (a 32-character hexadecimal string) from any input.
SHA
The National Security Agency (NSA) created the SHA (Secure Hash Algorithm) in 1993. The first version had flaws, so it was improved over time. Newer versions, like SHA-256, are now widely used for security. Because SHA creates unique and strong hash values, it is considered a secure method for protecting data.
BLAKE3
BLAKE3 is a fast hashing algorithm introduced back in 2020. It’s an improvement over previous versions of BLAKE and BLAKE2 with better speed, security, and scalability. It outputs a 256-bit hash but is also capable of producing variable-length digests when required.
Understanding the key differences at a glance
| Basis | Hashing | Encryption |
| Definition | Hashing involves transforming data into a shorter fixed value known as the key. | Encryption is the process of turning plaintext into a garbage text that can’t be understood until it’s deciphered back. |
| Purpose | Indexing and retrieving items from the database. | Encrypting data so that unauthorized users can’t read it. |
| Reverse process | A hash code cannot be reversed to get the original information. It can only be compared—if two hash codes match, the data is the same; if they don’t, it is different. The original information can never be recovered from the hash. | Knowing the encryption key and method lets you easily decrypt the data and retrieve the original information. |
| Secure | More secure than encryption. | Less secure than hashing. |
| Creation of file | A hash function usually creates a unique key for each input but might rarely produce the same key for different inputs. This is called a collision. | It will produce a new key for each information. |
| Example | MD5, SHA, and BLAKE3 | RSA, AES, and Blowfish |
| Output | A fixed-size hashing algorithm. | Ciphertext of the same size or larger than the original data. |
| Length of information | Hashed information is shorter and doesn’t grow if the length of the information increases. | The length of the encrypted information is not fixed, and it grows if the length of the information increases. |
| Key management | No secret key or algorithm is used to produce a hash value. | A secret key or algorithm is required to encrypt or decrypt information. |
Hashing and encryption in DKIM
Both hashing and encryption are used in DKIM to verify that an email sent from your domain has not been tampered with in transit. Here is how each plays their role-
Hashing in DKIM
If you have deployed DKIM for your domain, then parts of the email (like the subject and body) will be hashed, typically using the SHA-256 algorithm. The hashed value is included in the DKIM signature of the outgoing email. So, when it reaches the recipient, the receiving mail server recalculates the hash and compares it to the original value to verify if the content was altered during transit.
Encryption in DKIM
DKIM uses cryptography to encrypt the hashed value using the private key, and then a DKIM signature is formed. The recipient’s mail server retrieves the sender’s public key (published in DNS) to decrypt the signature and verify the email’s authenticity.
Final words
Encryption and hashing both help protect data, but they work in different ways. Encryption keeps data safe while it’s being sent by turning it into a secret code that can be unlocked with a key. Hashing protects stored data by creating a unique code that can’t be reversed. Sometimes, both methods are used together—like encrypting files while hashing passwords for extra security. Knowing when to use each one helps keep your data safe and secure. DuoCircle offers robust email security solutions to protect your data from unauthorized access and tampering.