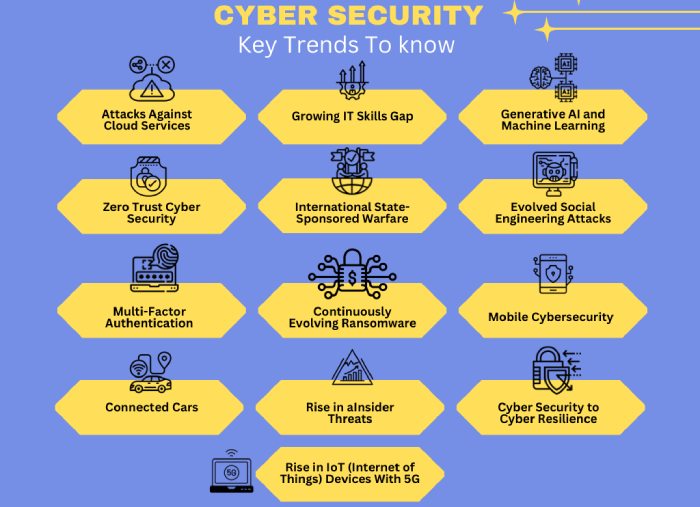
How Cybersecurity Evolved Over the Years?
Computers and the internet have been around for years now, and when something good happens, ill-intended people soon find ways to exploit it to their advantage. This is exactly what happened with computers and the internet, too.
Cybersecurity has existed since computers were invented, although the term was first included in the English lexicon in 1989. Let’s see how it has evolved over the years and what lies ahead.
1970s- The First Computer Virus and Anti-Virus
In 1971, Bob Thomas created the first-ever computer virus named ‘Creeper.’ It could creep across networks and between computers and left the message- ‘I’m the Creeper: Catch me if you can.’
Ray Tomlinson, who is better renowned as the ‘father of email,’ created a software named Reaper that could search networks and computers to detect and remove Creeper, taking the role of the first-ever antivirus. This is how the story and concept of cybersecurity started.
Although Creeper and Reaper were more of a playful experiment than a malicious threat, they highlighted the vulnerabilities of interconnected systems and laid the groundwork for the field of cybersecurity, which continued to evolve in response to ever-more sophisticated threats.
1980s- Malware Became a Thing
This decade marked the emergence and evolvement of ‘real’ malware, Morris Worm. Actually, this worm malware was originally written to map the size of the internet, however, it had some problems that used to leave an unintentional effect. It slowed down computers and clogged networks as it kept replicating. It was so powerful that it crashed many systems.
Considering the havoc wreaked by this code, commercial antivirus programs were developed and released in 1987.
1990s- The Virus Plague
This decade was infested with many computer viruses, including the infamous Melissa virus. Melissa was capable of infecting computers, encumbering email servers, hampering email accounts, and slowing the internet traffic. It collectively cost almost $80 million to clean and repair the infected computers.
Soon, the fortuity of antiviruses made its entry to detect and protect against malicious software and codes. This was the era when firewalls also emerged that helped control outside access to internal company resources. Antiviruses, firewalls, and awareness amongst users collectively damped the power of malware to some extent.
2000s- Cyber Risks Elevated Due to Digitization
People started digitizing data in the late 2000s, giving threat actors an unintentional edge and opportunities to exploit data as it was available on the internet. They just had to play a few technical tricks and moves to get access to people’s valuable data.
During this decade, cyberattacks became more sophisticated, and bad actors started hitting large companies and government bodies.
Moreover, even tech-enthusiast kids started exploiting their talent. A 15-year-old boy launched a massive DDoS attack, which took down eBay, Yahoo, Amazon, and other websites.
By the end of this decade, cybersecurity became a concern for tech-driven businesses and governments across the world.
2010s- Credit Card Breaches Increased
The number of cyberattacks rose significantly, pitying and sparing practically nobody. Businesses of all sizes, individuals, and government bodies- none was exempted. Over the decade, credit card breaches and ransomware became more frequent as cybercriminals focused on profit. For instance, a major 2013 hack of Target’s payment card information affected over 40 million customer accounts.
As data breaches and ransomware threats grew, along with the risks of business disruption, loss of customer loyalty, lawsuits, and fines, improving cybersecurity became a top business priority.
2020 to Present- Covid 19 and More
The Covid-19 pandemic brought major shifts in how people used technology. Due to the work-from-home culture, emails became even more common. People also started using online platforms (like Dropbox, Google Drive, Microsoft OneDrive, etc.) to share bulk data that were earlier being shared through safer mediums like pen drives and hard disks. And let’s not forget how digital payments became a new norm as cash was considered one of the virus carriers. All these transitions made a massive room for cyber threats like ransomware, malware, phishing, spoofing, credit card fraud, etc.
Now, almost four years later, the transition to hybrid and remote work continues, and the use of collaboration tools is rising to support a distributed workforce, improve communication, and boost productivity.
Cybercriminals are targeting these widely used tools, exploiting unsecured mobile messaging apps and collaboration platforms to access sensitive enterprise data. Organizations have learned that using these unsecured tools can lead to data breaches, compliance violations, reputational damage, and legal issues. This was evident when the SEC fined 16 firms over $1.1 billion in 2022 for using unapproved communication apps.
The Near Future
Cybersecurity was an issue for tech biggies and governments, but now the scenario has changed. Today, even kids are facing the brunt of cybercrimes. But the good thing is that companies and individuals have started taking cybersecurity seriously, and with the advocation of privacy laws and security tools, cyber resilience will get stronger.
A section that is currently lacking attention is the prohibition on the use of shadow IT. Companies must put effort toward completely eradicating this practice.
Additionally, providing staff with proper cybersecurity education enables them to identify, report, and prevent cyberattacks. Training on threats such as phishing, malware, and password security is crucial for preventing future attacks and enhancing a business’s cybersecurity readiness.
Together, these efforts are essential for improving cybersecurity and securely supporting the connected workforce of today and the future.
Final Words
We need to collectively stay vigilant against the growing incidents of cyberattacks. And now that ChatGPT and similar AI-generative tools have made their entry, it’s even easier to fool people with sophisticated emails and codes.
Amid the new era of remote working, it’s important that companies and individuals take precautionary measures, such as deploying email authentication protocols, practicing email hygiene, avoiding the use of public Wi-Fis, and reading red flags.
If you own a domain and send emails using that, then ensure it’s protected with SPF, DKIM, and DMARC. These protocols minimize the chances of email-based menaces. Contact us to book a demo.