When it comes to your business’s online security, there is no such thing as being too vigilant. Cyber threats lurk around every corner, waiting for the opportune moment to strike.
One such cyber threat is IP spoofing. IP spoofing can lead to a devastating loss of sensitive business data and assets. Read on to learn what it is and how you can protect your business from it.
What is IP Spoofing?
IP (Internet Protocol) spoofing is a type of spoofing attack. Spoof means to trick or imitate. So, IP spoofing is the term used to describe a cyber attacker imitating another computer system.
Data is sent across the internet via packets. Each packet contains information about the source of the data, including the data sender’s IP address. With IP spoofing, cyber attackers change IP addresses to impersonate credible and trusted ones. This way, the data is accepted, and the attack is free to be carried out.
IP Spoofers can gain access to sensitive data, infect machines with viruses, or crash servers. They are often difficult to detect until it is too late and the damage has been done. Any individual or business can fall victim to an IP spoofing attack, whether it offers a small business VoIP solution or graphic design services.
Types of IP Spoofing Attacks
There are different types of IP spoofing attacks, depending on the attacker’s goal. Here are three common types that you should be aware of:
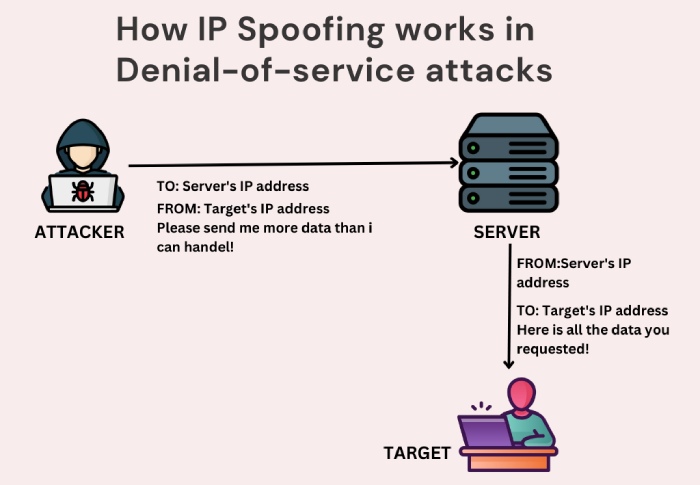
- DoS attacks: A DoS (Denial of Service) attack involves attackers sending large amounts of data to slow down or crash a server. Attackers conceal their identity with IP spoofing and remain anonymous. Because the attacker cannot be differentiated from legitimate users, they will likely not be implicated in the attack. They are, therefore, free to carry out other attacks, such as stealing personal information. Attackers also use DoS attacks to demand ransoms from their victims. When the victim pays the ransom, they regain access to their services.
- Man-in-the-middle attack: A man-in-the-middle IP spoofing attack is when a cyber attacker places themselves in the middle of an existing communication between two people or devices. The attacker thus impersonates a trusted source. This form of attack enables the attacker to gain access to an abundance of information over time. If you don’t have robust email security services in place, attackers can steal sensitive data. They can also direct the victim to fake websites where they input their personal information and credit card details.
- Botnet Attacks: Botnet attacks can cause chaos by crashing a network. Or, they can be carried out anonymously with no one noticing. With Botnet attacks, attackers infect a group of devices with malware. They either work silently in the background of a victim’s device, stealing information. Or, use a botnet attack to carry out a DoS attack, flooding the system or website architecture so that it crashes.
What are the Risks of IP Spoofing?
What makes IP spoofing so dangerous is how difficult it is to detect. As with most cyber attacks, the goal of IP spoofing is normally to make money. It’s one of the most common types of cybercrimes reported.
Attackers have lots of ways to do this:
- Steal directly from a bank account
- Trick the victim into paying them
- Steal sensitive data and sell it
- Hold sensitive data or services for a ransom
Attackers may steal sensitive information about a person or business and sell it to criminals. Personal information can subsequently be used for identity theft.
How to Protect Your Business From IP Spoofing
Although IP spoofing can be difficult to detect, there are steps you can take to help protect your business from attacks.
Packet filtering
Packet filtering uses network monitoring tools to analyze IP addresses attempting to connect with a network. Firewalls, for example, can use packet filtering to detect inconsistencies within IP addresses. If inconsistencies are detected, the IP address will be blocked from connecting to the network.
There are two types of packet filtering:
Ingress filtering: Analyzes traffic coming into your business’s network. Therefore, it helps prevent any damage from outside sources.
Egress filtering: Analyzes traffic going out of your network to ensure no one from inside your network is launching an IP spoofing attack.
Strong Firewalls
A strong firewall is your first line of defense against IP spoofing. Select a strong firewall with spoof detection capabilities. Ensure that your firewall is regularly updated and configured so that it remains an effective preventative cyber attack measure.
DLP Software
Since stealing data is the objective of many cyber criminals, installing DLP (Data Loss Prevention) software into your systems is a must. It helps to keep data safe by preventing unauthorized persons from accessing it. It also protects your business from insiders misusing data and sharing it with people outside of your network.
A contact center VoIP, for example, will need DLP software in place to protect all its VoIP customers.
DLP software offers IP protection, data visibility and secures personal and identifiable information. It uses preventative methods like encryption, as well as consistently monitoring data to ensure it remains secure.
Train Employees
To optimize business cybersecurity and minimize the potential threat of IP spoofing, train your employees to practice good cyber habits. These include:
- Use trustworthy websites with HTTPS.
- Use strong, randomized passwords that would be impossible to guess.
- Change passwords regularly.
- Be aware of spelling, grammar, and punctuation errors in emails and other communication methods to prevent email phishing attacks.
- Have security measures in place if employees are working from home.
- Not clicking on email links – go to websites via the web address bar instead.
This is especially important for remote workers. The pandemic provided fresh opportunities for cyber attacks. Employees worked from home without the same strict security measures in place as a business might have. As such, in 2020, Zscaler reported a 30,000% increase in cyber attacks aimed at people working remotely.
Nudge training is a brilliant method of instilling good cyber habits. It uses software to prompt employees to take specific actions in specific circumstances. For example, updating the internet security or thinking carefully before clicking on a link. It also flags risky online behavior and praises good online behavior.
Wrapping Up
Being the victim of a cyber attack is a daunting prospect. Businesses are especially at risk as they have much to lose through a successful attack like IP spoofing. Remain aware of cyber security risks and take steps to prevent IP spoofing.
Bio:
Jenna Bunnell – Senior Manager, Content Marketing, Dialpad
Jenna Bunnell is the Senior Manager for Content Marketing at Dialpad, an AI-incorporated cloud-hosted unified communications system that provides valuable call details for business owners and sales representatives using Dialpad’s live video calling. She is driven and passionate about communicating a brand’s design sensibility and visualizing how content can be presented in creative and comprehensive ways. Jenna has also written for other domains such as FreshySites and BlockSurvey. Check out her LinkedIn profile.