Did you receive a phishing email today from google with a document request from a friend? A user on reddit.com did and this is what he went through to figure it out.
You need to prepare yourself with the knowledge and understanding of just how important this attack vector is in context and how it is now going to be the model for NEW email-centric attacks.
‘You ain’t seen nothing yet.’
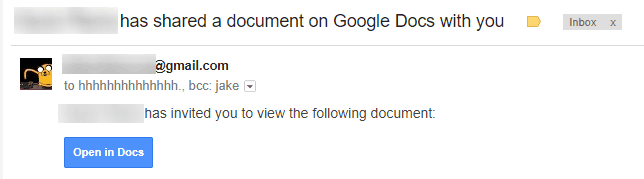
- He received an email that a Google Doc had been shared with me. Which looked reasonably legitimate, and it was from a recognized sender.
- The button’s URL was somewhat suspicious, but still but it still appeared to come from Google servers.
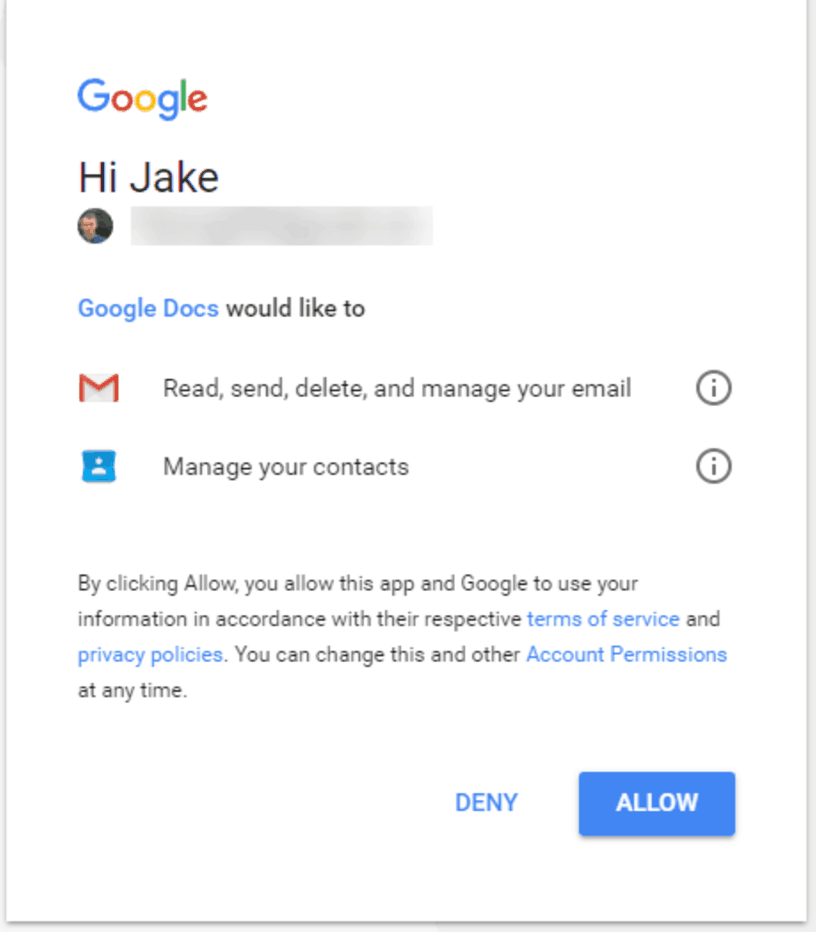
- The important part here is that he was then taken to a real Google account selection screen. It already knew about my 4 accounts, so it’s really signing me into Google. This is how this attack is different from other Phishing schemes that you may have heard about. Rather than a fake site pretending to be a real site this was the real Google.com.
- Upon selecting an account, no password was needed, he just needed to allow “Google Docs” to access my account.
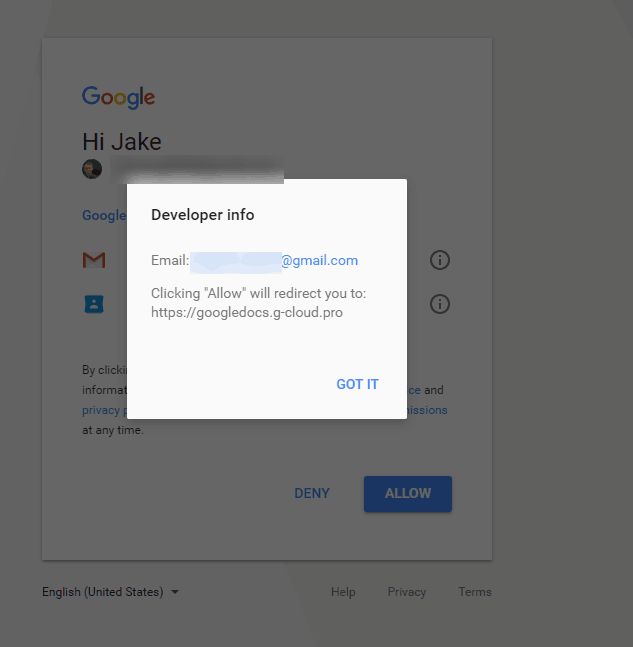
- However when he clicked “Google Docs”, it shows me it’s actually published by a random gmail account, so that user would receive full access to my emails (and could presumably, therefore, perform password resets etc).
- Shortly afterward he received a follow up real email from his contact, informing him: “Delete this is a spam email that spreads to your contacts.”
The reasons why this is so important to be aware of is NEW Attack Vector:
- Uses the existing Google login system (This is your real google account)
- Uses the name “Google Docs” (Google has now fixed this)
- Is only detectable as fake if you happen to click “Google Docs” whilst granting permission
- Replicates itself by sending itself to all your contacts
- Bypasses any 2 factor authentication / login alerts – because it’s the real you, logging into your real google account.
- Will send scam emails to everyone you have ever emailed
If you think you were affected, visit http://g.co/SecurityCheckup
Googles Response
FAQ
How do I know if I’ve been affected?
If you clicked “Allow”, you’ve been hit. If you didn’t click the link, closed the tab first, or pressed deny, you’re okay! The app may have removed itself from your account, and may have deleted the sent emails.
What do I do if I’ve been affected?
Revoke access to “Google Docs” immediately. It may now have a name endinginapps.googleusercontent.comGoogle removed it. The real one doesn’t need access.Try and see if your account has sent any spam emails, and send afollowupemail linking to this post / with your own advice if so.Inform whoever sent you the email about the spamemails,and that their account is compromised.
Google has resolved this and has rolled the fix out to all customers. Their suggestion – If you think you were affected, visit http://g.co/SecurityCheckup .
Google Official Statement
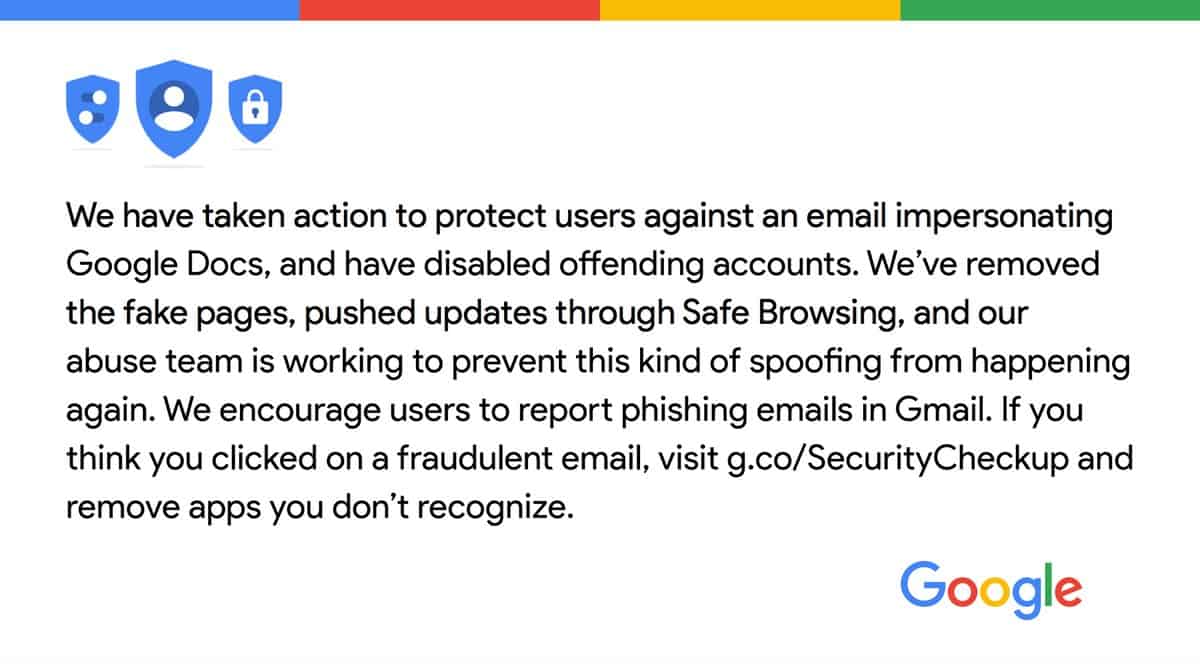
We have taken action to protect users against an email impersonating Google Docs & have disabled offending accounts. We’ve removed the fake pages, pushed updates through Safe Browsing, and our abuse team is working to prevent this kind of spoofing from happening again. We encourage users to report phishing emails in Gmail.
What are the effects?
All emails have been accessed, and the spam forwarded to all of your contacts. This means they could have all been extracted for reading later. Additionally, password reset emails could have been sent for other services using the infected email address.
This may be the payload, so it may just self replicate, and not do anything nastier. This is not at all confirmed, however, so assume the worst until an official Google statement.
I’m a G Suite sysadmin, what do I do?
Block messages containing the hhhhhhhhhhhhhhhh@mailinator.com address from inbound and outbound mail gateway/spamavservice.Locate Accounts in Google Admin console and revoke access to Google Doc app. It may now have a name endinginapps.googleusercontent.comGoogle removed it.
Google has resolved the issue – If you think you were affected, visit http://g.co/SecurityCheckup .