Keep yourself updated with this latest email security news to protect yourself from email scams and phishing attacks.
US Lawmaker Reveals Microsoft Email Compromise by Chinese Threat Actors
The US lawmaker Rep. Don Bacon has revealed in a tweet that Chinese threat actors, identified as Storm-0058, have infiltrated his Microsoft email inbox along with those of certain others.
In this recent incident, the malicious group allegedly supported by the Chinese government obtained a secret Microsoft key. It then used it with a cloud vulnerability to access several US state officials’ personal and campaign emails.
Bacon suspects that the attackers targeted him due to his support for the cause of Taiwan. He also mentioned that the FBI informed him about the breach much later, considering the incident occurred between May and June 2023.
Microsoft has now rectified the cloud vulnerability that helped malicious actors to generate fake authentication tokens. However, it is still unclear how the perpetrators obtained the secret key that could lead to serious Microsoft email scams and phishing attacks.
As we navigate this complex digital landscape, fortifying our defenses, emphasizing robust encryption protocols, and ensuring robust email backup MX strategies become imperative to safeguarding sensitive data from such persistent and audacious threats.
Alarming Rise in BEC and VEC Attacks to Outpace Malware Delivery
The cybersecurity company ‘Abnormal,’ specializing in email security solutions has noted that the rise in BEC attacks (Business Email Compromise attacks) during the first half of 2023 is 55% compared to the previous six months. It also observes that around half of all organizations have been subjected to one or more VEC attacks (Vendor Email Compromise attacks) during the same period.
This alarming growth trend has been going on for the past five years, with the latest statistics leading to the speculation that BEC attacks will soon outpace malicious delivery attacks. Threat actors glean authentication information from LinkedIn profiles and similar platforms and deploy generative AI for creating convincing emails.
VEC attacks increase mainly because many vendors are soft targets. An additional concern is that malicious actors can get their clients’ information and credentials by compromising vendors, increasing BEC attacks even further.
Cloudflare’s Threat Report Reveals Alarming Malicious Links and Brand Impersonation Statistics
Cloudflare’s first-ever phishing threats report of 2023 reveals numerous statistics concerning the use of malicious links, identity and brand impersonation, and more for email scams and email phishing attacks.
The report says that those involving malicious links are the highest threat category at 35.6% of all detected threats. Threats involving brand impersonation and identity theft are another prominent aspect of the report. The most impersonated brands are the giants like Microsoft, Google, and Salesforce.
Around one billion identity theft-related attacks were detected involving the impersonation of over 1,000 different organizations. The report points to an increase of 39.6 million attacks related to identity deception.
Besides these factors, the report also mentions that newly registered domains are also a prominent factor in threats, with 30% of threats identified involving such domains.
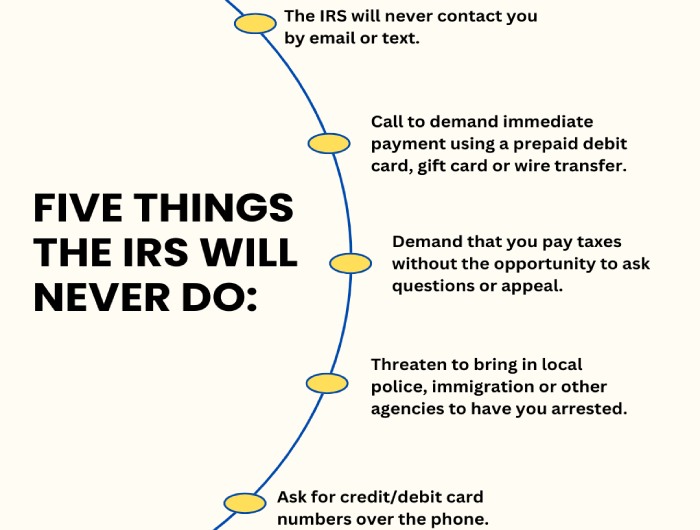
Beware of IRS Email Scam for a Third Round of Stimulus Payments
The US government issued stimulus payments to those affected by Covid in 2020 and 2021. However, US citizens are receiving emails purportedly for a third round of such payments.
IRS has warned that such ‘IRS emails’ are a scam and the IRS is not issuing another round of stimulus payments. Nevertheless, many could become victims as the threat actors use the IRS logo in these phishing emails.
Cautious email recipients can still easily avoid the pitfall as the emails contain grammatical errors. Besides, the IRS only sends such messages through US Mail, not email or SMS.
Anyone who has clicked the malicious link in the phishing email or replied to it must take immediate steps to protect their identity. Visiting IRS’s identity protection page will give you the necessary instructions to protect your identity.