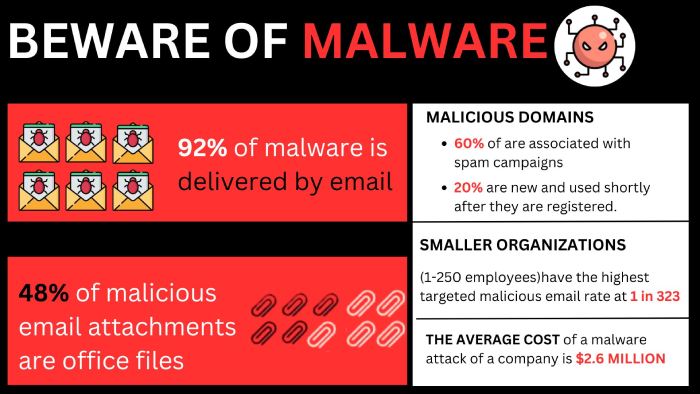
Bumblebee malware makes a comeback with email attacks. Here’s a close look at the episode, the threat actors, and how to protect yourself from such threats.
The cybersecurity world is again shaken due to the Bumblebee malware, which emerged after a two-month hiatus. The Bumblebee malware is back again with a new campaign wherein threat actors exploit Web Distributed Authoring and Versioning (WebDAV) services to create a gateway into the target organization.
This article shares the details of the attack, and the modus operandi, including how attack strategies involve giving shape to novel threats, and provides guidance on how to enhance your malware protection and stay safe from malware like Bumblebee.
How Bumblebee Malware Abused 4shared WebDAV Services
On September 7, 2023, security experts detected a resurgence of the Bumblebee malware, notable for its novel utilization of 4shared WebDAV services for disseminating harmful payloads. WebDAV, an extension of the HTTP (Hypertext Transfer Protocol) protocol, enables users to interact with remote web servers, presenting an enticing opportunity for threat actors.
Within this campaign, malicious actors employed deceptive email scams camouflaged as document scans, invoices, and notifications. These fake emails carried Windows shortcut (.LNK) files or ZIP archives containing .LNK files.
When a user interacts with or opens them, these LNK files initiate a sequence of instructions after establishing a connection to a WebDAV folder on a network drive, employing predefined credentials linked to a 4shared storage account.
Notably, diversifications in the commands used were identified, indicative of an ongoing endeavor by threat actors to refine their attack methods. Certain instances involved using the “expand” command to extract and duplicate files from the mounted drive, while others opted for “replace.exe.” File execution also used different files like “conhost.exe” and “schtasks.”
The Threat Actors Behind Bumblebee Malware
Initially detected in September 2021, Bumblebee gained popularity among malicious actors as it offered an efficient entry point into high-value enterprise environments. Notably, Bumblebee replaced the BazarLoader malware as the preferred loader for threat actors. The shift followed the public release of source code and control panel data related to BazarLoader, discouraging some malicious actors from its further use.
Intel 471’s research has revealed that Bumblebee is closely linked to adversaries previously associated with ransomware operations, including Conti and Trickbot. Given the threat actors ‘ history of ransomware activities, this connection underscores the gravity of Bumblebee’s resurgence.
One alarming development is a threat actor’s intent to use Bumblebee for malicious advertising (malvertising) campaigns. The goal is to compromise corporate users in the United States and then sell access to ransomware affiliates—a tactic known as initial access brokering.
Evolving Bumblebee Malware: What You Need to Know
In its return, Bumblebee’s latest version exhibits notable enhancements. In the past, it heavily relied on the WebSocket protocol for its Command and Control (C2) server communications. However, the updated version has shifted its approach, employing a tailored Transmission Control Protocol (TCP) mechanism. The strategic shift bolsters its ability to evade detection and significantly enhances its resilience against disruption.
Moreover, Bumblebee has abandoned relying on fixed C2 server addresses. Instead, it has embraced a Domain Generation Algorithm (DGA) strategy. The DGA generates a hundred unique domains within the “.life” top-level domain (TLD) upon execution, using a 64-bit static seed value. Bumblebee, in turn, connects to these domains by systematically cycling through the list until it locates an active C2 server IP address.
Adopting the DGA by threat actors adds a layer of intricacy, rendering the task of security teams to trace Bumblebee’s infrastructure, block its domains, and disrupt its activities a notably challenging endeavor.
How to Protect Against Bumblebee Malware
There is a lot that organizations and individuals can do to protect against the Bumblebee threat, including:
Implementing Strong Email Security
Employ robust email security solutions to detect and block malicious spam emails. Train employees to recognize phishing attempts and avoid opening suspicious attachments while providing comprehensive phishing awareness training.
Strengthening Endpoint Security
Use advanced endpoint protection software that includes behavior-based detection to identify and block Bumblebee. Restrict users’ privileges to limit the execution of suspicious files.
Enhancing Network Monitoring
Consistently observe network traffic to identify abnormal behavior that could signal potential email attacks or malware activity. Employ Intrusion Detection and Prevention Systems (IDPS) for enhanced Bumblebee detection capabilities.
Final Words
The return of Bumblebee malware highlights the ever-evolving nature of cyber threats organizations face. Using 4shared WebDAV and a Domain Generation Algorithm by malicious actors exacerbates cybersecurity challenges. Bumblebee’s links to ransomware emphasize the need for continuous vigilance and adaptable defenses. Traditional security measures falter against such sophisticated threats.
Collaboration between security experts and organizations is vital to counter this resilient malware. Staying ahead of threat actors requires ongoing vigilance and adaptation in cybersecurity.
References
- Intel471 (2023, September 15). Bumblebee loader resurfaces in the new campaign. https://intel471.com/blog/bumblebee-loader-resurfaces-in-new-campaign
- Toulas, B. (2023, September 18). Bumblebee malware returns in new attacks abusing WebDAV folders. BleepingComputer. https://www.bleepingcomputer.com/news/security/bumblebee-malware-returns-in-new-attacks-abusing-webdav-folders/