If someone offers you free DNSSEC, just know, it’s a scam. This according to Bleeping Computer. “A very clever phishing campaign targets bloggers and website owners with emails pretending to be from their hosting provider who wants to upgrade their domain to use secure DNS (DNSSEC).”
“As it’s possible to determine who is hosting a domain for a website via the WHOIS records, IP addresses, and HTTP headers, the email scam is highly targeted and impersonates the specific hosting company used by a website.” If it seems too good to be true…
Airbnb Scam
While the pandemic has kept most people from traveling and using services like Airbnb to find accommodations, it hasn’t stopped everyone. But we bet one woman wished it had stopped her before she was scammed. From Q13 Fox in Seattle, “Woman falls victim to fake Airbnb site phishing fraud, says no ordinary rental scam.”
It started when the woman, Summer Burt, found a listing on Craigslist but the owner told her to rent it through Airbnb and emailed her a malicious link as there was no email security service installed. “Burt said the fake site looked like an exact clone of the real one, and at that point, there were no red flags for her. She was then asked to wire money through a bank transfer, so she sent the man his first month’s rent and a security deposit through the site.” Total damage: $6,000. Pay attention out there.
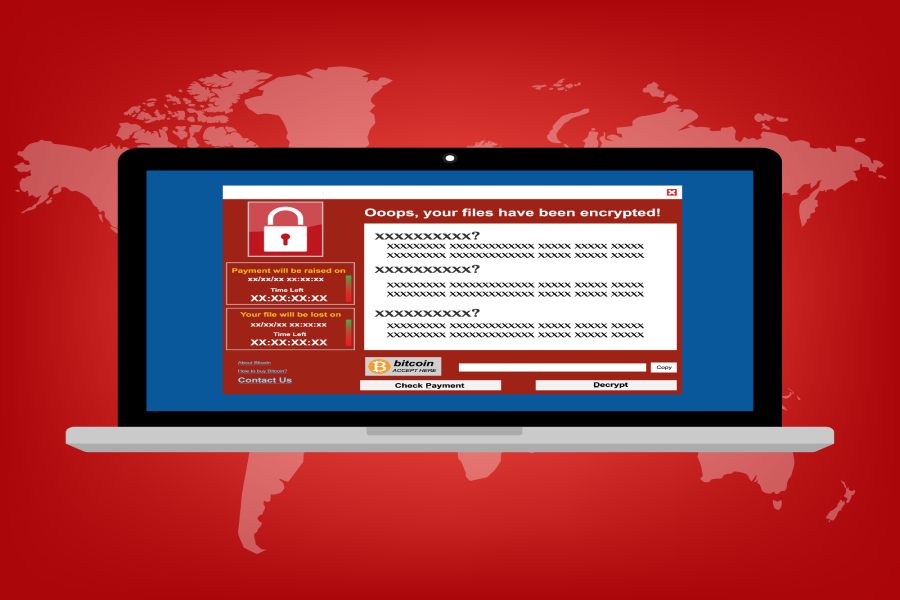
Phishing Phrontier
It’s always a little scary when you can be the victim of ransomware without ever having to click on a link, but it’s real. From Security Week, “G Data security researchers have identified a new ransomware family that attempts to spread using infected USB drives. The new piece of ransomware appears related to the ‘Stupid’ ransomware family, which is available in open-source on GitHub.” So, not only does it use a USB drive, but it’s available as an open source exploit in GitHub. Be really careful what you put in your USB slots.
Adobe Phishing Attack
The latest in phishing exploits? How about the “redirect.” According to SlashNext, a redirect is where “cybercriminals leverage legitimate commercial infrastructure sites to avoid detection and host the growing number of phishing attacks they launch.” The latest infrastructure to be used? Adobe.
“SlashNext discovered a new outbreak where attackers were found to be luring users to Adobe’s open redirect services (hosted at t-info[.]mail[.]adobe.com) through emails[1] as a means to redirect to various malicious sites. When a potential victim clicked on the link, it immediately began executing a number of redirects that would send the user to one of several different malicious webpages.”
Body Count
Hackers were at it again this week going after the healthcare industry. This time in North Carolina and Texas. According to the HIPAA Journal, “Claremont, NC-based Choice Health Management Services, a provider of rehabilitation services and operator of several nursing homes in North and South Carolina, has experienced an email security breach affecting employees, and current and former patients.”
“The Houston, TX federally qualified health center, Legacy Community Health, is notifying approximately 19,000 patients that some of their protected health information may have been accessed by an unauthorized individual who gained access to the email account of one of its employees.” When are these healthcare providers going to learn?
Celebrity Data Breach
Just because you’re rich and famous, that won’t protect you from hackers. Such is the case with LeBron James. According to SC Magazine, “The Sodinokibi/REvil ransomware gang has apparently made good on its threat to auction off files it lifted from celebrity law firm Grubman Shire Meiselas & Sacks. The group on July 1 reportedly placed legal documents corresponding to Nicki Minaj, Mariah Carey and LeBron James up for bid, with the starting price set at $600,000 per lot.” Nobody is immune.
What’s interesting here is the way the crooks are now monetizing their booty. “Auctioning off stolen data creates another potential avenue for monetization while also ratcheting up pressure on victims to pay or at least negotiate.”
BMW Owners Data Sale
It’s not just the immensely rich that are victims of this new type of extortion, but also the merely rich, like BMW owners. Also from SC Magazine, “A database of 384,319 BMW car owners in the U.K. is being offered for sale on an underground forum by the KelvinSecurity Team hacking group, according to KELA, a darknet threat intelligence firm, based in Tel Aviv.”
“The hacking group, which last week tried to sell databases related to U.S. business consulting firm Frost & Sullivan, made the BMW data available, including initials and last names, emails, addresses, vehicle numbers, dealer names, among other information.”
And that’s the week that was.