What is a quid pro quo attack?
‘Quid pro quo’ is the Latin term that literally means ‘this for that,’ meaning a mutual exchange. Although the term itself doesn’t indicate an illegal act, threat actors leverage this social engineering tactic to offer something valuable or helpful in exchange for information or access to a system.
For example, the attacker might pretend to be an IT support person offering to fix a computer problem, but in return, they ask the victim for login credentials or other sensitive information. The victim thinks they’re getting help, but in reality, they’re giving away valuable data or access to the attacker.
Let us walk you through this topic in detail.
What is a quid pro quo attack?
A quid pro quo attack is a social engineering cyberattack in which victims are tricked into giving up confidential information or access to a system. It’s a type of baiting method in which both parties get something in return. The method is built upon exploiting the core elements of human interaction to achieve an objective.
In 2023, Indian authorities raided fake IT support teams that were running in collaboration with national and international agencies alongside private sector giants. The alleged cybercriminals operated call centers in five regions of India and were duping people for at least 5 years.
The scammers sent users pop-up messages that looked like they were from well-known multinational companies, warning them about issues with their PCs. The pop-up included a toll-free number for assistance.
When victims called the fake support line, the scammers took control of their computers and charged them hundreds of dollars for a supposed fix.
Who are the targets of quid pro quo attacks?
There is no specific criteria or group of people that threat actors leveraging the quid pro quo technique target. However, mid-and-large-scale companies are more prone to being victims. The repercussions include financial losses, data breaches, identity theft, impersonation, fraud, etc.
Difference between quid pro quo and baiting
Both baiting and quid pro quo are social engineering tactics as they work on psychological manipulation and trust building to get sensitive information or gain access to a device. However, there is a difference between these techniques- in quid pro quo, the cyberactor provides some service in exchange for information or access. But, when it comes to baiting, the threat actor offers irresistible baits to the victim, such as discount coupons, cash, gift cards, etc.
Quid pro quo attacks are simpler to attempt and don’t require much preparation or high-end tools.
Difference between quid pro quo and pretexting
Pretexting requires an elaborate and well-planned scenario to fool the victim into giving information. The common pretext scenarios are the intervention of people with authorities like the police, tax department, legal aid, etc. In most cases, the malicious actor creates a sense of urgency to trigger victims to take quick action without giving them the chance to come across red flags or question anything. Unlike the quid pro quo attack, pretexting doesn’t need an ‘exchange’ to happen.
Possibilities after becoming a victim of a quid pro quo attack
With sophisticated tools and artificial intelligence, tricking people has become easier. A quid pro quo attack is generally not the main attack but an element in the chain of steps to attempt a bigger mess. Here are the possibilities of all that can happen after you are attacked-
Phishing
A quid pro quo attack might not always feel like you’re giving up something valuable. For example, you might think your email address is harmless to share, but that could be exactly what the attacker is after. Once they have it, you could be flooded with malicious emails, scams, and spam messages.
Ransomware attacks
Ransomware is short for ransom malware, which is malicious software designed to disrupt, damage, or gain unauthorized access to a system or its files.
Using ransomware, threat actors can steal or encrypt data and demand ransom in exchange for the decryption key or for not making the information go public. Sometimes, they even sell the data on dark websites, which are then further exploited by other threat actors.
BEC attacks
With the obtained access, the attacker can impersonate the compromised employee to send fraudulent emails to other employees, business partners, or clients. These emails might request payments, sensitive data, or further access to the company’s systems. Since the email comes from a legitimate account, the recipients are more likely to trust it. The attacker can trick them into transferring funds, sharing confidential information, or installing malware.
What’s even scarier is that threat actors can continue exploiting your data once they have it, gaining even deeper access and furthering the impact of a quid pro quo attack.
Other scams; employment, charity, investment, tech support, and healthcare
Employment scam:
When inflation sweeps in and recession fears grow, any job opportunity looks worth a try. Threat actors leverage this desperation of unemployed people and launch job scams. In a quid pro quo job scam, malicious actors impersonate recruiters of reputed organizations and reach out to potential job seekers, asking for personal information. Sometimes, they even ask for payments in the name of providing ‘work supplies.’
Charity scam
Threat actors offer small tokens in exchange for donations, which ultimately go into the pockets of scammers. These scams often exploit current disasters or health crises to tug at heartstrings. So, before going ahead and making donations, verify the legitimacy of fundraisers or donation collectors.
Investment scam
Investment scams promise big returns in exchange for your money. Scammers might offer fake investments in things like cryptocurrency or claim celebrity endorsements. These scams are hard to spot, especially when they involve new or digital assets.
Healthcare
Healthcare scams target people looking for cures or treatments for chronic conditions. Scammers sell fake or harmful products, claiming miraculous results. Victims may lose money or endanger their health, believing in these false promises.
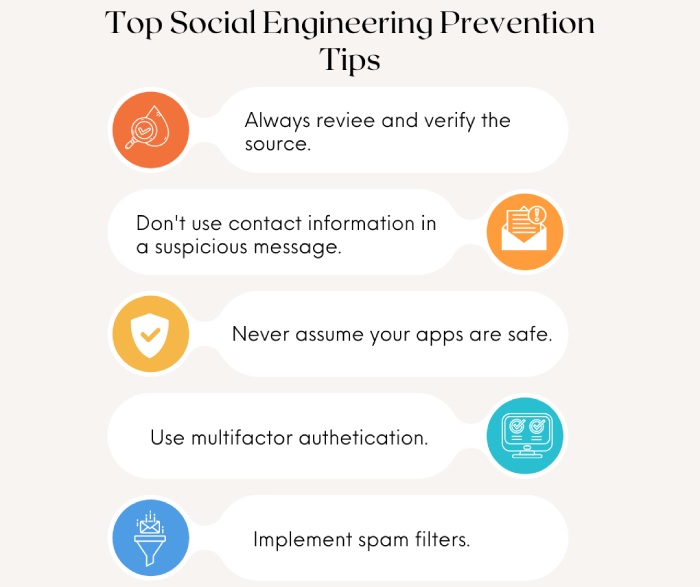
Spotting and preventing quid pro quo attacks
The Internet is as much a bane as it’s a boon. You must be cautious while browsing, clicking, and giving away your information. You will be safer if you are vigilant enough to read the common red flags.
Unsolicited offers of help
Be wary of unexpected offers of assistance, especially from unknown sources. For example, if someone contacts you out of the blue claiming to be from IT support, asking if you need help with your computer, be cautious.
Requests for information or access to a system
Keep in mind that legitimate service providers don’t ask for sensitive information or access to a system. If the person is asking for these, then question why they need it; get into the details and proceed only if you feel it’s safe. We recommend declining such requests outright for the sake of your security and reputation.
Urgency
Attackers might create a sense of urgency, saying that something needs to be fixed immediately, pressuring you to comply without thinking it through. This is often a tactic to catch you off guard.
Unusual communication channels
Random pop-ups, unsolicited calls and emails, and social media platforms are all examples of suspicious communication channels. If someone is connecting through these, refrain from replying or giving in to their requests. Legitimate support providers use established communication channels like emailing or calling after you submit a form available on their official website.
Lack of verification
If the person contacting you cannot be easily verified as a legitimate employee of a company or service provider, or if they refuse to provide proof of identity, it’s likely a scam.
To good to be true offers
Be skeptical of offers that seem too good to be true, such as free software, gift cards, or other perks in exchange for something seemingly minor, like your email address or account information.
Misspellings or poor grammar
Phishing and social engineering messages often contain spelling errors, awkward phrasing, or poor grammar. While this isn’t always the case, it can be a clue that something is off. Also, note the graphics quality used; malicious actors rarely hire professional graphic designers. So, if the image is of low quality, take it as a sign.
What to do if you have already become a quid pro quo attack target?
If you believe you are already under the radar of threat actors and have shared some information or given access to your system, then cease the interaction right away and don’t give any further information. If you have given work-related information or access, notify your IT department or the security team. Additionally, report the incident to the relevant authorities, such as the Federal Trade Commission (FTC) in the U.S. or your country’s equivalent, to ensure a thorough response to the email security breach.
Most importantly, all passwords must be changed and two-factor authentication enabled, followed by stopping access permissions.
If you suspect or anticipate financial fraud, notify your bank and request that they don’t pass transactions without checking in with you personally over the phone or calling you to the bank.
You can mitigate the disruptions by being cautious and taking suitable measures, cushioning your personal and professional reputation.