What is Cybercrime-as-a-Service or CaaS?
Don’t we all love it when tasks become easier for us? And by saying ‘all’ we unfortunately have to include cybercriminals as well. What we are talking about today is cybercrime-as-a-service or CaaS– a model that has democratized cybercrime by allowing even budding malicious actors to wreak havoc with just a rudimentary understanding of cyber menaces, access to the internet, and some money.
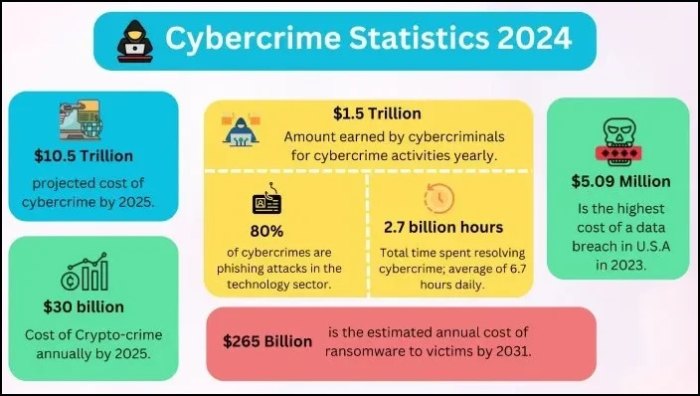
The Microsoft Threat Intelligence-Cyber Signals Report 2023 proved that the rising number of business email compromise or BEC attacks are driven by CaaS by stating a 38% increase in these services between 2019 and 2022. Microsoft also took down 417,678 unique phishing URLs between May 2022 to April 2023.
CaaS isn’t a very hot topic in the cybersecurity industry, and hence, we are sharing more about it.
Cybercrime-as-a-Service- Definition and Operating Style
CaaS is a model where threat actors offer hacking and malicious services to individuals or groups in exchange for payment. This concept borrows from the “as a service” model commonly seen in the legitimate IT industry, where services are offered on a subscription or pay-as-you-go basis– for example, software-as-a-service or SaaS.
In the context of cybersecurity, CaaS empowers newbie bad actors with limited technical skills or resources to get access to high-end hacking tools, malware, rootkits, etc., without having to develop any special skills or undergo any sort of training.
The irony is that cybercriminals run even these illegitimate services in an organized and legitimate-looking manner. They offer a subscription model, where only the paid ‘services’ or ‘products’ are accessible through legit login credentials.
The prices vary depending on the sophistication of the tool and how badly it can affect the target- so a DDoS booter can be rented for as little as $60 per day or around $400 per week. Although there are ransomware kits that can cost you as much as $84,000.
All this is disturbing to find out as now it means that virtually anyone with just a few dollars and base-level knowledge of running technical devices can play with your privacy.
In fact, Assistant Director-General of the Australian Signals Directorate (ASD) Rita Erfurt has also raised her concerns and stated that the country is observing many cases of double extortions, where victims’ networks are encrypted through ransomware, and their data is stolen to be used as an extra way to get money.
She also added how CaaS-driven malicious actors will let you know of their presence loud and proud as they are financially motivated and after a cashout.
Microsoft is on the Hunt
In 2023, Microsoft obtained legal permissions from the court from the Southern District of New York to dismantle 1152’s network– a group that runs an extensive cybercrime-as-a-service network. Microsoft got permission to seize its US-based infrastructure, which involved shutting down its key websites, 750 million fake Microsoft accounts, illicit social media pages, YouTube tutorials teaching how to bypass security measures, etc.
By far, Microsoft has identified three Vietnam-based people behind these operations: Duong Dinh Tu, Linh Van Nguyễn (also known as Nguyễn Van Linh), and Tai Van Nguyen.
This group is especially a threat as it offers its unauthorized and malicious services openly rather than on the dark web.
Primary Activities in CaaS
This is how activities unfold in standard CaaS-used cyberattacks–
Vulnerability-Discovery-as-a-Service
The first thing a threat actor does is spot a vulnerability so that they can plan to exploit it. Vulnerability-discovery-as-a-service or VDaaS is the subcategory of CaaS, where dealers on the dark web announce the services of cyberattack professionals or automated tools to find and evaluate security loopholes in targets’ devices, networks, or applications.
Exploitation-Development-as-a-Service
Up next comes the exploitation-as-a-service or EDaaS, where threat actors sell services that play with the vulnerabilities found in the above step. To drive such services, threat actors create or customize codes that are capable of taking down systems by manipulating security weaknesses.
They may also think of setting up operational weaknesses like fake wifi networks or spyware to play with the human link before launching payload computers, networks, or applications.
Secondary Activities in CaaS
An ecosystem keeps all its elements intact and in sync with each other, ensuring a long-living cycle. Similarly, there is a CaaS ecosystem that revolves around building and expanding a marketplace, community, and an extensive playground so that threat actors get more area to work upon. This drill involves the hacker community, marketing and delivery actions, and operations and lifecycle management.
Their overall agenda is to decrease entry barriers from fellow hackers and trade gains for money or assistance in cybercrimes.
Defense is Challenging Yet Necessary
It’s challenging to shield your businesses and their reputation against CaaS-using cybercriminals due to the easy accessibility and availability of sophisticated tools and services for newbie malicious actors. However, it’s also absolutely necessary to put preventive measures in place because these services trigger and facilitate widespread threats.
Thus, we strongly encourage using email authentication protocols like SPF, DKIM, DMARC, and BIMI, strong and unique passwords, backup email tools, firewalls, intrusion detection systems, etc. We are available to help you stay safe from phishing-based cyber menaces- get in touch to know how.