DKIM replay attacks: Why not all emails should be signed
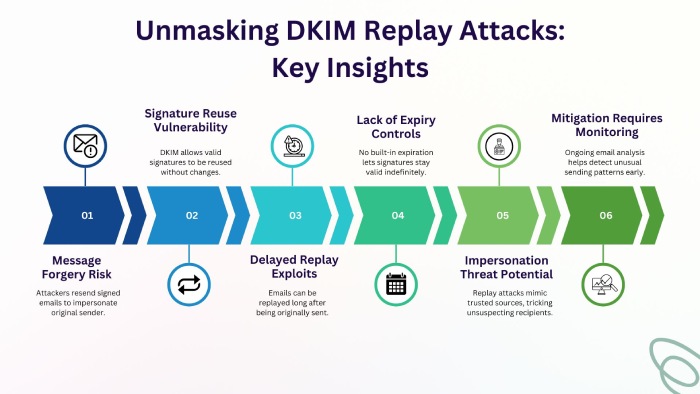
Attackers often outsmart the cybersecurity custodians, and a DKIM replay attack is one such technique exploited by them to sign, seal, and send fraudulent emails using a valid DKIM signature.
What basically happens in a DKIM replay attack is that a cybercriminal takes a legitimate email that was properly signed with DKIM, like a newsletter or promo email, and then resends it repeatedly to different people. Since the DKIM signature is valid and untampered, the fake emails pass through DKIM security filters and get delivered to the inboxes of targeted recipients. This leads to successful phishing, spoofing, and BEC attacks.
A DKIM replay attack is so stealthy and convincing that even Google wasn’t immune to being exploited in April 2025.
That’s exactly why it’s suggested to limit the use of DKIM signatures, especially for general marketing emails.
Why are general marketing emails prime targets?
Marketing emails like the ones that include newsletters, announcements, and event invites are easily accessible by many recipients and often lack user-specific content. Since these are archived online or in inboxes, cyberattackers can easily obtain them.
So, when these emails are signed by DKIM, the signature only proves that nobody tampered with the email content in transit. So, there is no method involved in DKIM that verifies if the sender is really who they are claiming to be— this is something that malicious attackers take advantage of.
So, if they get their hands on an email with a valid DKIM signature, they resend it to multiple people. Since the content is the same for everyone, security systems don’t find anything faulty or suspicious.
What should be DKIM signed vs what shouldn’t?
When deploying DKIM, it’s important that you consider which category of emails should be signed. Signing every outgoing email can backfire. Here’s what to consider-
Always sign transactional emails
Transactional emails—like password resets, order confirmations, account activity alerts, and invoices—should absolutely be DKIM-signed. These kinds of messages contain sensitive details, and if they get tampered with in transit, they can lead to grave cyberattacks. Moreover, these messages have unique, user-specific details, so there is a far lower possibility that a threat actor will abuse them for DKIM replay attacks.
Reconsider signing mass marketing emails
Mass marketing emails—like newsletters or promos—are a bit tricky. They’re sent to everyone, have generic content, and are easy to find. If you DKIM-sign them, you’re basically giving attackers a green signal to reuse that signature. They can resend the same email to others, and it still passes as legit. Since the email isn’t personalized, spam filters don’t catch anything fishy.
So, don’t just sign every email by default. For bulk marketing emails, either skip DKIM or use short-term keys. Better yet, add user-specific details or one-time links to make replay attacks harder.
Mitigating DKIM replay risks
Following the best practices for using, managing, and storing DKIM keys helps you ward off most DKIM-oriented attacks. So, start by using longer keys with shorter validity and rotate them frequently— this ensures that even if your keys are stolen, an attacker can’t keep abusing them for long.
Moreover, don’t use DKIM in isolation; instead, use it in tandem with SPF and DMARC. SPF will help verify the sender’s legitimacy, while DMARC will instruct receiving mail servers to quarantine or reject potentially fraudulent messages sent by impersonating your domain.
If you want our help deploying and managing SPF, DKIM, and DMARC, reach out to us. We have a team of experts ready to defend your email infrastructure.