Emails are the primary means of commercial, professional, academic, diplomatic, and other official correspondence. An office employee receives around 200 emails daily, and not all of these emails come from harmless or relevant senders. Ninety percent of the email exchanged globally accounts for spam email. Spam email and its associated cyber risks are known to all – it is the root cause of malware, Trojan, and virus spread through email. Data breaches, compromise of confidential intelligence, and financial fraud are initiated by spam and phishing emails commonly appearing as an ’email security alert.’
What Is An Email Security Alert?
An email security alert is a red alert for any suspicious activities in users’ email accounts. Email service providers often use such alerts as a phishing prevention measure to warn users of any new logins from different devices, password changes, access requests, etc., that may have occurred on their accounts. However, not all email security alerts that notify of some suspicious activity about an account are genuine. Unsuspicious users tend to overlook whether an email comes from google.com or g00gle.com. There are many ways through which attackers bypass anti-phishing services, and fake email security alerts are one of them.
How To Spot A Fraudulent Email?
While most email providers come with spam filters of their own, it is essential to ensure that some ransomware protection protocols are in place for the organization. Identifying a spam email is the first and foremost step to ensuring email security, and here are some safeguards to spot a fraudulent email:
- Look For Errors: This may sound very obvious, but spam and spear-phishing emails come with intentional spelling errors and camouflage. The infamous PayPal scam and countless other instances warn of the efficacy of this attack scheme wherein strikingly similar logos and difficult-to-spot spelling or grammatical errors are used. Hence, it is good to read emails with caution.
- Watch Out For Unusual Requests: Business Email Compromise (BEC) scams can happen to anyone in an organization. Therefore, if you receive an untimely payment or draft clearance request from a supplier or even a superior within the organization, you must consider verifying the email before complying with the request.
- Check Relevance: Always use reason over fake emergencies presented in emails. The email account was probably not compromised. The password wasn’t probably changed, but panicking and clicking on links attached to such fake email security alerts can lead to an actual account compromise.
- Check Language: The user can know a lot about the sender from the tone of a message. If an email from one of the regular communication threads is signed differently or sounds unusual, it probably is. Always check the language for familiarity.
What Happens After Being Attacked?
Attackers usually request money transfers, login credentials, payment card details, or company intelligence through email forwarding spams. In other cases, malicious links and attachments download Trojan, virus, or malware (particularly ransomware and spyware) into the recipient’s device, which eventually takes over an entire organization’s information network. An email infiltration also increases the risks of spear-phishing attacks in the future.
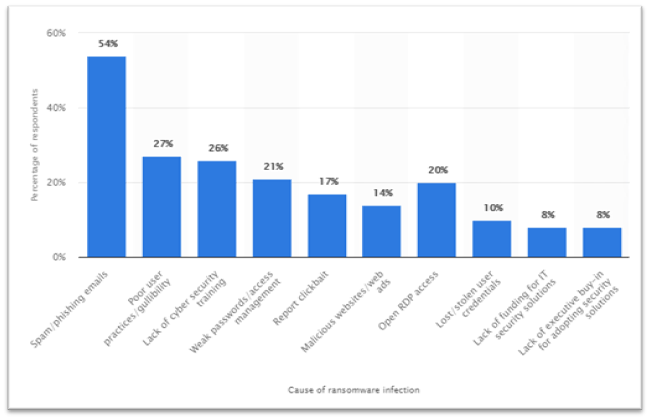
(Source: Statista)
How To Prevent Email Security Risks?
Email hosting services appeal to their customers with their robust email security service, but an attacker might still penetrate the business network and disrupt operations despite these protective measures. Users can adopt the following control measures at an individual and organizational level to prevent email security risks:
Employee Awareness And Training
Human error is accountable for 95% of all cybersecurity breaches. An accidental click and the inability to spot and handle an attack can lead to an enormous and irrevocable loss of information assets and intelligence. That’s why employee training and cybersecurity awareness are essential.
Access Control
Implementing access control measures ensures that only select employees have access to sensitive business files. This action, in turn, limits the risk of data loss if employees’ email accounts get compromised.
WFH Protocols
Encouraging employees working remotely from home and on personal devices to use VPN while accessing official systems is inevitable. Other ‘Work from Home’ protocols, such as safe internet connection, firewalls, VPN, etc., must also be strictly observed.
Strong Password
Email security depends a lot on healthy password habits. Businesses must instruct employees to change passwords frequently. They must use password managing tools and a combination of disparate characters for all their passwords.
MFA
Enabling Multi-factor authentication for all employees is an effective cybersecurity measure as it uses more than one strategy to grant access to sensitive files and systems.
How To Ensure Minimal System Downtime?
Cyberattacks, especially those involving malicious emails, can never be entirely avoided, and despite the best email security services, attacks can still occur. Organizations experience downtime, system failure, and disruption in business correspondence in such unfortunate events, which costs millions of dollars.
Email backup proves to be a life-saver in adverse situations like this. It might take days, months, or even years to overcome the effects caused by ransomware or a DDoS attack. Identifying the entry point and patching loopholes is a tedious process even with help from external cyber experts and government agencies, and organizations cannot afford to wait all along. Customers’ safety is just an addition to this list of security concerns. A backup copy of all critical conversation threads, files, documents, and other data stored on the cloud or external drives ensures uninterrupted workflow and business continuity. Organizations can restore systems quickly with such controls without complying with the exorbitant ransom demands of adversaries for the decryption key.
Email archiving and backup solutions are a must for all SMEs and even large businesses. These tools can be helpful in the case of cyberattacks or when files get accidentally deleted, necessitating a quick recovery. MX Backup services and backup solutions for businesses ensure that no email ever gets lost, whether in a cyberattack or due to an error.
Final Words
The idea of email security alerts presents an easy opportunity for malicious actors to launch successful phishing scams. They manage to trigger the fear of account compromise for most users. Since there is no fool-proof phishing protection strategy to safeguard from such scams, having email backup and regularly updating it will prove a robust email security measure.