Implementing DKIM the right way: A guide for ESPs
You might have heard that email authentication protocols are only for businesses, but that’s not entirely true!
Don’t you think email security is crucial for everyone, including businesses that send email campaigns and email service providers (ESPs) that facilitate them? If so, you can agree with us when we say that email authentication is a must for every entity in the email ecosystem, including the ESPs.
Here’s why it matters: email scams are everywhere, from phishing attacks to spoofing emails, attackers are always on the lookout to impersonate unsuspecting users and deceive them. There’s no way that these hackers can cease to exist, but as an email service provider, you can give assurance to your clients that the email coming into the mailbox is indeed authentic and has not been altered along the way. That’s where DKIM comes in!
But the thing is, most email service providers struggle with implementing these protocols, particularly DKIM. In reality, it’s not that difficult to configure DKIM to ensure that the outgoing emails aren’t tampered with; it’s about following the proper steps.
In this article, we will talk about how you can implement DKIM properly, what common pitfalls are, and how you can assure your recipients that their emails are secure and trustworthy!
Common mistakes that ESPs make while implementing DKIM
There’s a reason we said earlier that most ESPs struggle with implementing DKIM. Most of them make some common mistakes that render their authentication protocol ineffective. This is what makes systems and clients vulnerable to scams.
Let’s take a closer look at some of the common mistakes ESPs make when implementing DKIM:
Using one key for everyone
A lot of email service providers (ESPs) take shortcuts with DKIM by using the same key for all their customers. It’s easier for them because they can give everyone the same instructions, use the same record for DNS, and sign all emails with one key. Yes, this might be convenient, but here’s the catch: if that one key gets hacked or leaked, every single customer using it is at risk. It’s like having one master key for every lock in a building—if someone gets a hold of it, they can open every door.
Not rotating the keys
Another common problem is that the ESPs don’t update the DKIM keys frequently enough. As changing keys involves altering DNS records, this additional step might seem like an unnecessary hassle to many of them. That’s not all! Some ESPs even ask their customers to rotate the key themselves, which we all know is all the more unlikely to happen. In such cases— where the same key is used for many years, say 5-10 years, it creates a significant security risk. If an attacker cracks this key, they might exploit it to launch malicious attacks.
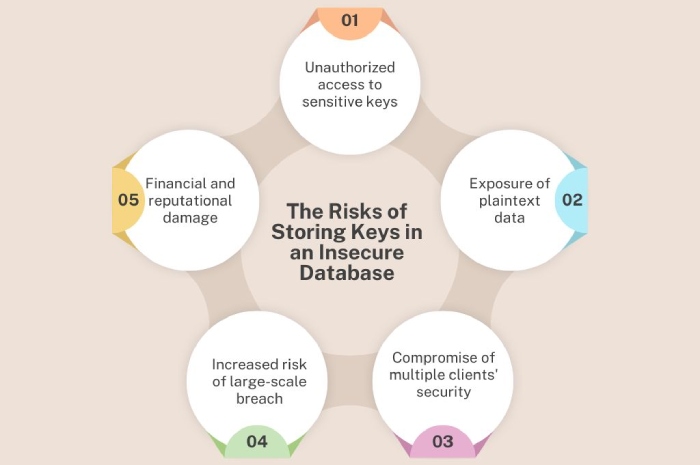
Storing keys in one place and in plaintext
Now, even if an ESP decides to do things the ‘right way’ by giving each customer their own unique key and trying to rotate them, there’s another issue. Many email service providers tend to store all their clients’ keys in one central place, and that too in plaintext (that means unencrypted). This certainly makes things easier for them to manage, but it’s also like putting all your eggs in one basket. If someone hacks into that database, they could steal all the keys at once.
Considerations for ESPs to keep in mind when implementing DKIM
Being the facilitator for sending email campaigns, it is the responsibility of the ESPs to ensure that the emails that are sent out from their infrastructure are safe and secure. For this, simply implementing a protocol isn’t enough; it’s about doing it the right way.
Now that we know everything that can go wrong with the DKIM implementation strategies of the ESPs, let’s take a look at some of the things that you should keep in mind while enforcing DKIM:
Never share the same key with all your clients
Your clients deserve assurance that their email communications are secure and no one alters their messages along the way. A way to ensure this is to assign them their unique DKIM key. We get that it might be easier for you to use the same key for multiple clients, but this ease of convenience can cost you and your clients a lot in the long run. If the common key is hacked or it somehow gets into the hands of an attacker, it can lead to phishing attacks, damaged reputations, and a loss of trust in your platform.
Rotate the keys regularly
Using the same key for a client for a long time is just as risky as using a common key for all your clients, if not more. The longer you use a key, the easier it becomes for an attacker to guess it and the riskier it gets. But rotating the DKIM keys regularly, let’s say once in 3 or 6 months, will keep your clients safe from email-based cyberattacks. Although it might seem like extra work, it is definitely worth the effort. It not only protects your clients against phishing and spoofing attacks but also shows them that you take their email security seriously.
Store the keys properly in a distributed manner
The last thing you want is to present all the DKIM keys on a platter to the attackers, and storing all the keys in one place is like doing exactly this. To ensure that this does not happen, you must store the DKIM keys in encrypted form across multiple locations instead of a single centralized one.
The solution to DKIM configuration woes
Configuring DKIM isn’t easy. Yes, we said it!
We understand that setting up DKIM can be tricky, and doing it all by yourself— generating keys, updating DNS records, and ensuring everything works seamlessly, can be a lot. But with our team at DuoCircle by your side, you don’t have to worry about any of it. Get in touch with us today, and we will take care of it all so you can focus on what you do best—delivering excellent email services to your clients!