This article explains CISA’s Secure by Design and Secure by Default development principles and how they prioritize security in product development. Discover how these principles protect against prevalent threats and vulnerabilities and how these principles will help organizations make security a standard expectation for customers.
One of the top news in the cybersecurity world today was provided by CISA (U.S. Cybersecurity and Infrastructure Security Agency), which has introduced two development principles for product development to act as a shield for organizations against cybercriminals and their malicious intent. Let us see what these are and how they will improve cybersecurity.
What is Secure by Design?
CISA’s Secure by Design involves development practices to prioritize security by incorporating the entire product development lifecycle. To build security into products and systems from the outset instead of as an afterthought, Secure by Design will minimize potential vulnerabilities and reduce costs and time.
Secure by Design identifies threats via comprehensive risk assessments during manufacturing, which are considered during the blueprinting stage to incorporate protections to combat cyber threats. Specialists from Netcorp, a software development company, advise that a proactive approach in identifying risks early can significantly mitigate the possibility of exploitation during later stages of product development.
To ensure product and platform security, Secure by Design will guide manufacturers to adopt a holistic approach where software manufacturers will include security at each stage and not “bolt it on” later. It will also require organizations and businesses to make safety a business priority instead of a technical feature to identify and address security vulnerabilities before they become a problem.
By implementing the Secure by Design policy, organizations could keep the risk of security vulnerabilities of their products in check, leading to robust security and improved customer trust due to a significant decrease in successful cyber attacks.
What is Secure by Default?
Secure by Default is the other principle that organizations should pay attention to. Secure by Default means an organization’s products and services are resilient against common cyber threats without additional costs or charges.
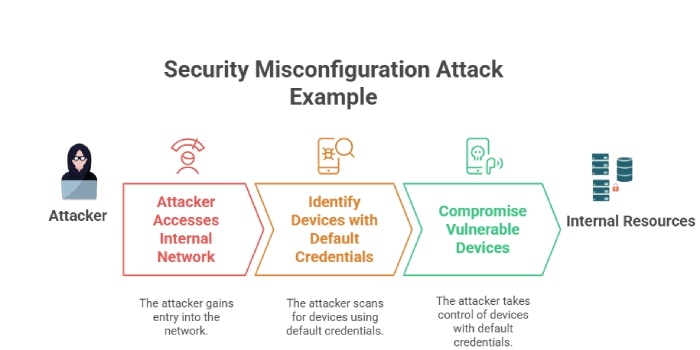
The products protect the users on all ends without requiring other actions on their behalf for proper security. As per Secure by Default, by setting secure configuration settings as the default, users do not have to adjust settings to ensure security manually. Secure by Default outlines that the details or complexity of an organization’s security configuration should not be left to the customers, and organizations should incorporate the best security configurations by default.
Secure by Default emphasizes the importance of strong passwords, data encryption, and network access control. By adopting Secure by Default principles, organizations can control the risk of security breaches caused by user error or misconfiguration. Secure by Default is an approach that will improve the security of an organization’s offerings and minimize the likelihood of cyberattacks.
What are the Benefits of Secure by Design and Secure by Default?
The benefits of adopting Secure by Design and Secure by Default principles are numerous.
By building security into products and systems from the outset, organizations can minimize the need for costly security measures down the line. On the other hand, by setting secure configuration settings as the default, users do not have to adjust settings manually to ensure security, reducing the risk of misconfiguration.
Adopting Secure by Design and Secure by Default principles also helps improve customer trust. By prioritizing security in product development, organizations can demonstrate their commitment to customer data and reduce the likelihood of security breaches. To further put these strategies into practice, product management software can help embed security checkpoints directly into the development lifecycle, ensuring consistency and accountability.
These strategies will take care of the risk of cyber attacks at every stage of manufacturing to protect the organization and allow organizations to take responsibility for user security so smart security decisions are not left to a layman who does not understand how grave a cyber threat is.
Challenges of Secure by Design and Secure by Default Policies
While the benefits of adopting Secure by Design and Secure by Default principles are clear, organizations may face challenges in implementing these policies due to two significant challenges:
- Security Education: One of the main challenges will be educating developers and users on the importance of security. Organizations must ensure developers understand the importance of building security into products and systems from the outset. They must also educate users on how to use the product or system securely.
- Implementation Costs: Another challenge is implementing Secure by Design and Secure by Default principles. Organizations may need to invest in new technologies or hire additional staff to implement these principles effectively. As security will be prioritized at every development stage, it might increase the initial costs of developing a product or service.
Final Words
Cybersecurity threats are ever-evolving and becoming increasingly sophisticated, with a new cyberattack occurring every other day. Reacting to security breaches is becoming challenging and putting pressure on organizations struggling to prevent these from happening.
These new design principles with CISA are a step in the right direction as long as organizations follow them enthusiastically instead of cutting corners and skimping cybersecurity checkmarks. How organizations will incorporate these and what impact Secure by Design and Secure by Default will have on cybersecurity is a question that the future will answer.